German COVID-19 Task Force Targeted by Phishing Actors
- Phishing actors are actively targeting the global medical procurement supply chain.
- Germany is heavily targeted right now by what seems to be Russian actors' work.
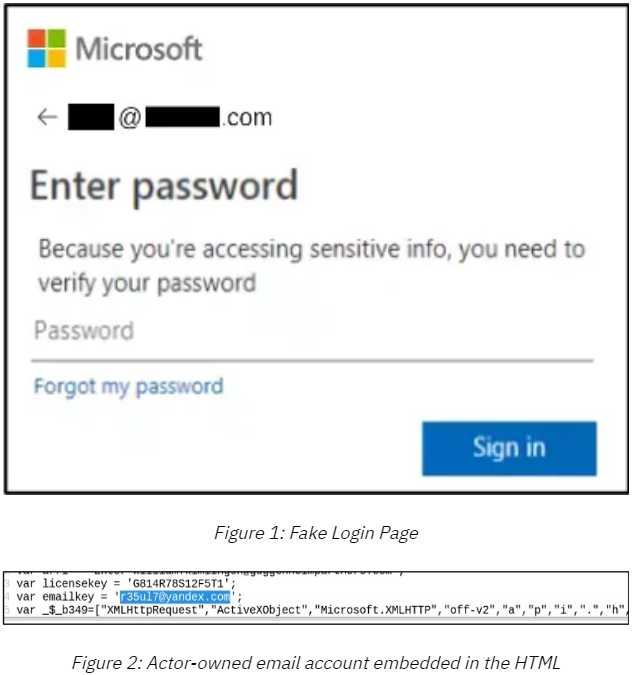
- The actors are phishing executives via fake MS login pages and use the credentials to enter the corporate networks.
According to a report by IBM X-Force Incident Response and Intelligence Services team, the German task force called to deal with the COVID-19 outbreak right now is being actively targeted by phishing actors. The task force consists of the governmental and the private sectors’ cooperating entities and focuses on the procurement of personal protective equipment (PPE) like face masks and gloves. More than a hundred high-ranking executives and managers working in these organizations have already been targeted by the phishing actors who try to exploit the emergency and the reduced security that comes with it, mostly to break inside corporate systems by stealing user credentials.
The IBM researchers have figured that the actors are most likely Russians, as the URLs used in the campaign are tied with “178[.]159[.]36[.]183,” a Russian-based IP. Half of the target email addresses belong to executives who engage in the departments of operations, finance, and procurement belonging to the target corporation. The other half concerns executives of third-party partners who do business with the German task force at the moment, and are mainly US and Europe-based chemical manufacturing, pharmaceutical, finance, and communications firms.
Source: securityintelligence.com
The phishing happens through a Microsoft login page that looks a lot like a genuine one, but exfiltrates whatever credentials are entered in the boxes to “[email protected].” The use of a Yandex email address is another indication that the actors are Russian. By stealing these credentials, the actors are then free to roam in corporate networks, move laterally, or even launch BEC (business email compromise) attacks against other employees in the organization.
Besides the direct network compromise, the actors could hope to divert payments for the procurement of PEE, as this would be a very lucrative scenario for them. There’s a global race for resources, and most countries are looking to secure large numbers of face masks from Chinese manufacturers. These buying and importation national programs are working on an exigent and urgent basis that doesn’t leave a comfortable time margin for confirmations. This is what the actors are exploiting right now, and Germany is one of the most active and aggressive players in that race. Admittedly, it’s not the only target of phishing, but the particular operation is still ongoing at the time of writing this. The German task force needs to be extra careful about how they handle their communications with their procurement partners, and other countries should take note of all that is going on.