German Bank “OLB” Loses €1.5 Million from Fraudulent Withdrawals
- A German bank has suffered a cloned card withdrawal attack originating from Brazil.
- The attackers withdrew €1.5 million from 2,000 accounts, which have been refunded by the bank.
- Cloned card attacks are getting streamlined, rise in number, and get harder to detect and stop.
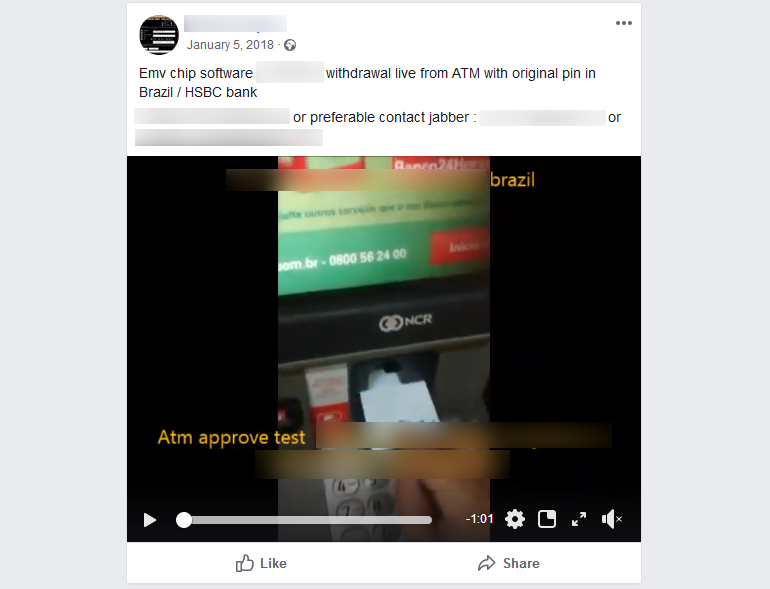
As reported by ZDNet, the Oldenburgische Landesbank has discovered that a group of actors in Brazil withdrew about €1.5 million by using cloned debit cards. More than 2,000 accounts were affected by this incident, and all of the cards associated with them are Mastercard debits protected by the chip-and-PIN technology. The German bank refunded the amounts that were withdrawn from its clients’ accounts and stated that they discovered no security breach that could have compromised the particular set of payment cards. Right now, they are issuing replacement cards for their clients, hoping that this will be the end of the story.
As we discussed back in July, there are thousands of credit cards that are compromised every day. Crooks either use this information to create clone cards themselves or sell it to someone else who will do it on their own. The tools that are needed for the job include an encoder that will load the stolen data to the magnetic stripe of a blank card, and an embosser that will etch the name of the real account holder and the credit card number onto the plastic. This is all that’s required for ATM withdrawals, which is exactly what a Russian-speaking group of hackers achieved in Cyprus two months ago.
Brazil is considered to be a hotspot for card cloning, along with Mexico, as similar attacks have stemmed from there numerous times in the recent past. Cyber-criminals from Brazil don’t hesitate even to advertise their ability to create working credit and debit clone cards, selling their services to those who are interested. The worrying part is that the trend of these attacks is on the rise, with ATM sniffers and POS malware stealing the required card data more massively than ever before.
Source: zdnet.com
As we have seen recently, cyber-criminals are even selling POS malware such as “GlitchPOS” and “DiamondFox”, both of which are capable of stealing credit card data from compromised payment platforms. To make the situation worse, the actors have found a way to create cloned cards that don’t even need a valid PIN to work. Instead, they can accept any random PIN that is entered on a POS or ATM terminal. All of this combined has expanded the exploitation potential and has rendered card cloning into a reliable and profitable attacking method that is getting gradually more and more streamlined.
Have you ever fallen a victim of a debit card cloning attack? Share the details with us in the comments down below, or on our socials, on Facebook and Twitter.