‘G Buddy – Smart Life’ Android App Carries Windows Malware
- A Chinese smartwatch app for Android was found to contain malware that targets Windows systems.
- The app was removed, cleaned, and re-uploaded, so it was likely a case of a supply chain infection.
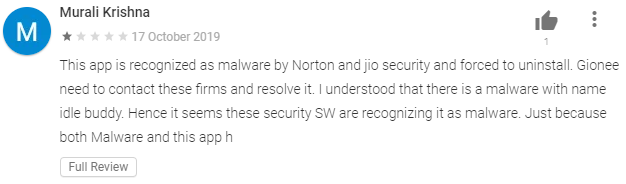
- Many AV tools for the Android platform detect and mark the app as malware.
Researchers at Quick Heal Labs have discovered that a smartwatch configuration app for the Android platform is actually carrying Windows malware. The app is named 'G Buddy – Smart LIFE,' and it's meant to accompany the Gionee SmartWatch, connecting with the wearable, fetching data, and visualizing it. At the time of writing this, the app is available on the Google Play Store, having an average user rating of 3.6, which mostly comes from bugs and performance issues. However, there are quite a few that also report that they are getting warnings about malware risks. All in all, the score shows that the Chinese developers of the app haven't done a diligent job, really.
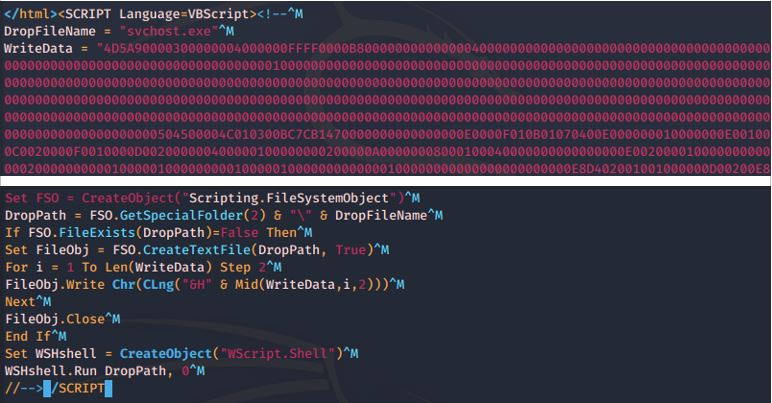
The researchers have analyzed a bunch of HTML files that are generated as assets inside the APK folder and noticed a suspicious VBScript code snippet at their end. Upon further analysis, this code was found to be an encoded Windows executable, whose purpose is to drop a payload named "svschost.exe" and send an execution call. Of course, all that can't be triggered on Android, and can't be propagated through anything else other than EXE, DLL, and HTML files. This was the case with version 1.0.11, which was reported to Google upon discovery, on February 20, 2020.
Source: Quick Heal Labs Blog
Google has removed the malware-ridden version of the 'G Buddy' app and informed the developer, who cleaned their code and then re-uploaded the app. This was most probably not an act of the app developers, but of hackers who managed to compromise their development tools. Thus, this is a typical case of a supply chain attack. While the risk for Android was non-existent, the code could have caused harm to other platforms if it somehow found its way there. In any case, incidents like this one highlight the negligence of the developers and make it harder for users to trust their products.
Source: Google Play Store
That is especially the case when users are getting warnings about the 'G Buddy' app being malware from the mobile security solutions that they're using. It is encouraging to see that many Android AV engines are still checking for malicious code meant to run on other platforms, and, at the same time, it's awkward to realize that somehow the checking systems of "App Defense Alliance" aren't. Google has a dedicated category for "Non-Android" threats, so it should be capable of detecting them and displaying the relevant warning message to the users nonetheless.