Researcher Uncovers Four Android VPN Apps that Serve Disruptive Ads
- Four VPN apps are engaged in nasty, disruptive advertisement serving techniques.
- All of them use the Google advertisement API, which makes it possible to serve ads at any time.
- One of them has a staggering userbase of 500 million people, and it goes a bit easier in the serving.
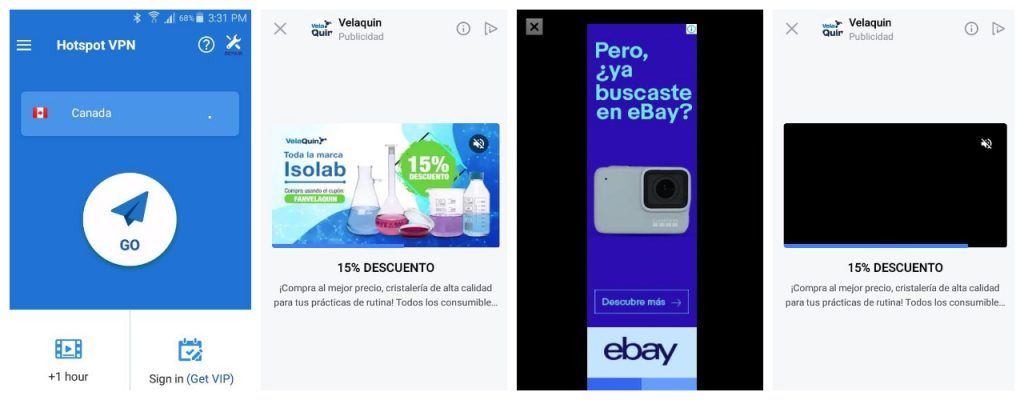
Security researcher Andy Michael warns about a group of four VPN apps for the Android platform which are serving their users with disruptive ads. The apps are “HotSpot VPN” by HotspotVPN 2019, “Free VPN Master” by Freemaster2019, “Secure VPN” by Sec VPN, and “Security Master” by Cheetah Mobile. In total, the four apps count more than 500 million downloads and installations, two of them have nearly identical code, and all of them were created by Chinese developers (including Hong Kong). All of these apps are available on the Play Store at the time of writing this piece.
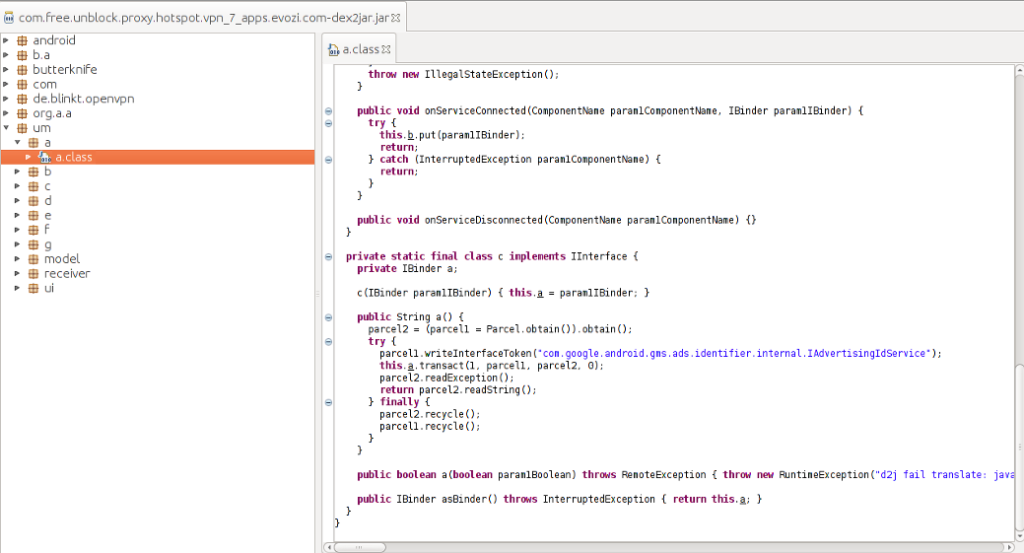
Starting with Hotspot VPN, an app with half a million users, the researcher noticed some level of code obfuscation which is always suspicious. The app is using the advertisement API from Google, which means that it can serve ads at any time it wants. The Facebook API was also present in the app. The host device screen resolution is grabbed for ad-serving purposes, so when the intrusive ads land, they cover the whole screen of the device. The case with Free VPN Master was similar, as the 1 million users app is also deploying the Google advertisement API, which the code structure and contents were the same as the one in Hotspot VPN.
Source: vpntesting.com
Secure VPN, which has 1 million downloads, the ad-serving action is a tad more sophisticated. Here, the app monitors the user's activities and tries to display ads that are relevant. This app uses multiple ad APIs, including the Google one, and considers the user’s country, region, time, etc. The researcher also noticed that it has the right to read and write logs on the SD card, but he found no evidence of that happening.
Source: vpntesting.com
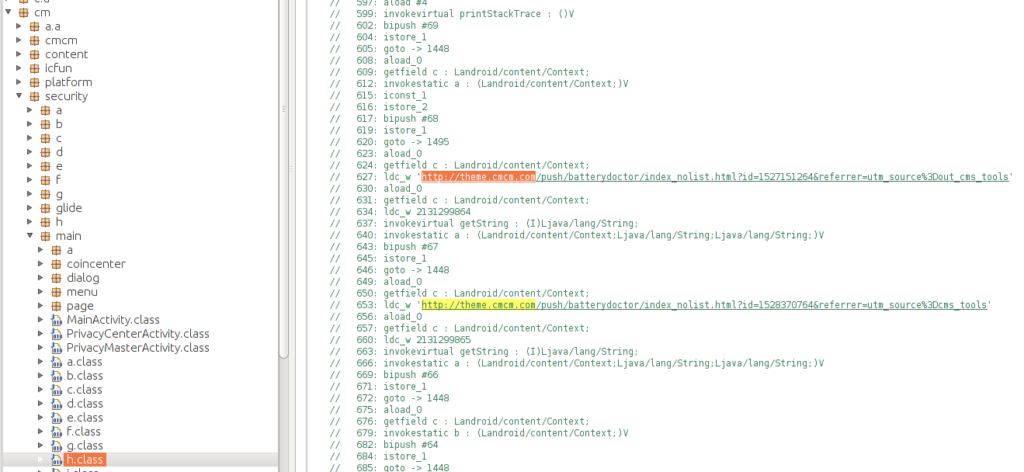
Finally, there’s the big haul of 500 million users that come with Cheetah Mobile’s Security Master, which has an excellent user review score of “4.6”. According to the researcher, there are functions in the code of the app that relates to the displaying of ads, when to do it, and how to evaluate properties in connection to this activity. The researcher tested out some URLs that he found hard-coded in code classes which were ads. Moreover, he found the Facebook advertisement API, along with those from Google, Airbnb, Unity3D, GitHub, and even more. Security Master is not serving intrusive and disruptive ads all the time but instead does it more infrequently, to avoid being too annoying for its massive userbase.
Source: vpntesting.com
Are you using any of the apps above? Can you confirm the researcher’s claims? Let us know in the comments down below, or on our socials, on Facebook and Twitter.