American Soldiers Expose the U.S. Nuclear Missile Bunkers Secrets in Europe Through FlashCard Apps
- American soldiers serving in Europe-based nuclear bunkers exposed extremely sensitive information through FlashCard apps.
- The personnel used these apps to learn complex security procedures, but somehow, they made this data public.
- The exposed details include the location of the bunkers, the weaponry, the location of cameras, universal codes, and more.
Flashcard learning apps are great for improving visual memory, helping you learn new processes, and mentally conquer complex procedures through spaced repetition. This is why American soldiers being in charge of the security and operation of nuclear missile bunkers in Europe have been using apps of this kind extensively, as they need to come to grips with lengthy and complex security protocols that underpin their daily work. However, they are putting extremely sensitive secrets at risk by doing so, and according to a Bellingcat report, the damage has already been done.
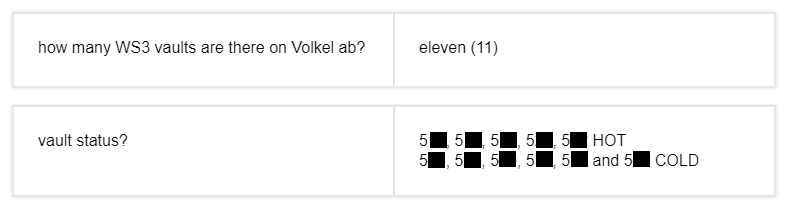
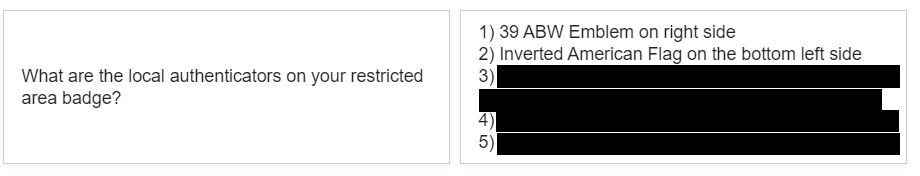
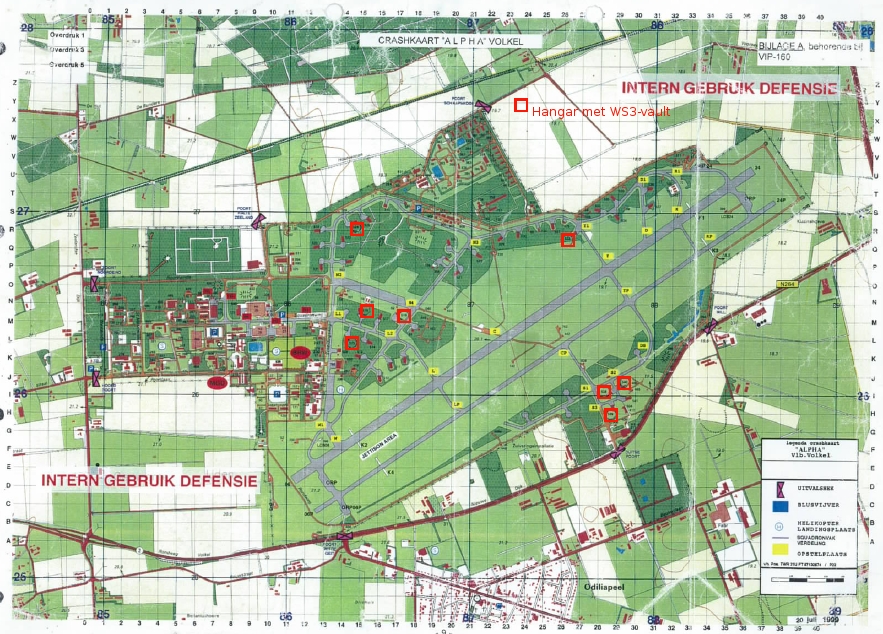
As investigative journalist Foeke Postma details, the flashcards that the soldiers create for training purposes are retrievable by anyone, and in fact, it appears that Google Search is indexing them. The reporter found them online by searching military jargon terms and abbreviations, trying to find evidence of bunker locations and operational status. By searching for “PAS,” “WS3,” and “vault” together with names of air bases in Europe, he was surprised to see results from flashcard platforms like Chegg, Quizlet, and Cram.
The information found in these cards includes the exact locations of the bunkers, which officially remains a secret, whether or not they are “hot” or “cold,” meaning if they have nuclear heads at the location and even details about the security protocols that apply at each base. Some flashcards even detailed the number of security cameras and their exact positions, radar systems, sensors, the location of keys to aircraft shelters, location of backup generators, universal release codes that open all vaults, and a lot more.
It is unclear how exactly this information became public and indexed by Google, but it may have to do with the privacy settings on the flashcard apps. If the cards are created with public visibility set to “on” (which is the default setting on many of these apps), then they are meant to be shared with the entire community. It is also possible that these platforms' data privacy and security level aren’t up to par, and soldiers working on such critical locations shouldn’t have trusted them no matter the settings and policy promises. If only the U.S. Army had provided its own flashcard app for soldiers to use, this “flagrant breach” could have been avoided.
Due to the extreme criticality of this exposure, Bellingcat contacted NATO, EUCOM, and the U.S. DoD four weeks before this story went public, allowing them the time to take the appropriate actions. And with the confirmation on the existence of multiple B61 missiles spread across Europe, the anti-nuclear weapon debate in the continent has now been reignited.