Flash May Be Dead, but ‘Shlayer’ Campaigns Are Still Using It as a Disguise
- Distributors of the ‘Shlayer’ malware are still tricking macOS users with fake Flash Player update notifications.
- The installation is finalized manually by the victim and takes place while hidden in the background.
- Shlayer has been a constant pain for macOS users ever since its first appearance three years ago.
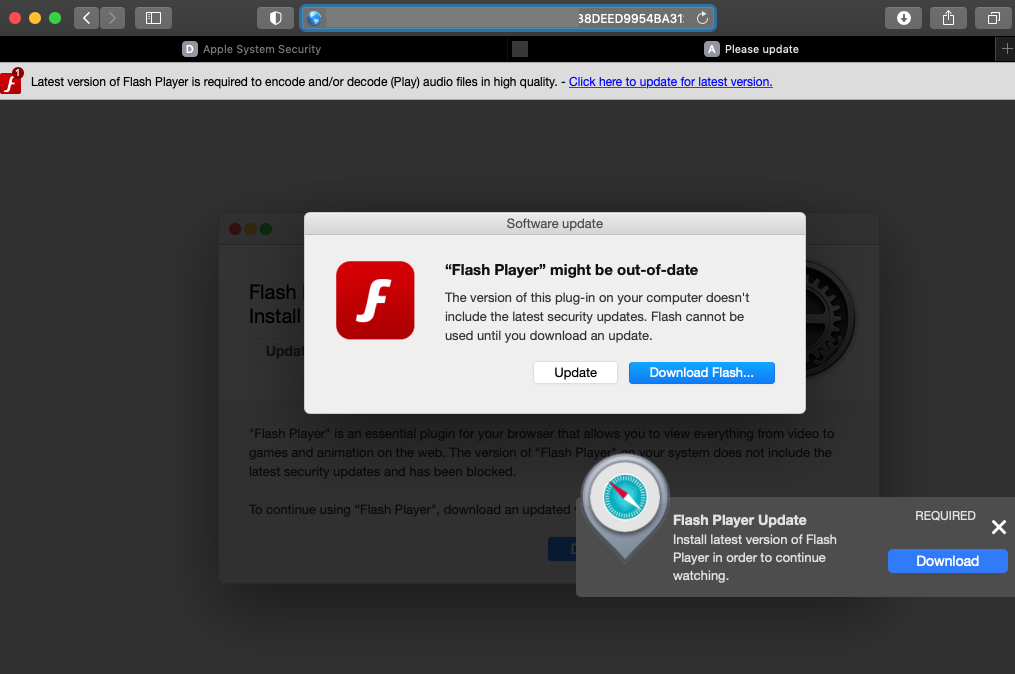
Adobe announced the end of support for the Flash Player on December 31, 2020, all major browsers uprooted it even earlier, and users should be already aware of the fact that Flash isn’t a thing anymore. However, malware actors are still abusing the name. This tells us the old method still works well enough, not creating an incentive to change to a different theme. As reported by Crowdstrike, distributors of the ‘Shlayer’ malware for the macOS are still masquerading their software as a Flash update.
‘Shlayer’ has been around since 2018, and it is currently the most common type of malware targeting macOS systems. Ever since its humble beginnings, Shlayer used fake Flash updates to trick its victims into installing it on the Safari browser. This opened up a host of opportunities for the actors, as Shlayer can pass all user network traffic through an actor-controlled proxy server, essentially allowing the hackers to access sensitive data.
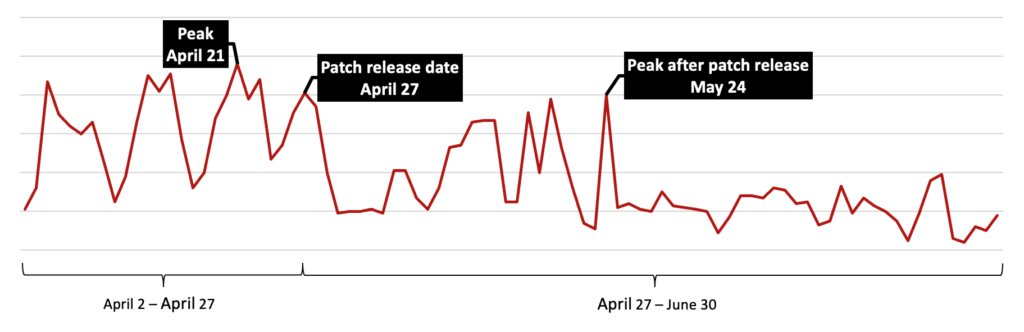
Multiple actors are using Shlayer for their own malicious purposes, while the malware authors are constantly maintaining and evolving the tool to use new bypasses and new zero-days. Each time a new trick was added, Crowdstrike recorded spikes in the infection numbers, and every time Apple released a fixing patch for the macOS, the numbers went down significantly.
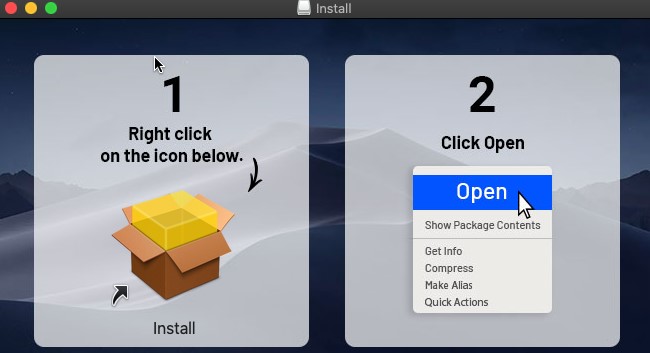
The notable aspect in Shlayer’s distribution is that a fake alert of the Flash Player being supposedly out of date and needing an update is still the prominent method of social engineering. If the user is convinced of the fact and clicks on the update popup, Shlayer is downloaded and mounted on the victim’s machine. For the installation step, which the victims have to carry out on their own, a step-by-step guide is offered to create a sense of legitimacy, as well as to ensure that everything will go as planned.
The actual installation takes place in the background. It involves hidden folders, temporary directories, scripts to decode the AES commands, substitution ciphers, immunity to hangup signals, independence to user log-offs, clearing quarantine flag to bypass Gatekeeper, and finally, the termination of all these processes. The end result is a nasty adware infection that gradually leads to fetching more payloads, usually also adware.
The main takeaway here is that if you’re ever met with a request to update your Flash Player, it’s malware attempting to nest in your computer. Flash is gone, and there’s no service or video platform requiring it anymore.