FIN7 Hackers Spread Infostealers via Fake AI-Powered Nudes-Generating Websites
- FIN7’s latest malware campaign leverages public interest in AI tools that turn pictures into nudes.
- The threat actor promotes online and Windows tools that only deliver infostealers.
- Among the malware strains are the notorious Lumma Stealer and Redline Stealer.
The notorious Advanced Persistent Threat (APT) group FIN7 launched a new campaign that exploits public interest in AI-powered deepfake nudes via a network of fake websites claiming to offer deepfake nude generators that distribute information-stealing malware instead, according to recent reports.
The group uses black hat SEO tactics to enhance the visibility of these malicious websites in search engine results, thereby increasing the likelihood of victim engagement. By capitalizing on controversial and often illicit interests, the threat actor lures unsuspecting users into downloading malware under the guise of AI-generated content.
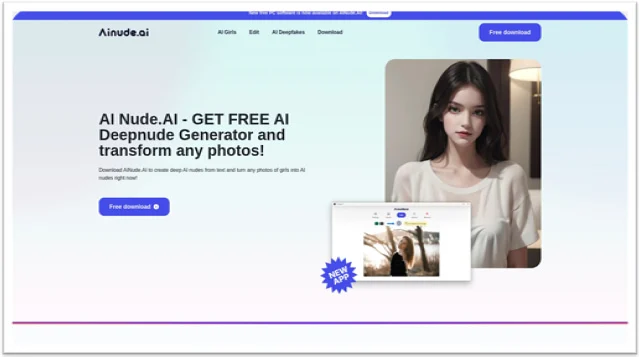
Silent Push research identified several websites directly operated by FIN7, such as "aiNude[.]ai" and "nude-ai[.]pro," which entice users with "free trials" or "downloads." These either claim to generate fake nudes from user-uploaded pictures or promote a deepnude generation program for Windows.
However, these downloads contain Lumma Stealer, Redline Stealer, and D3F@ck Loader malware, which target sensitive data, including credentials, cookies, and cryptocurrency wallets.
The cybercriminals’ honeypot websites allow work by allowing users to upload photos to be turned into deepfake nudes. The image that is supposed to be generated is not displayed on the screen, and users are prompted to use a download link instead.
The URL redirects to another site where the victim sees a link for a password-protected Dropbox archive and the required password, and the download only includes the malware.
FIN7 is also employing parallel tactics by distributing NetSupport RAT through deceptive browser extensions. Furthermore, the group utilizes trojanized installers masquerading as legitimate software from well-known brands like Zoom and Fortnite to deliver malicious payloads.
FIN7's evolving methods and recent campaigns illustrate an alarming trend of leveraging societal interests and emerging technologies, such as AI and deepfakes, to advance their cybercriminal agenda.
In recent news, several infostealer developers have announced their malware shows successful bypasses for Chrome's cookie-theft protections, and these include MeduzaStealer, Whitesnake, Lumma Stealer, Lumar (PovertyStealer), Vidar Stealer, and StealC.