FIN7 Bolsters Ransomware Threats With New Recruits
- The FIN7 group, notorious for PoS payment card fraud, has been recruiting employees under a fake company.
- The group has been actively recruiting IT experts like system admins and reverse IT engineers in Eastern Europe.
- The detailed investigation on the group and its updated ransomware attack tactics has been corroborated with the Microsoft presentation at Mandiant Cyber Defense Summit 2021.
FIN7, a cybercriminal group first seen in the mid-2010s, has been noticed attempting to recruit low-wage IT-skilled talent from Eastern Europe via a new fake company titled Bastion Secure, promising a salary between $800 and $1,200. The group had previously been fronting its cybercriminal activities with another fake company titled Combi Security. The new report is based on information gathered by a source who was recruited by this group, and the findings have also been included as part of the Microsoft presentation at Mandiant Cyber Defense Summit 2021.
They had set up what seemed to be a legit website at first glance on Google in case prospective employees checked them out, but it was actually copying a legitimate business called Convergent Network Solutions Ltd. The domain used a Russian host named Beget, which is often utilized by cybercriminals. The company lists its offices in the UK, Tel Aviv, Moscow, and Hong Kong, but none of the company registry indexes in those cities have the company name entered officially on their books.
The source working with Gemini Advisory said that as part of their recruitment test at FIN7, they got access to key files linked with post-exploitation tools Carbanak and Lizar/Tirion and became part of a ransomware attack team. Using the data derived from the exposure, Gemini Advisory was able to discover the new fake company fronted by FIN7.
The group was using a three-stage process to hire IT experts with skills in C++, Python, and PHP, and system admins and reverse engineers. The process seems authentic, except in some places where the tests require applicants to focus on file systems and backup signals, which imply they are interested in fielding IT experts to bolster their ransomware attacks as opposed to their previous strategy of PoS infections.
The idea here is to use professional system admins with legit credentials to help map out a systems network, sometimes even during the hiring process, either via phishing attacks or outright dark web purchases. After that, the group could execute a ransomware attack and hold the compromised system’s owners and their data hostage until they are paid.
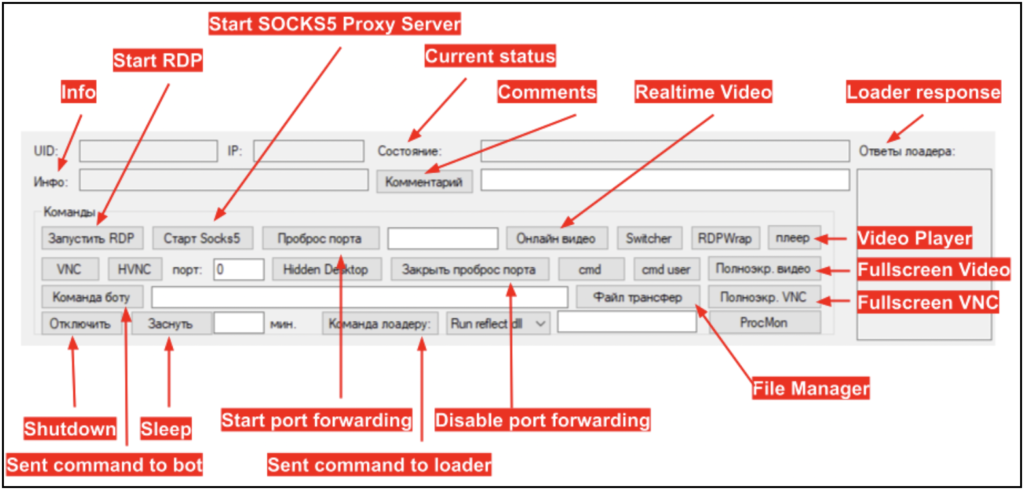
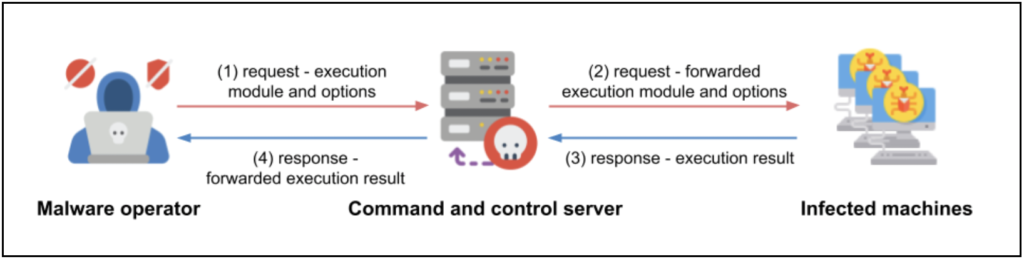
The file set for recruitment with Bastion included a software component titled “Command Manager,” which was, in fact, the client component of Carbanak. This application is used in collecting data on infected devices for gaining remote access operated via PowerShell scripts to launch the Lizar/Tirion injector and payload. This loader receives periodic commands via the C&C server and launches commands modules in .dll, .exe, and .ps1 file types. The purpose here is to monitor user activity and prepare for the eventual ransomware attack.
Gemini Advisory has been investigating this group and working with law enforcement to monitor FIN7’s activities, which began its cybercriminal career trying to compromise point-of-sale systems. The group had been using REvil or Ryuk ransomware to perpetrate its standard PoS attacks to extract payment card details.
FIN7 and similar groups are always looking for legitimate skilled IT professionals to front their fake companies. This group stands out for the marked overtness with which it operates and the deceptively sophisticated underpinning of all its cybercriminal operations. IT experts and companies operating in the cybersecurity market are advised to maintain discerning caution when engaging with such suspicious actors.
In the past 10 years, FIN7’s carding campaigns compromised 20 million payment card records and stolen a cumulative $1 billion, making the group one of the most successful during that time. Despite the arrest of one of its chief administrators in 2021, FIN7 continues to operate in the ransomware domain and poses a huge threat through its activities.