FamousSparrow Returns with Two New Versions of Their Signature SparrowDoor Backdoor
- China-linked APT FamousSparrow re-emerged after three years of inactivity.
- The threat actor has two previously undocumented versions of its specific backdoor.
- Security researchers identified overlaps with other APTs, such as Earth Estries, APT41, and Salt Typhoon.
FamousSparrow, a China-linked advanced persistent threat (APT) group previously thought to be inactive since 2022, is back in business with two previously undocumented versions of the group's signature backdoor, SparrowDoor.
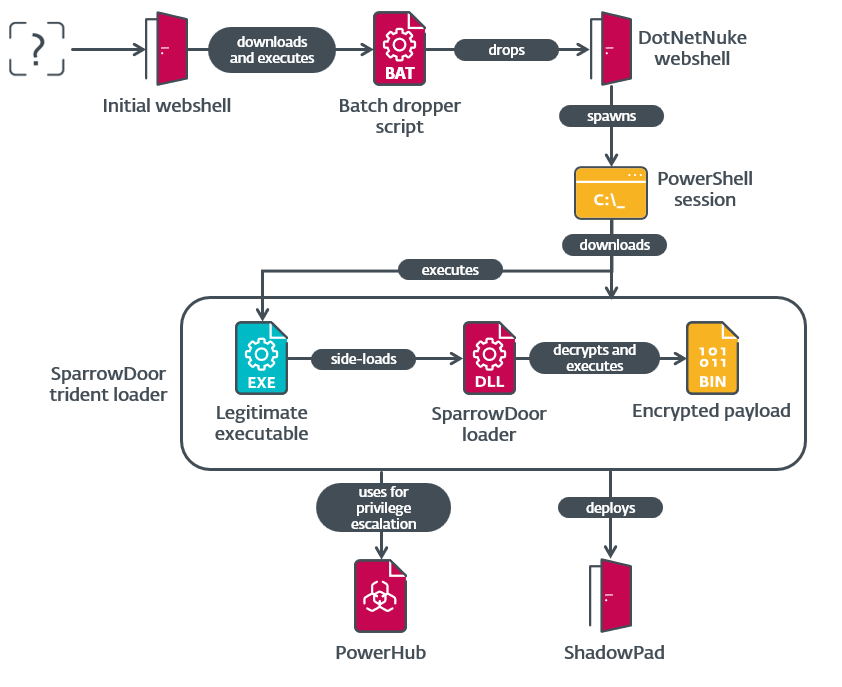
The hallmark of this campaign was the discovery of two advanced versions of SparrowDoor by ESET researchers These versions represent considerable improvements in code quality, architecture, and functionality.
While FamousSparrow’s activities overlapped with groups like Salt Typhoon and Earth Estries, ESET researchers maintain that FamousSparrow remains distinct.
One version shares design similarities with CrowDoor, a backdoor linked with Earth Estries, another APT group, and acts as a TCP proxy between the command and control (C2) server and an arbitrary machine.
The other, a modular variant, only implements the commands related to C2 configuration management and uninstalling the backdoor, adding a list of installed security products when exfiltrating host details.
For the first time, FamousSparrow was also observed utilizing ShadowPad, a backdoor exclusively available to Chinese-aligned threat actors like APT41. This marked a significant collaboration in methodologies among nation-state-backed cyber threat groups.
Overlaps, such as shared infrastructure and similar tactics, may suggest coordination via a central "digital quartermaster" rather than direct links between the groups.
FamousSparrow continues to rely on a blend of custom tools and shared malware. Key methods observed include:
- Exploit Webshells – Webshells were deployed on compromised servers running outdated Microsoft Exchange and Windows Server installations.
- Privilege Escalation – Leveraging the “BadPotato” exploit within the PowerHub framework to gain SYSTEM-level privileges.
- SparrowDoor Deployment – Using multi-stage loaders, SparrowDoor infiltrates networks with encrypted communications and modular capabilities for adaptability during exfiltration.
- ShadowPad Integration – Leveraging side-loading techniques to execute ShadowPad, further enhancing its capabilities for espionage.
The renewed activity was discovered in July 2024 when ESET responded to a cybersecurity incident affecting a trade group in the U.S. financial sector. Further investigation revealed that FamousSparrow had also breached a research institute in Mexico during the same campaign.