FakeCall Android Trojan Improves Espionage Capabilities and Evasion Tactics
- The FakeCall Trojan for Android was seen displaying improved functionalities and architecture.
- With new, advanced evasion and espionage capabilities, the Trojan now stealthy intercepts and manipulates user communications.
- The enhancements help the malware remain undetected by traditional security tools.
The FakeCall Android Trojan, notorious for targeting South Korean users with its vishing tactics, has evolved with enhanced architecture and functionalities and advanced evasion and espionage capabilities, deploying sophisticated tactics to intercept and manipulate user communications, which makes detection by traditional security measures increasingly difficult.
According to recent research by Zimperium’s zLabs, the malware begins its attack vector through traditional phishing techniques, tricking victims into downloading an APK file that acts as a dropper for FakeCall. Once installed, it communicates with a command-and-control (C2) server, executing various commands under the guise of a legitimate interface.
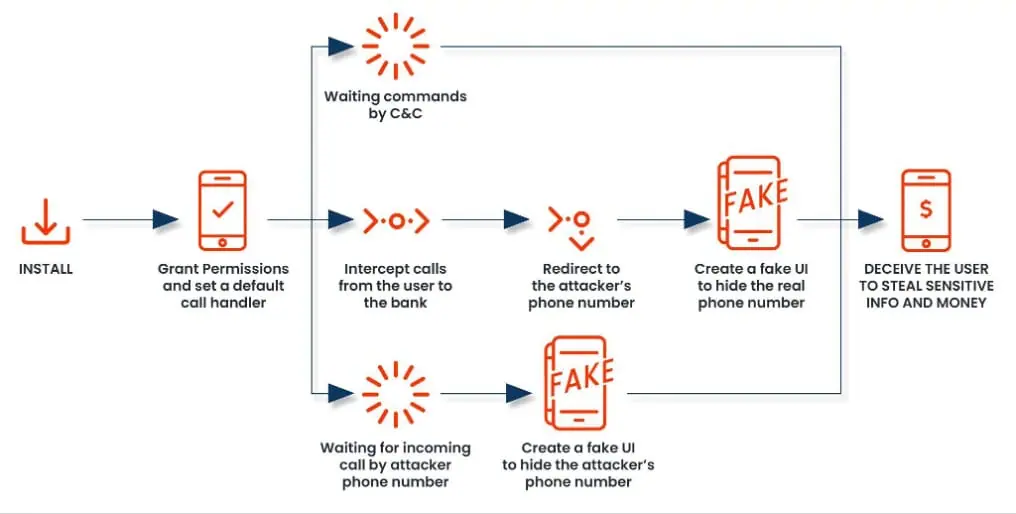
Its primary aim remains to redirect financial calls to attacker-controlled numbers, extracting sensitive information under the pretense of real banking interactions.
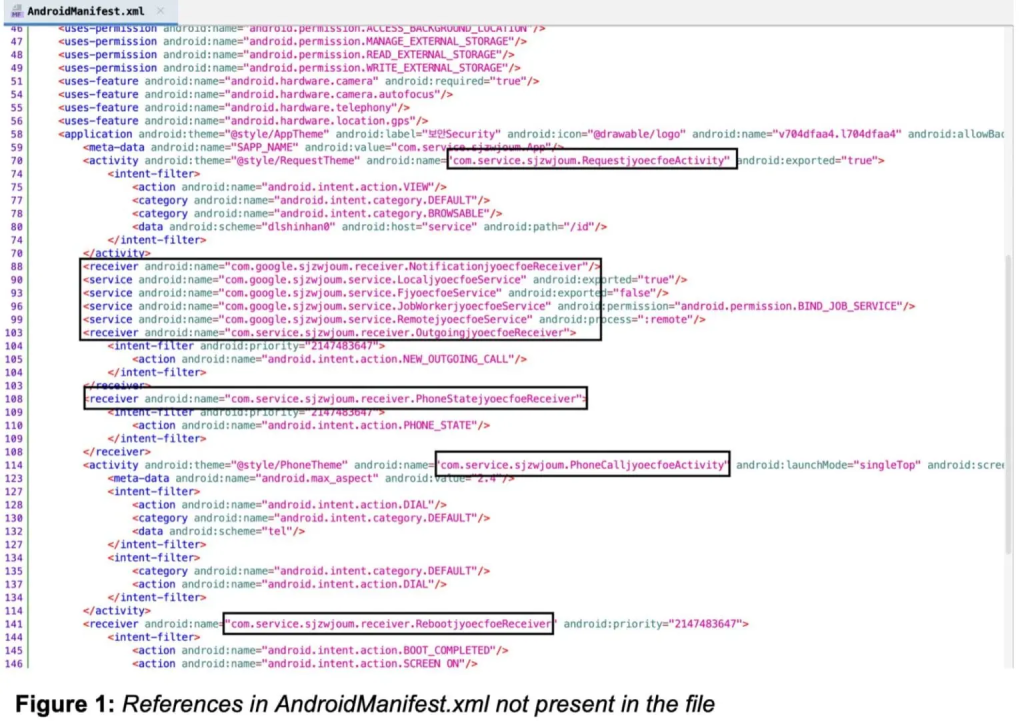
Recent analyses reveal discrepancies between declared activities in the app's manifest and those found in the decompiled code, showcasing a strategic shift to migrate malicious functionalities partially to native code.
This includes advanced obfuscation techniques, remote surveillance, and expanded espionage capabilities, such as the ability to disable Bluetooth and simulate user actions on the device, enhanced phone listener service for seamless communication with C2 servers, and the capability to intercept and manipulate call interfaces, presenting convincing fake UIs to the victim.
Zimperium's report aligns these tactics with MITRE’s ATT&CK Framework, emphasizing the sophisticated evasion strategies employed by FakeCall. Despite no specific attribution, the malware's techniques resemble those observed in state-sponsored campaigns.
The evolving nature of FakeCall and its capabilities to hijack user interfaces and exert remote control highlight the growing complexity of modern cyber threats.
In other recent news, compromised WordPress websites were observed displaying a fake issue to lure victims into installing Remote Access Trojans on their machines, which contained the RedLine Stealer malware.
In August, attackers lured users with fake download sites looking like Roblox FPS Unlocker, YouTube, VLC, or KeePass to distribute Trojans that install malicious web browser extensions and steal sensitive user data.