Fake Zoom Installer Deploys BlackSuit Ransomware in Enterprise-Targeted Attack
- Hackers targeted enterprise networks with BlackSuit ransomware via a trojanized Zoom installer.
- They used a Pascal loader with embedded URLs that pointed to OneDrive, Telegram, Steam, and more.
- The attack included the deployment of the SectopRAT malware to drop a Cobalt Strike beacon and a Brute Ratel Badger.
A cybersecurity incident involved attackers exploiting a counterfeit Zoom installer to initiate a series of malicious activities, culminating in widespread BlackSuit ransomware deployment across enterprise networks.
The attack began with a fake installer downloaded from a malicious website masquerading as the legitimate Zoom platform, as a case study detailed by The DFIR Report says.
The installer, developed using the Pascal-based d3f@ckloader, served as the entry point for a sophisticated multi-stage malware attack, which included zip/cmd files, executables, and URLs. The embedded URLs pointed to OneDrive, Telegram, Steam, and platforms.
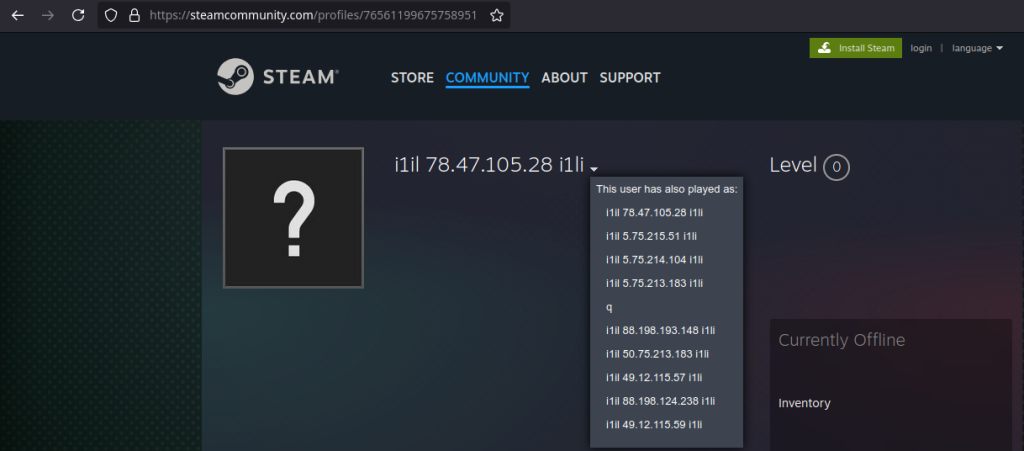
In the first stage of the operation, the malicious installer executed scripts to manipulate Windows Defender exclusions and connected to online platforms (e.g., Steam Community) to retrieve second-stage payloads.
In stage two, the attackers deployed SectopRAT malware, which established command and control (C2) communication via Pastebin. The Remote Access Trojan (RAT) remained dormant for eight days before resuming its attack.
The third stage occurred on Day 9 when the payload initiated Brute Ratel (commonly known as Badger) and Cobalt Strike frameworks for lateral movement, credential access, and system discovery.
The threat actors demonstrated an impressive range of evasion and execution tactics, including the use of batch scripts to hide files and manipulative commands to obscure their presence from cybersecurity tools.
For extracting credentials from LSASS memory, the hackers used tools like pass-the-hash for privilege elevation, employed proxy tools like QDoor to facilitate tunneled RDP traffic, and leveraged Cobalt Strike PsExec for lateral movement.
Sensitive files were compressed and transferred via the Bublup SASS project management suite.
The final phase involved deploying BlackSuit ransomware across all Windows systems using PsExec scripts. Encrypted files and deleted shadow copies on affected machines were accompanied by ransom notes, rendering victims’ data inaccessible unless the ransom was paid.
The attackers ensured maximum impact by staging ransomware deployment meticulously, backing up necessary tools, and targeting high-value network nodes like domain controllers and backup servers.