Fake ‘Security WordPress’ Plugin Injects Casino Spam, Improving SEO of Attacker’s Website
- A new discovery revealed a fake WordPress plugin hidden in plain sight injected casino spam links.
- The attackers hijacked legitimate websites and inserted spammy links from dangerous portals.
- This increases the search engine results of the attacker’s websites due to the inserted backlinks.
Attackers used fake plugins to insert casino spam, compromising website functionality and search engine rankings. This attack bypasses integrity checks and remains hidden from unsuspecting website admins by mimicking legitimate plugins in the WordPress directory.
The latest reported incident involves spam links related to online gambling being injected into the footer of a WordPress site.
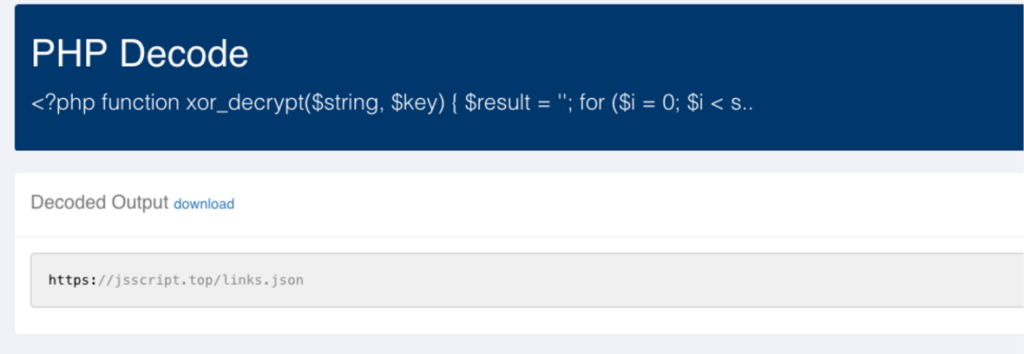
These links are pulled from a malicious URL—“jsscript[.]top”—via encoded scripts contained in the fake plugin named “Security WordPress,” as detailed by Sucuri.
Masquerading as a seemingly harmless plugin, the malicious software avoids detection by using techniques like obfuscation and single-file execution. This ensures that even thorough integrity checks within WordPress fail to detect the malware.
The attack begins with an XOR decryption function that reveals an encoded URL. From there, the plugin uses cURL functions to retrieve external JSON data containing a list of spammy links.
The malware then decodes, shuffles, and inserts these links into the website footer for both visitors and search engine crawlers to find.
Such actions appear to serve three primary purposes for attackers – Black Hat SEO, traffic redirection, and paid link schemes.
The attacker's domains improve their search rankings by creating backlinks from legitimate websites. Users clicking these links are redirected to potentially harmful websites, and attackers may profit from selling these placements to unscrupulous entities.
Another Sucuri report said a compromised WordPress site was manipulated to host spam pages with casino-related links. The malware was concealed using a simple "include" statement within the WordPress theme, referencing a malicious file positioned above the webroot.