Fake Military Apps Try to Steal Login and GPS Data from the Ukrainian Army
- Hackers distributed malicious links to Ukrainian military servicemen via the Signal app.
- They impersonated critical military systems, urging the users to download fake apps.
- The downloads installed malware with credential-stealing and location-exfiltrating capabilities.
Malicious actors are targeting the Ukrainian army with counterfeit military applications designed to exfiltrate credentials and GPS data from soldiers' mobile devices. Two cyberattacks designed to infiltrate the mobile devices of military personnel were identified and neutralized, according to the Ukrainian Computer Emergency Response Team (CERT-UA).
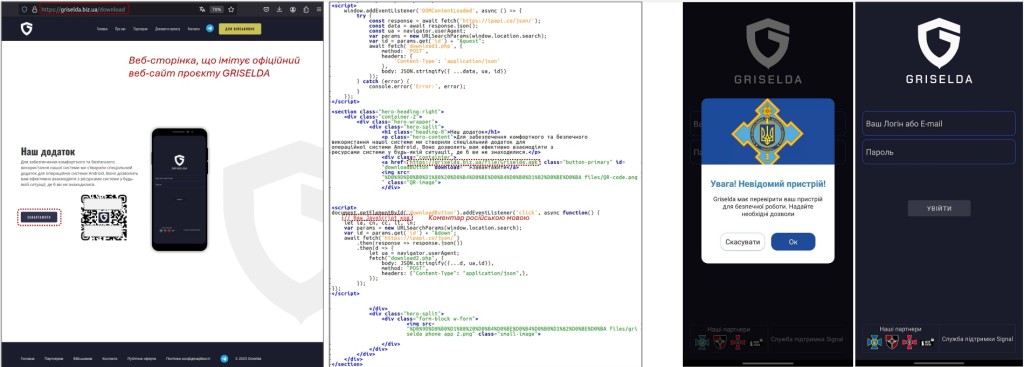
The attackers leveraged the secure end-to-end encrypted messaging app Signal to distribute messages with links to download APK files among military personnel disguised as legitimate apps for critical military systems, including the AI-based GRISELDA system and army tracking system Eyes.
One link opened a copy of the GRISELDA project's official website that offered to download a mobile GRISELDA version, which does not exist. The downloaded APK file was HYDRA malware, which can steal session data, contacts, keystrokes, etc.
The other link was a Google Drive URL that bundled an APK file with the original Eyes program. The malware could steal the user's login credentials and transmit the device's GPS coordinates. CERT-UA assumed the attackers added a third-party JAVA class and implemented its call in the corresponding code blocks of the legitimate program.
The report highlights the need to adopt separate comprehensive measures to ensure the security of mobile devices from cyber threats.
In August, attackers posing as the “Security Service of Ukraine” (SSU) conducted a phishing campaign to distribute malware to the country's government agencies. They used a fake SSU documents archive as a lure and compromised more than 100 computers.
In July, the group tracked as “UAC-0063” carried out a cyber attack against one of the Ukrainian scientific research institutions using HATVIBE and CHERRYSPY malware.