Fake Job Offers Impersonating CrowdStrike Target Developers with XMRig Cryptominer Attacks
- Hackers try to lure developers with fake CrowdStrike jobs via social engineering campaigns.
- The malware can perform anti-debugging and system requirements checks and displays anti-analysis strategies.
- After these checks, it displays a fake error message and deploys the XMRig cryptominer.
A sophisticated phishing campaign exploiting CrowdStrike’s recruitment branding to target developers emerged, deploying the XMRig cryptominer through fake job offers. This operation utilizes deceptive social engineering tactics and advanced evasion techniques.
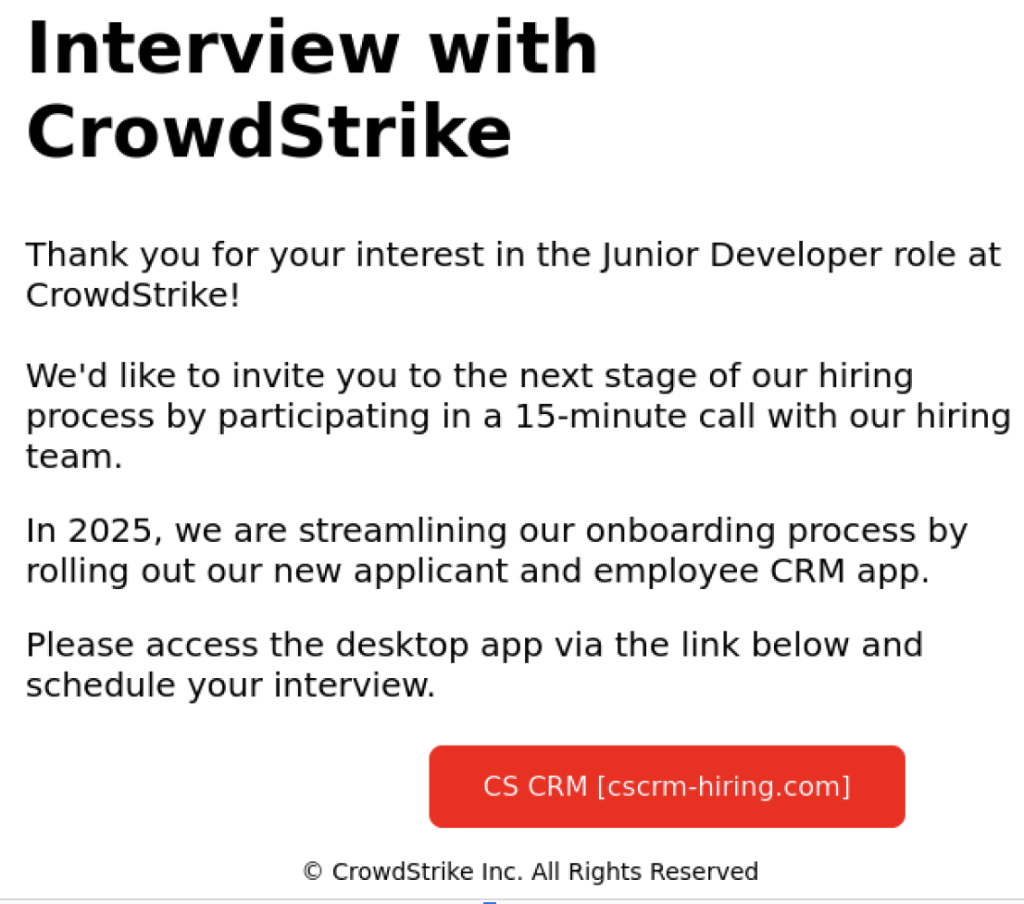
The cybercriminals behind this campaign begin by delivering meticulously crafted phishing emails impersonating CrowdStrike’s hiring process. These emails direct recipients to a fraudulent website designed to closely mimic CrowdStrike’s official recruitment portal.
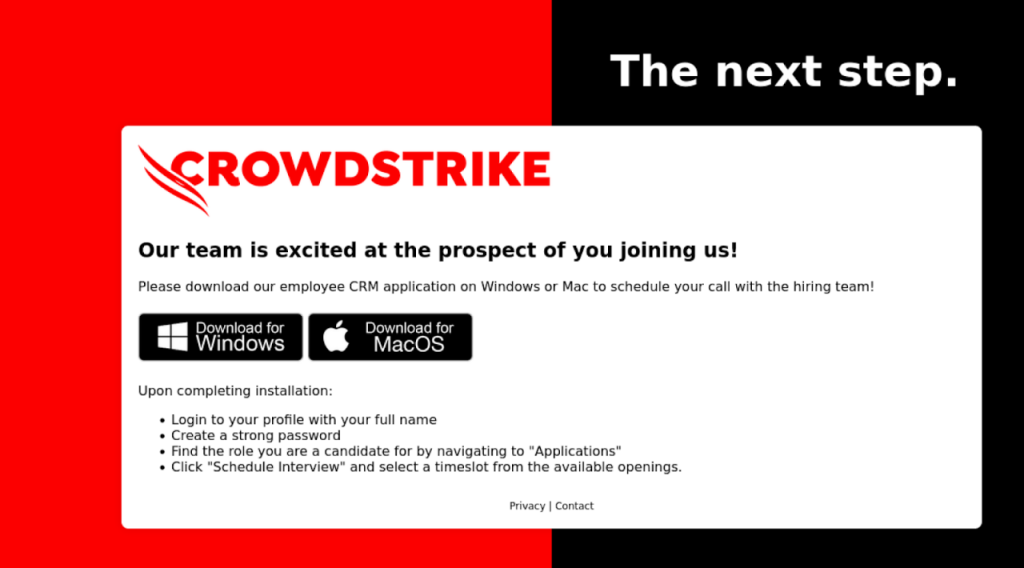
Victims are presented with download options for both Windows and macOS, cleverly simulating a legitimate employee relationship management (CRM) application.
However, regardless of the operating system selected, the victim unknowingly downloads a Windows executable written in Rust.
The dropper uses the IsDebuggerPresent Windows API to identify whether debugging tools are in use. The malware scans for minimum system requirements, including a specific number of active processes and at least two CPU cores. It also searches for common malware analysis and virtualization tools to avoid execution in environments where it may be scrutinized.
If these checks pass, the malware displays a fake error message to reinforce its legitimacy. Meanwhile, the malicious activities—deploying the XMRig cryptominer—run covertly in the background.
At the core of this campaign is XMRig, an open-source cryptocurrency mining software often abused by threat actors. Once installed, XMRig hijacks the victim’s CPU and GPU computer resources to mine Monero, a privacy-focused cryptocurrency.
XMRig’s ability to optimize resource usage across hardware configurations amplifies its mining potential, further exacerbating device degradation.
This attack is part of an ongoing trend of cryptojacking campaigns targeting businesses and individuals. Cryptojacking remains attractive to cybercriminals due to its stealthy, resource-intensive nature, giving threat actors financial gain with a relatively low risk of detection.