Beware of Fake Job Campaigns That Deliver Malware on Victims
- Multiple and differentiated fake job campaigns target victims through the LinkedIn platform.
- The actors deliver malware through the “More_eggs” backdoor and other methods, targeting whole organizations.
- Right now, the highest activity is primarily detected in the US, but the spectrum remains global.
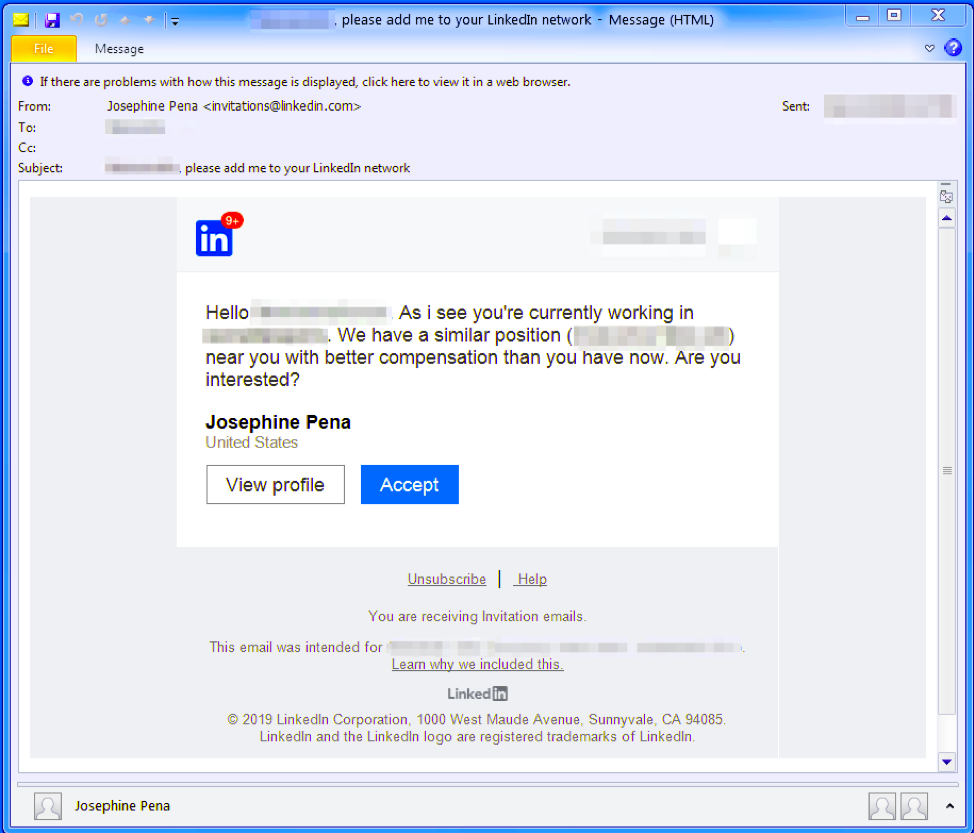
As highlighted in a recent report by Proofpoint, fake job campaigns are on the rise, targeting US companies in various fields, as well as high-profile organizations from around the globe. The fraudsters are impersonating staffing agencies in the LinkedIn platform, and search for profiles of people who work in the companies that they want to attack. Taking advantage of the platform’s direct messaging, they approach people and offer them a fake position that is similar to the one they’re holding at the time but with a higher salary.
image source: proofpoint.com
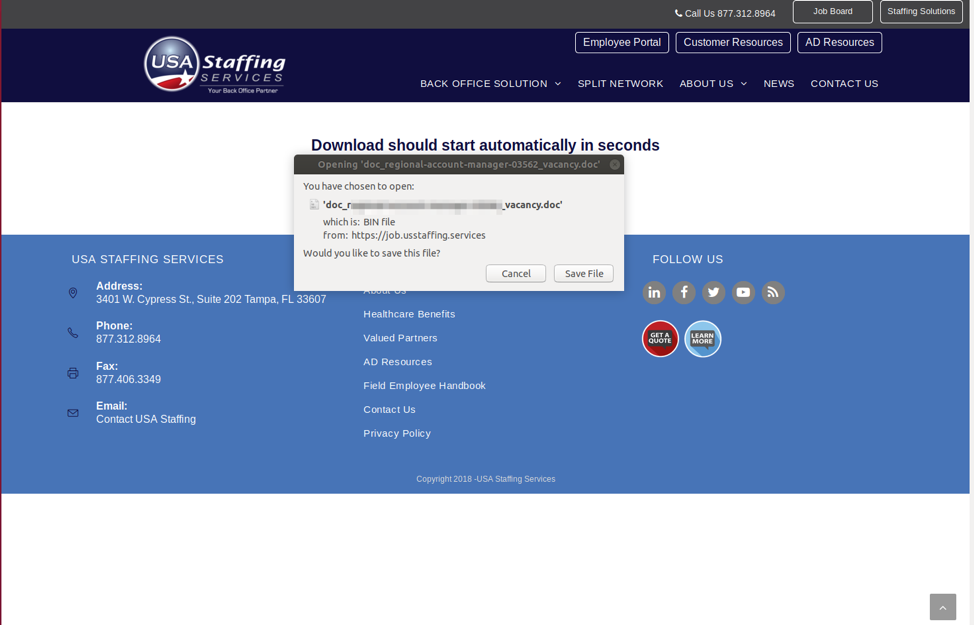
Having set the bait, the actor is sending a reminder email to the target after a week or so, attaching a PDF that contains shortened URL links to a supposed “full job description”. If clicked, the victim is taken to a hoax page that looks like it really belongs to the alleged staffing agency that has supposedly reached out to them. The landing page features all the legit branding elements like logos, design, etc., tricking those who don’t pay much attention to the actual URL. There, a document download is automatically initiated, with the file named with something relevant to the job vacancy. Of course, the document contains malicious macros that can deliver the More_eggs and other types of malware when ran on the victim’s machine. If this machine belongs to the target company, the better for the attackers.
image source: proofpoint.com
More_eggs is a JavaScript backdoor that connects to its C&C (command and control) server to carry out further downloading and execution of additional files and scripts, run shell commands, add or delete startup entries, etc. While this is the case in several campaigns of this type, some attackers prefer to add the links directly on the main message of the email and override the PDF step entirely. Variability in the malware delivery methods is vital in staying versatile and avoiding an easily identifiable pattern. This is why the set of tools used to develop the malware distribution mechanism also varies, including the Taurus Builder, VenomKit, and the More_eggs of course.
People are advised to be very careful with HR and staffing agents who approach them on LinkedIn, and/or follow up with an email. As the tools and methods that are used by threat actors are getting increasingly stealthy, and as landing pages have become deceptively polished, it is easier to fall, a victim, if opening URLs and downloading documents is taken light-hearted. For a full list of the indicators of compromise for all these fake job campaigns, check out Proofpoint’s detailed report.
Have you ever received a fake job offering like those described above? Let us know of your experience in the comments section below, and don’t forget that you can help us spread the word by sharing this post through our socials, on Facebook and Twitter.