Fake Browser Updates Disseminate New macOS Infostealer Malware in Global Campaign
- New threat actors were seen leveraging legitimate but compromised websites to distribute malware.
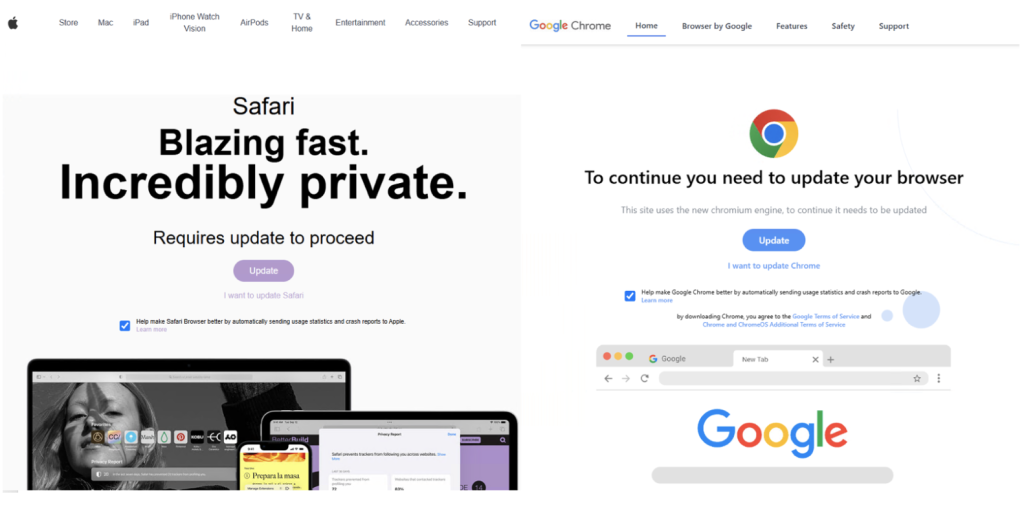
- One of them, dubbed FrigidStealer, is a new macOS-specific infostealer disseminated via fake browser updates.
- It collects and exfiltrates browser cookies, password or crypto-related files, and Apple Notes.
Two new threat actors, TA2726 and TA2727, leverage compromised websites to deliver malware payloads tailored to the victim's device and location, with an emphasis on a new macOS-focused malware targeting users through fake browser update schemes.
Active since at least January 2025, TA2727 is part of a larger web inject operation that uses traffic distribution systems (TDS) for malware delivery, as noted in the latest Proofpoint security report.
These actors utilize fake software update lures to compromise systems. TA2726, which most probably acts as a TDS for TA569 and TA2727, was the main distributor of web inject campaigns throughout the years, with its SocGholish injects used for malware infections and follow-on ransomware attacks.
The tactics primarily involve malicious JavaScript injected into legitimate websites. These attacks often unfold in three phases – execution of web-based injects that lure users into clicking fake update buttons, traffic redirection, and malware delivery.
Traffic redirection is orchestrated by TDS infrastructure to specific malicious payloads based on the visitor's location, device, and browser.
The disseminated malware targets Windows, Android, and macOS systems. Payloads include LummaStealer (Windows), Marcher (Android banking trojan), and FrigidStealer (Mac).
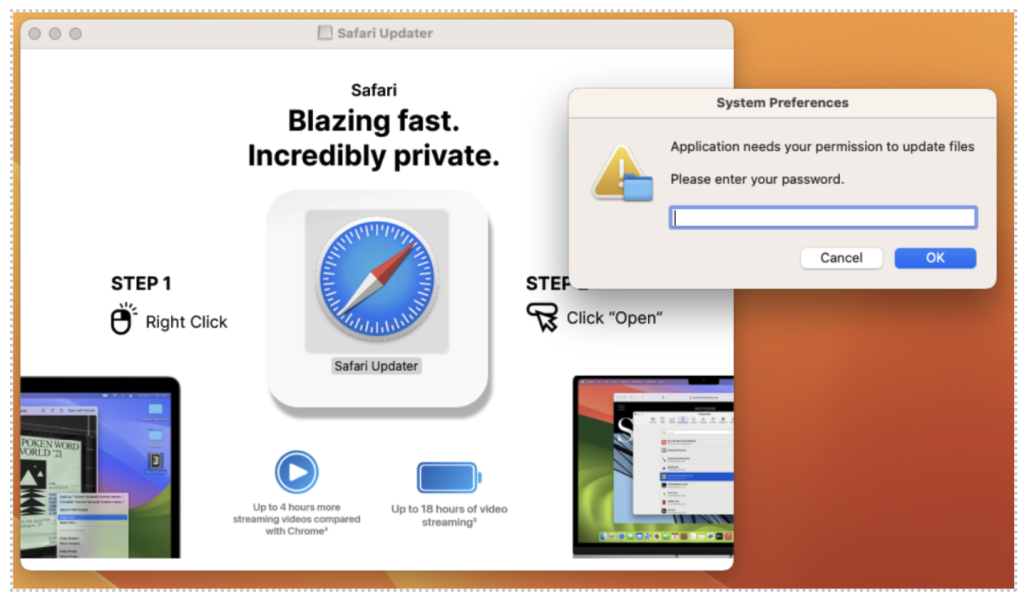
Proofpoint researchers highlight that TA2727 targets MacOS users through malicious browser update prompts, exploiting a common security bypass where users are encouraged to right-click and select "Open" to install untrusted applications.
FrigidStealer is developed in Go and utilizes WailsIO to mimic legitimate browser updater interfaces, further enhancing its deceptive appearance.
Once executed, it employs AppleScript to prompt victims for administrative privileges, allowing it to harvest and steal vital information, including browser cookies, files related to password material or cryptocurrency from the victim’s Desktop and Documents folders, and any Apple Notes the user has created.
The collected data is exfiltrated to its command-and-control server (C2), askforupdate[.]org.