Fake Banking, Social Media, and Dating Apps Evade Detection Via .NET MAUI Framework
- Cybercriminals seem to leverage the .NET MAUI framework to hide malware from detection mechanisms.
- These malicious apps are not distributed via official means but through third-party app stores and websites.
- The malicious apps impersonate known entities, including IndusInd Bank in India and the X social media platform in China.
Cybercriminals use Microsoft’s .NET MAUI cross-platform development framework to develop resilient malware targeting Android devices that bypass detection and steal sensitive user data in the form of fake banking and dating apps and even social media services.
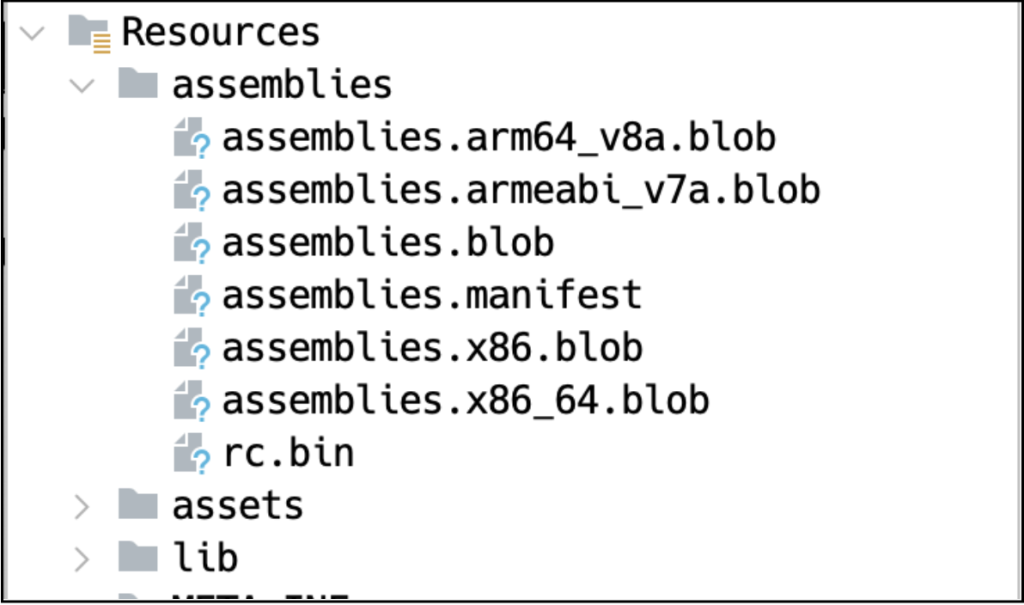
Unlike traditional Android apps that rely on DEX files and native libraries, .NET MAUI-based malware hides its malicious code within blob binaries, making it significantly harder for antivirus tools to detect harmful activities.
The McAfee Mobile Research Team has uncovered two prominent campaigns utilizing .NET MAUI to disguise their malicious intent.
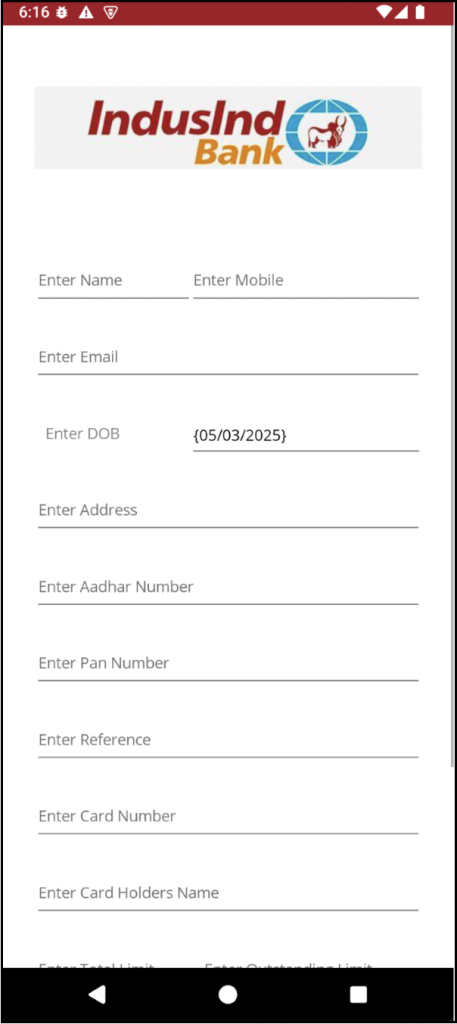
One campaign mimics the branding of IndusInd Bank, a prominent financial institution in India, targeting users by requesting sensitive personal and financial details. The stolen information, including banking credentials, is sent directly to the attacker’s command and control (C2) servers.
The malicious operations are skillfully concealed in the app, with no obvious traces in Java or native code. Instead, the harmful code resides inside encrypted blob files within the assemblies directory.
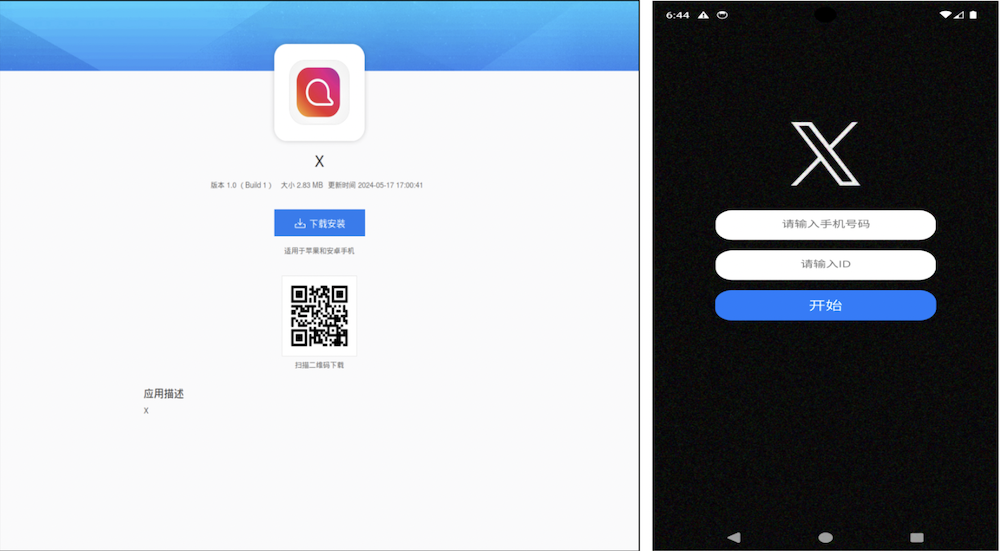
Another campaign focuses on Chinese-speaking users under the guise of social networking apps like X and even dating apps. These apps go beyond stealing personal information, collecting private content like SMS, contact lists, and photos.
Distributed through third-party app stores and websites, these malicious apps thrive in regions with limited access to official app stores, such as China.
This malware employs advanced evasion techniques, including multi-stage dynamic loading. Encrypted DEX files are loaded in layers, further obfuscating the app’s true intent. It also manipulates Android's Manifest.xml to disrupt static analysis tools and uses encrypted socket communication to secure the exfiltration of stolen data.
Microsoft’s decision to replace Xamarin with .NET MAUI in May 2024 introduced a more versatile cross-platform development tool. However, cybercriminals have capitalized on this upgrade, weaponizing the new framework.