Google Drawings and WhatsApp Short-Links Used in Amazon-Impersonating Phishing Campaign
- Hackers used Google Drawings and WhatsApp shortened URLs in Open-Redirect campaigns.
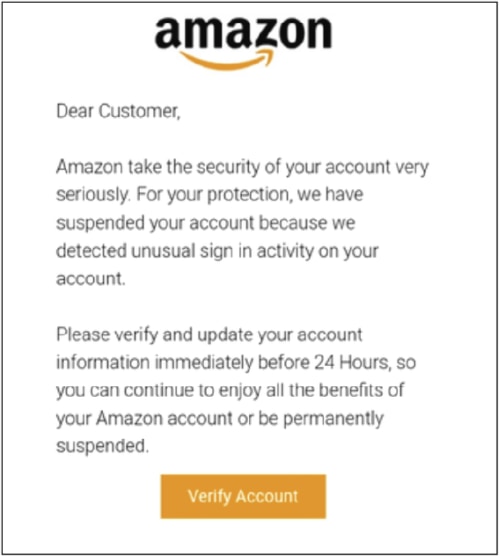
- The phishing campaign masqueraded as an Amazon email asking for security verification.
- Users’ details were then stolen via a malicious domain that requested sensitive personal data, including banking details.
A novel phishing campaign impersonating Amazon leverages popular sites to craft and host malicious elements, known as a ‘Living Off Trusted Sites’ (LOTS) threat. The attackers employ Google Drawings and shortened links generated via WhatsApp to evade detection and steal victims' sensitive details, as per a new report from Menlo Security.
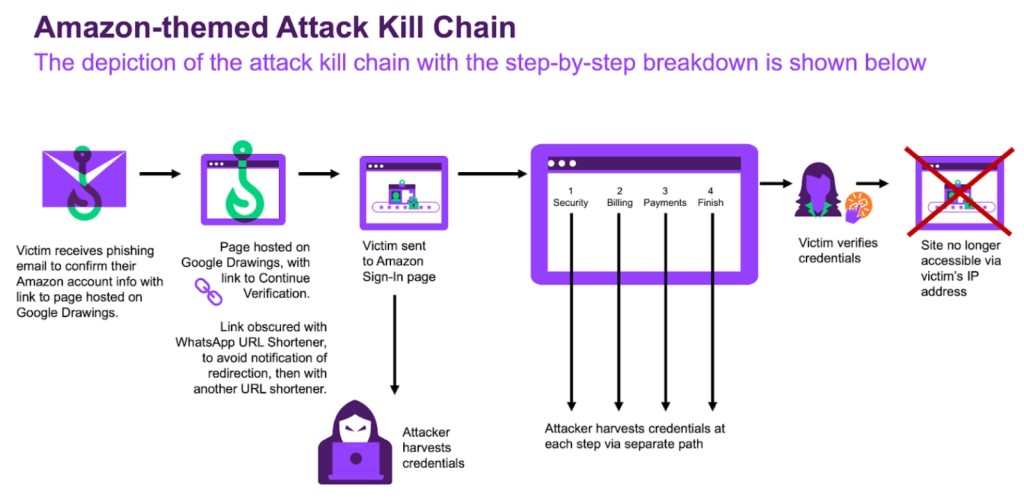
Open-redirect campaigns send users to a trusted website, which was Google Drawings in this specific sample, then redirect them to a malicious domain controlled by attackers.
This campaign debuted with a phishing email containing an image similar to an Amazon account verification link. The picture is hosted on Google Workspace suite’s Google Drawings, which allows users to collaborate on graphics and add links to these images.
Google Workspace is not typically blocked by traditional security tools, aiding the attackers to employ a legitimate tool for a nefarious purpose.
Clicking through redirects to a seemingly legitimate Amazon Sign-In page via the CTA button’s attached URL, which is a WhatsApp URL shortener, "l.wl.co," perfect for hiding the destination domain, as this shortener does not warn the user about leaving the website they are currently on.
A second step, designed to hide the original link from security URL scanners, adds another URL shortener for dynamic QR codes "qrco[.]de."
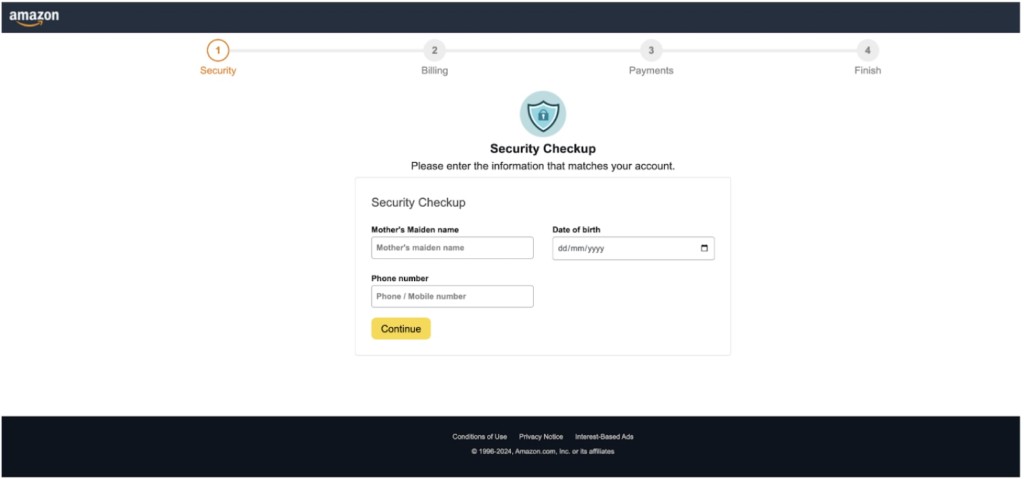
Once the victim enters their Amazon credentials, they are taken through four pages invoking a fake security checkup – ‘Security,’ ‘Billing,’ ‘Payments,’ and ‘Finish.’ The inputted details are exfiltrated separately for each step.
The personal information requested from the user includes the mother’s maiden name, birth date, and phone number, as well as the complete billing address and payment card details, such as the cardholder's name, card number, expiration date, and security code.
Recently, an exploit of Proofpoint’s email protection service allowed threat actors to send millions of spoofed phishing emails, perfectly impersonating Proofpoint customers, among which are huge companies and brands such as Disney, IBM, Coca-Cola, Nike, Best Buy, and more.