Facebook Business Pages Hijacked in SYS01 Infostealer-Distributing Malvertising Campaign
- An ongoing malvertising campaign persuades Facebook users to download the SYS01 InfoStealer via fake ads.
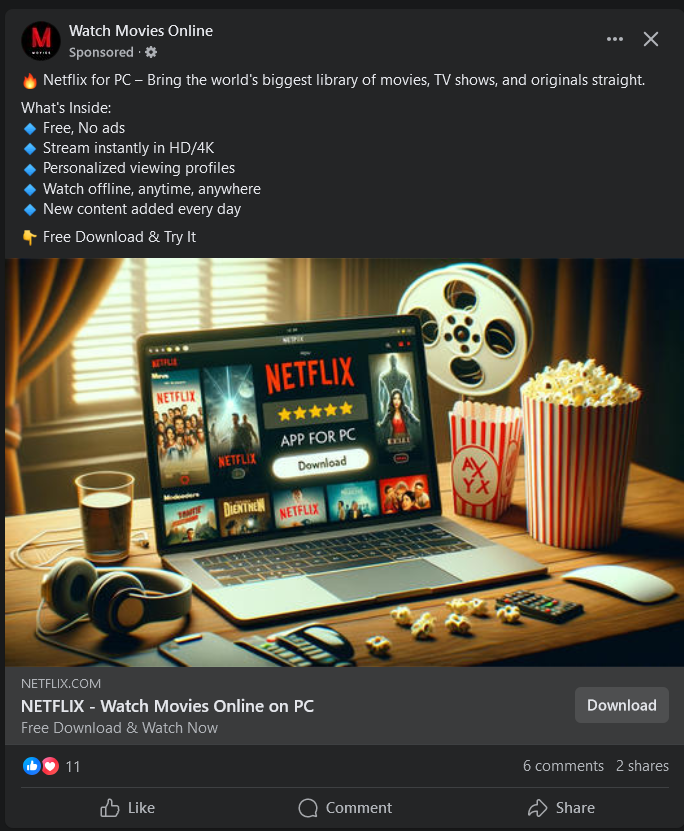
- The attackers impersonate several popular brands to distribute the malware, including ExpressVPN, Telegram, and Netflix.
- They harvest credentials of Facebook Business accounts to further place malicious ads – and also sell these credentials on the dark web.
A sophisticated malvertising campaign leveraging Meta’s advertising platform to deceive users into downloading the SYS01 InfoStealer malware via impersonating well-known brands, such as software tools related to productivity, video or photo editing, VPNs, movie streaming services, instant messaging apps, and even video games.
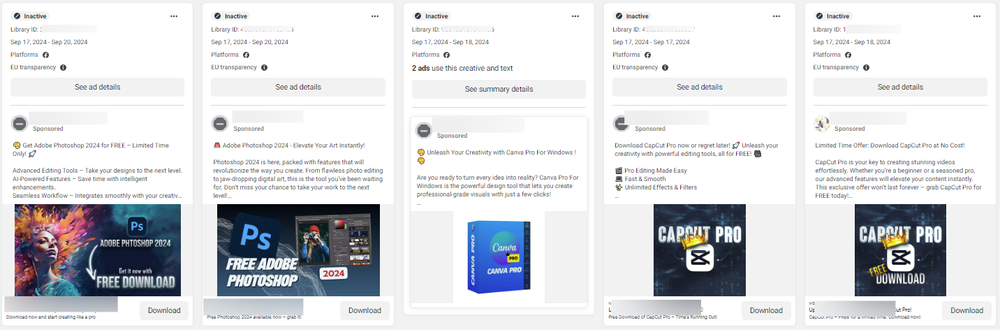
According to the latest security research from BitDefender, this campaign has been active for over a month and sees cybercriminals impersonating popular brands like Capcut, Canva, Adobe Photoshop, ExpressVPN, VPN Plus, Netflix, Telegram, Super Mario Bros Wonder, Black Myth: Wukong, and more.
At the core of SYS01 Infostealer's operation is the objective to harvest Facebook credentials, particularly those linked to Facebook Business accounts. Once cybercriminals gain access, they leverage these accounts not only to compromise personal data but also to propagate further attacks through hijacked platforms.
These compromised accounts serve as conduits for launching additional malicious ads without raising immediate red flags, as they appear legitimate and evade standard security filters.
When using the fake video games ads, the threat actor either directly offered malicious samples via advertisements or reused malicious domains that impersonated a generic video game download platform.
The ads typically point or refer to a MediaFire link for the direct download of malware in a .zip archive that contains an Electron application, and the infection method they use is always the same, employing the Electron-embedded Javascript code to drop and execute malware.
To avoid detection, the hackers continuously adapt their tactics, updating malware versions and launching new ads. The malware employs sandbox detection to halt operations if analyzed in controlled environments, making it challenging for cybersecurity tools to discover.
By utilizing hijacked Facebook business accounts, threat actors can exponentially scale their operations. Each compromised account is repurposed to disseminate further malicious ads, allowing the attack to expand its reach without the need to create fresh accounts manually.
This strategy is both cost-effective and time-efficient, enabling cybercriminals to maintain operational stealth and avoid traditional detection methods such as email phishing campaigns.
Beyond promoting malicious campaigns, cybercriminals monetize their efforts by selling harvested credentials on underground marketplaces. Facebook Business accounts are particularly valuable, providing a lucrative source of income.
Furthermore, stolen personal information—including login credentials, financial data, and security tokens—can be sold to other malicious entities, potentially fueling identity theft and other cybercrimes.
Utilizing nearly 100 malicious domains and a malvertising strategy that is evolving daily, the attack has a global reach, potentially affecting millions across regions such as the EU, North America, Australia, and Asia. Despite limited transparency from Meta outside the EU, the scale of the attack is concerning.