ExtenBro Changes the Victim’s DNS and Serves Adware on the Browser
- ExtenBro arrives with a bag of DNS changing and task scheduling tricks, so beware.
- The Trojan bundles adware that pushes ads to victims and generates money for the actors.
- Malwarebytes offers a detailed guide on how to remove it, as it can’t be done that simply.
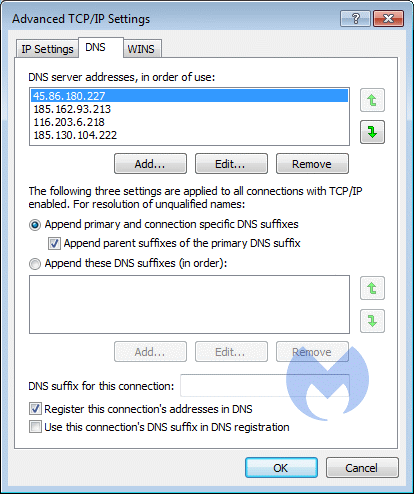
According to a Malwarebytes report, there’s a new adware bundler called ExtenBro that comes with a set of aggressive and persistence-boosting methods that make it a severe threat. More specifically, the Trojan is protecting itself by changing the DNS settings of the infected machine, ensuring that the victim will never be able to reach the websites of popular AV and anti-malware tools. The malicious software is adding four DNS server addresses that prevent the accessing of security vendor websites. The number ensures that if people don't use the “Advanced” Network settings, they will only see and possibly remove the first two of the four additions.
image source: blog.malwarebytes.com
To add persistence, ExtenBro also creates a task scheduler that re-configures the DNS settings in the way that the malicious actor wants them to be, so if you delete them and reboot you will be reverted to the same situation. The Trojan is also disabling IPV6 so as to ensure that the malicious DNS servers are always on use, and also adds a root certificate on the Windows registry. This certificate is then connected to a change in the Firefox user.js file that configures the browser to use the Windows Certificate Store.
image source: blog.malwarebytes.com
Check your DNS servers and look for the following numbers: 45.86.180.227, 185.162.93.213, 116.203.6.218, 185.130.104.222. If you find any of these in your settings, then you have been infected by ExtenBro. Remember, changing the DNS settings won’t be enough to get rid of the infection, as you’ll also need to remove the scheduler task entry and the root certificate. Of course, Malwarebytes is able to detect ExtenBro and uproot the threat, so if you want a quick and easy solution to this problem you may download Malwarebytes for free and run a scan and clean on your system.
Of course, if you are infected with ExtenBro, you won’t be able to visit the Malwarebytes website unless you manually change your DNS servers first. If you don’t know what DNS servers you're supposed to be used in the first place, use OpenDNS which is owned by Cisco, and which offers higher phishing security as well. If you are having trouble finding your steps in this process, check out the ExtenBro removal guide on Malwarebytes forums and you’ll figure it out.
Did you find the aforementioned DNS servers on your settings? Let us know in the comments down below, and help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.