Exploiting Critical Authenticated Bypass Vulnerabilities to Gain Admin Access on GitLab
- Two vulnerabilities in ruby-saml versions were exploitable through chain round-trip attacks and were patched by GitLab
- Researchers explained how differences in XML parsing would have allowed threat actors to exploit the authentication bypass vulnerabilities
- The method involved manipulating namespace confusion to gain admin access
GitLab detected and patched vulnerabilities that would have allowed a threat actor to log in to any account and gain complete control over them posing a risk to the account holders and their contacts.
The critical authentication bypass vulnerabilities CVE-2025-25291 and CVE-2025-25292 in ruby-saml versions 1.12.4 and 1.18.0. leveraged namespace confusion to gain unauthenticated admin access on GitLab Enterprise. Namespace confusion involves publishing malicious packages in the name of legitimate packages to confuse and trick developers into using the malicious versions.
Besides patching the flaws, learning about the chain round-trip attacks exploiting the ruby-saml library would help prevent threats. Ruby programming language allows the implementation of Security Assertion Markup Language (SAML) which is used for accessing a service through a service provider like logging into a shopping portal through a Gmail account.
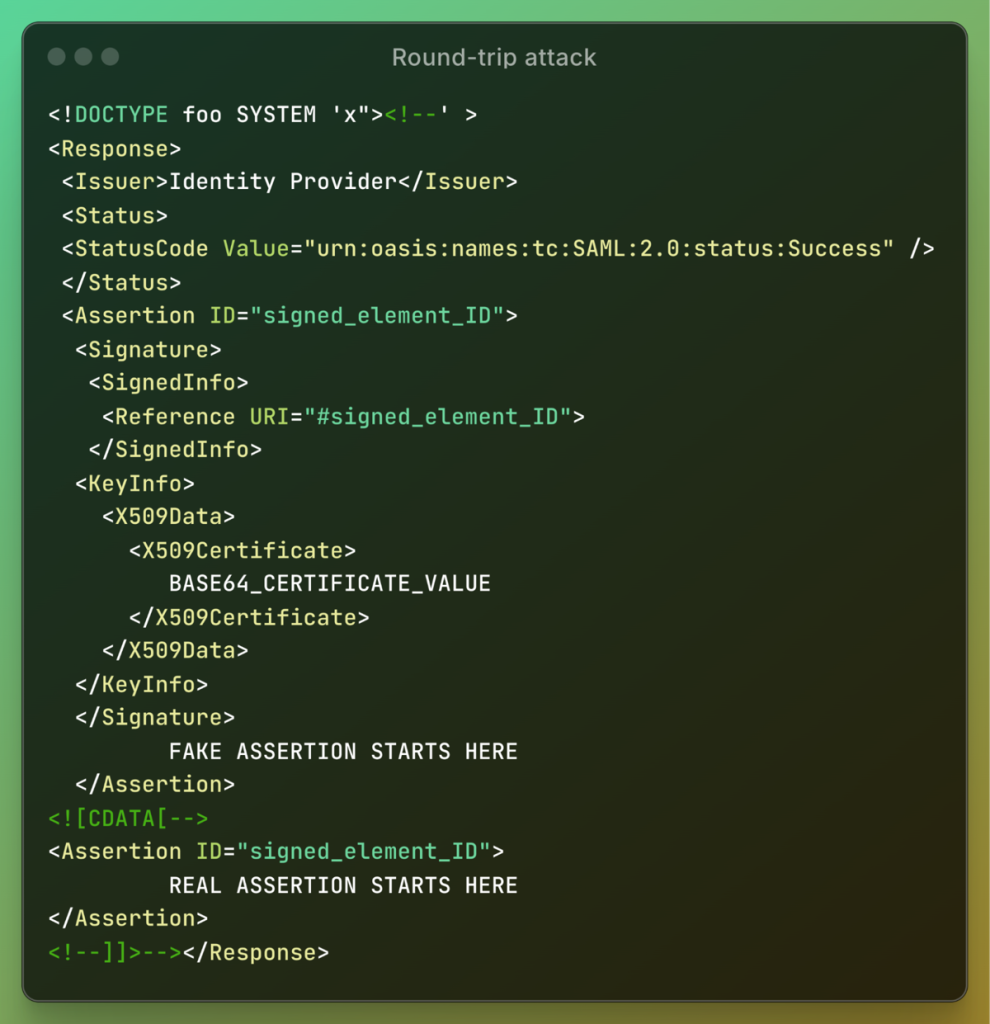
The login request passes through several validation checks. The SAMLResponse certificate is checked by comparing the hash with the stored signature on the server. The signature validation process starts with converting it to XML format. Both the XML samples must match to move to the next step.
After forging the original signature to trick the library, the process moves to the next stage which includes comparing the signed IDs. Here they modify the validation fields without disrupting the signature verification process as shown below in the round-trip attack process:
Here the threat actor must handle the validation performed through Nokogiri, an open-source software library that works with XML in the Ruby language. The steps check for a structure of the XML document with valid attributes, order, number of elements, and data type.
The Namespace confusion attack tackles both the ruby-SAML XML parsers i.e., REXML which checks the signature element, and Nokogiri which works with the DigestValue. DigestValue is the hash after encrypting login data.
This intricate process involves searching for the signature element in the XPath query. There is a flaw in REXML which ignores a restriction that XML follows to prevent duplicate attributes in the same name.
The threat actor could use this to his advantage by specifying two namespace attributes. This confuses the process with Nokogiri reading one and REXML reading another attribute.
REXML is designed for Ruby for monitoring XML documents. Hackers can successfully exploit unpatched critical authentication bypass vulnerabilities by creating two signature elements. All they would need to do to bypass Ruby-SAML validation is to create a signature with a valid digest value and another with a fake one.
Moreover, threat actors can extract a legitimate signature element using publicly available signed XML documents from a service provider like Identity Providers (IdPs) that support Single Sign-On protocol by default.