Exchange PoC Released and APTs Gather Around Vulnerable Servers Like Piranhas
- As if the situation wasn’t dramatic already, someone has released a PoC to exploit vulnerable Exchange servers.
- Already, there were at least 10 APTs that have been massively exploiting email servers for over a week now.
- The recently released patches are yet to be applied by hundreds of thousands of systems that remain vulnerable.
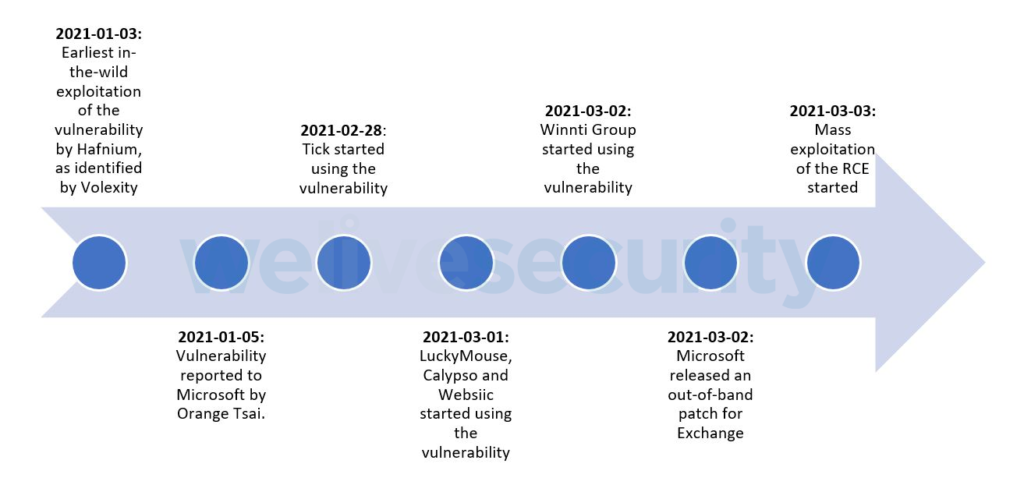
The situation with the Microsoft Exchange security lapse is unfolding a lot worse than what even the most pessimistic predictions could suggest, as literally everything is playing out badly. First of all, it took Microsoft a very long time to discover the flaws. Secondly, they spent two months after receiving a detailed report about the vulnerabilities before a patch was released. Thirdly, there are still hundreds of thousands of Exchange servers that remain unpatched and vulnerable.
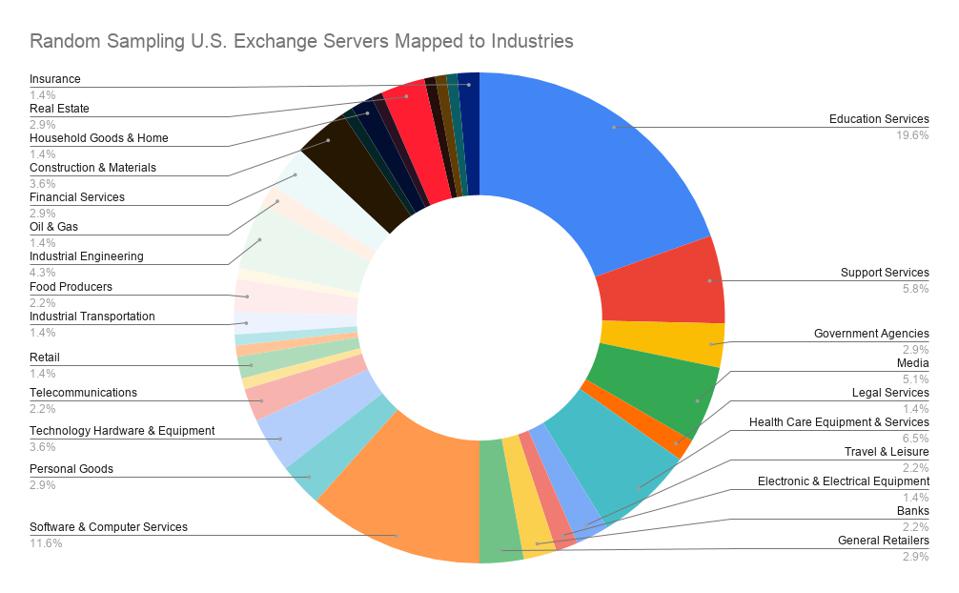
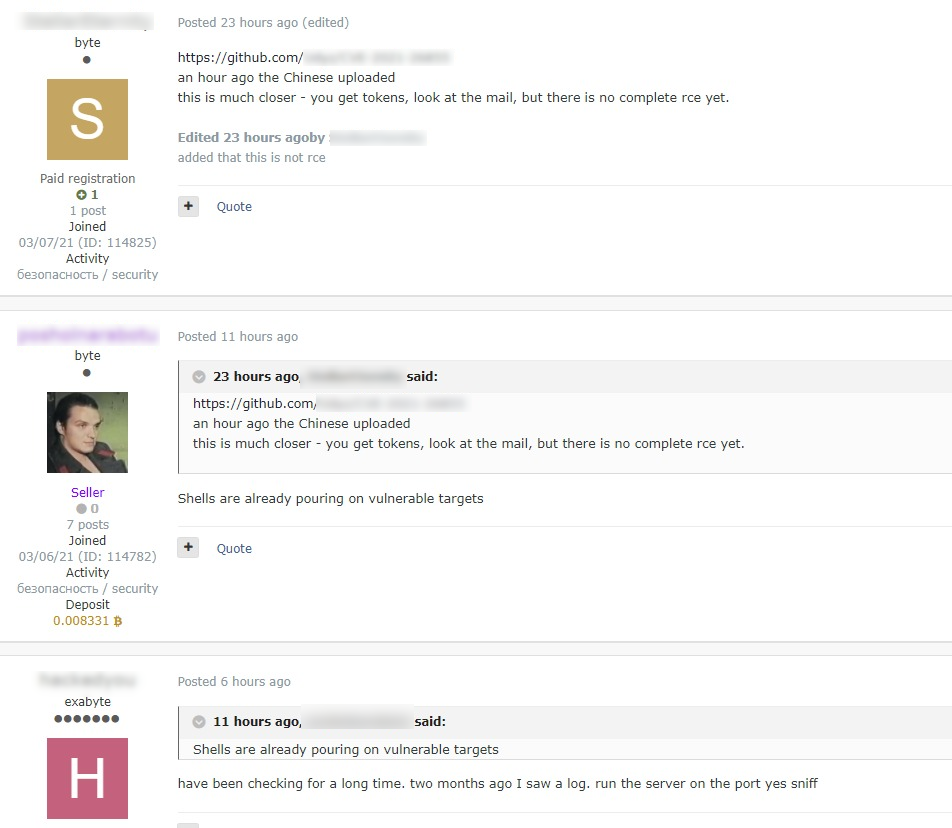
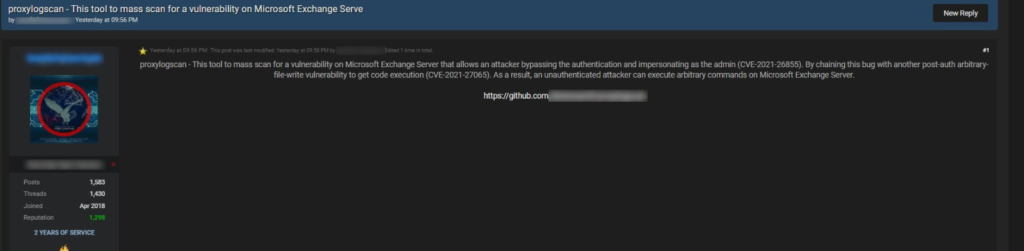
To top all that, a Vietnamese hacker thought that now would be the ideal time to publish his Exchange exploit proof-of-concept code (PoC) on GitHub and explain the technical aspect in detail in a post on Medium. Even before hacking groups had that valuable PoC at their disposal, they were already flocking vulnerable systems, and ESET reports to have identified the activities of at least 10 APT groups launching mass-exploitation attacks since March 3, 2021.
Obviously, sophisticated actors develop their own exploits, but the PoC could now open the door to less capable actors or non-specialized ransomware groups. Even for skillful hackers, the PoC could help them realize more entrance points. It was just very bad timing for this release, but there are no laws on ethics, so this is what everyone's dealing with right now.
KELA's threat analyst, Victoria Kivilevich told us:
In the meantime, the number of organizations that are admitting huge-scale email data compromises grows exponentially by the day. In Germany, the national cybersecurity watchdog announced that as many as 60,000 computers were exposed to the flaw, 25,000 of which remain unpatched. In Norway, the parliament admitted that it had suffered a cyberattack where the actors exploited the recently disclosed Exchange flaws.
In the United States, the number of compromised entities is too big to even estimate right now, but CISA maintains that at least it doesn’t include any federal agencies.
We are clearly in the stage of widespread exploitation. At the same time, cybersecurity agencies are investigating, trying to figure out who may have been compromised and what could have been accessed. Exchange and SolarWinds were so close and so big that the same teams that were already overwhelmed investigating and coordinating the first incident response are now called to split their time and focus their attention on the new problem.