Evernote Web Clipper Chrome Extension Allows Hijacking and Information Stealing
- Researchers warn of a severe Evernote vulnerability affecting older versions of its Chrome extension.
- An attacker could abuse the extension’s injection infrastructure to run arbitrary code and inject payloads onto legitimate frames.
- The flaw has been fixed now, so everyone using Evernote are urging to update their extension immediately.
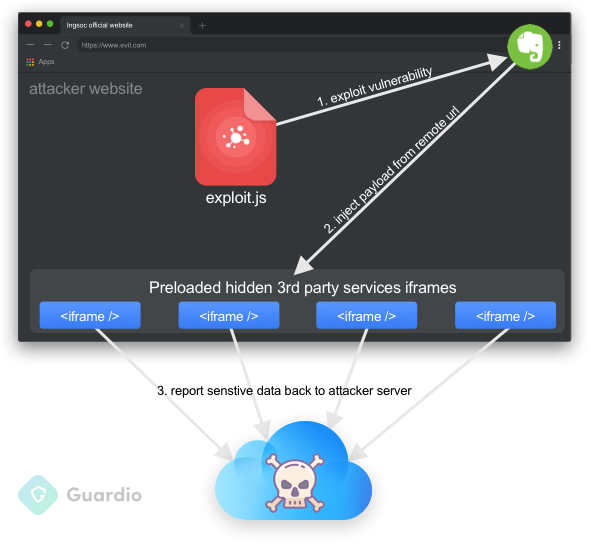
Researchers from the Guardio team have published a report about a critical vulnerability concerning the Evernote Web Clipper extension for Chrome. The particular flaw concerns a logical coding error that could enable an attacker to execute arbitrary code and gain access to sensitive user information from any website that the victim visits. This means that using the Evernote extension could lead to losing your financial information, social media login credentials, email content, and plenty more. This nasty flaw was given the identification 'CVE-2019-1259', it was discovered and reported to Evernote last month - and has now been fixed with a patch.
If you are using version 7.11.0 or earlier, make sure that you update your Evernote Chrome extension to a more recent version (7.11.1 or later), otherwise you remain vulnerable. The proof of concept (PoC) code that was published by the Guardo team researchers shows how it all starts by visiting a malicious website which loads iframe tags that are made to mimic the legitimate iframes from the targeted websites. These tags, however, are loaded with the exploit payload, which is specially crafted to be capable of stealing user data from the target websites. From login credentials and private information to browsing actions or even browser cookies, a wide range of exploitation is possible.
Image source: guard.io
From a technical perspective, this is an abuse of Evernote’s intended injection infrastructure. The Web Clipper extension is supposed to be able to interact with websites and their frames in order to be useful. By exploiting the 'BrowserFrameLoader.js' script, the attacker could then move forward by pushing arbitrary commands, since there is no authentication mechanism to stop it. Finally, via a logical oversight and inadequate input sanitization in the 'getBundleUrl' function, the attacker can manipulate the first part of the URL.
Evernote is a worldwide popular note-taking application that helps people create and organize their various daily, weekly, or monthly tasks, and keep them handy across all their devices. Approximately 4.6 million Chrome users have downloaded the extension, so the discovered vulnerability affects quite a lot of people out there. If you are using Evernote, or any extension on your Web browser, you should always make sure that you are keeping them up-to-date, as this piece of news is characteristic of how far things can go to the wrong direction only because of a browser extension flaw.
Have something to say on the above? Feel free to do so in the comments down below, and also on our socials, on Facebook and Twitter.