Ethical Hacker Says Microsoft’s Recall AI Feature Is Easy to Exploit
- Microsoft’s Recall collects screenshots using artificial intelligence and stores these interactions in a local database.
- A white-hat hacker has already created a tool that can extract sensitive data from Recall, naming it TotalRecall.
- The Microsoft feature can function without an Internet connection and even when you're not logged in to your Microsoft account.
Microsoft unveiled Windows Recall two weeks ago, a key element on its new Copilot Plus PCs, using an AI feature to capture data from all permitted applications via screenshots taken every five seconds. However, security experts have warned that it could be a security nightmare and one white-hat hacker even developed a tool called TotalRecall that exfiltrates private user data.
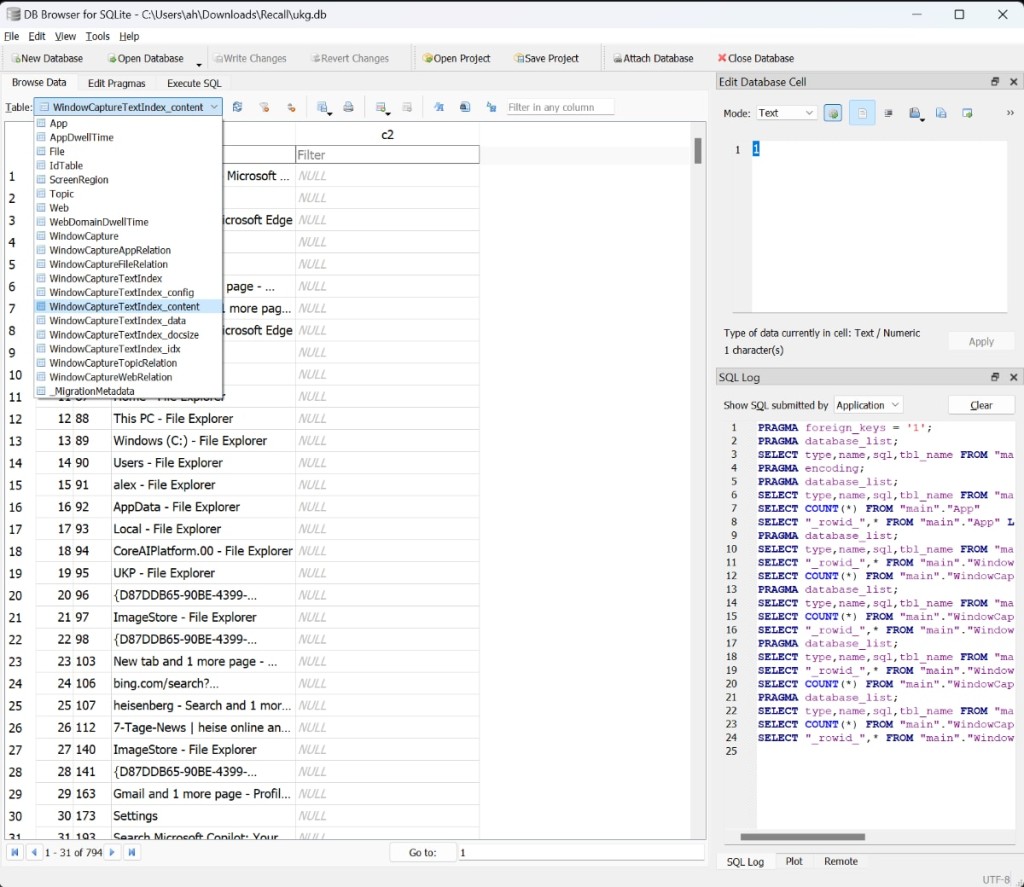
Recall stores everything locally in an unencrypted SQLite database, saving the screenshots in a local PC folder. Ethical hacker Alex Hagenah’s tool shows how anyone with enough know-how and the right tools could steal and access Recall data from Windows machines, encryption-free.
The AmperageKit, found online, allows one to emulate an ARM machine locally or create an instance on Azure. Hagenah used the latter for his tool, whose capabilities include date filtering and text search. It generates comprehensive reports of the captured windows, images, and search results.
TotalRecall copies the databases and screenshots to a specified extraction folder and parses the SQLite database for potentially interesting artifacts such as window titles, timestamps, and image tokens, leveraging Windows Recall's Optical Character Recognition (OCR) capabilities. It also renames the image files with a .jpg extension for easy access.
Microsoft’s Recall AI is found only on the new Copilot Plus PCs. If you do plan to acquire one and don't want Recall, you can easily disable the feature from Windows’ settings, where you go to ‘Privacy & Security,’ and then to ‘Recall & Snapshots.’ You can now toggle off the feature or delete any collected data.