The “Ensiko” PHP Web Shell Is a Multi-Platform Ransomware Trouble
- Ensiko is a new PHP web shell that can encrypt server files, deface websites, and steal information.
- The malware is pretty nasty, featuring a rich set of exploitation tools, including a steganography image generator.
- The web shell encrypts files using AES 128-bit, which pretty much locks them down for good.
Researchers at Trend Micro warn about “Ensiko,” a new PHP web shell that can target any platform that has PHP installed (Windows, Linux, macOS). It can also enable the threat actor to take remote control of the target, run shell commands, scan the servers for other web shells, download files, distribute mass emails, carry out brute-force attacks against FTP or cPanel, and many more.
The worst of all Ensiko’s features, though, is probably its ransomware-type abilities that include file encryption using RIJNDAEL 128 with CBC mode.
Source: Trend Micro
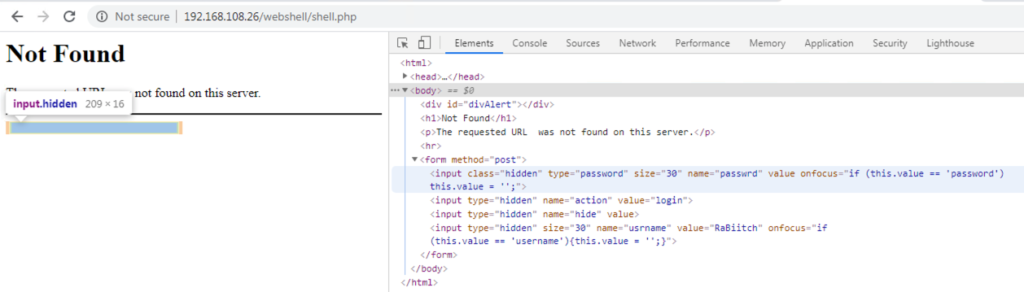
The malware is usually password-protected, showing a fake “Not Found” page with a hidden login form that only the adversaries would know how to use. In the analyzed sample, Trend Micro found out the password being “RaBiitch.”
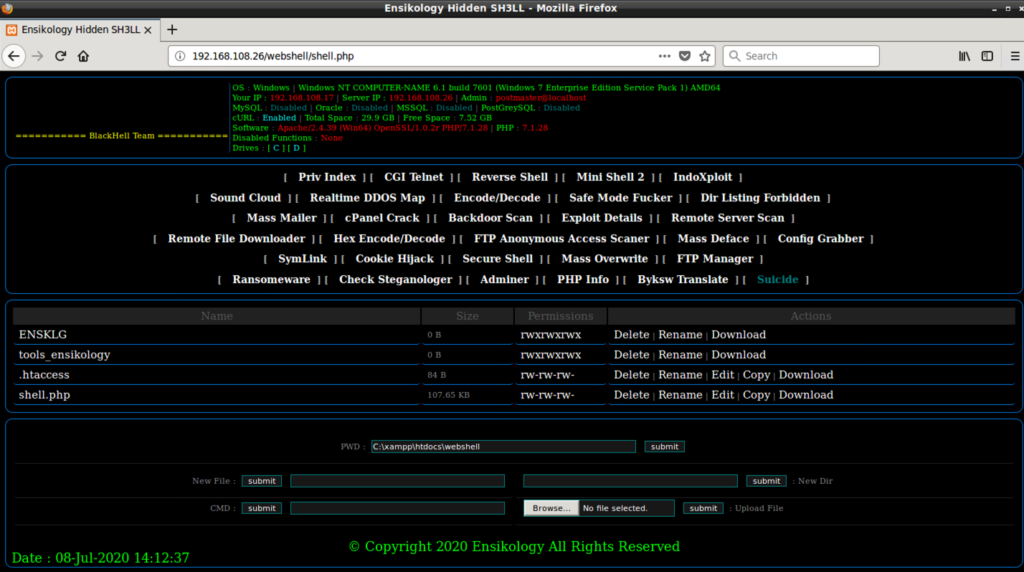
Once the actors are logged in, they get the “Ensikology” web shell, which looks like the following.
Source: Trend Micro
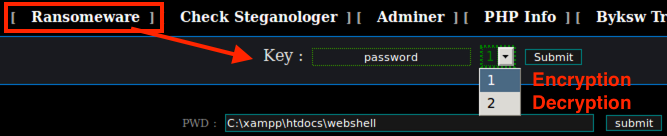
The “ransomware” feature encrypts all files and appends the “.bak” extension to the resulting filenames. The actor may pick any ransomware key they want, and then set the default page to a custom index.php file that is dropped in the server meaning to warn the victim of the situation.
Rijndael (AES) 128-bit is considered a powerful encryption method that is resistant to brute-forcing, and malicious actors appreciate it due to its speed.
Source: Trend Micro
Of course, this is only one of Ensiko’s numerous tricks, as high-level targets could very possibly have to deal with more severe, persistent, and complex attacks. Actors can use Ensiko to load additional exploitation tools from Pastebin, use a “steganologer” tool to create an EXIF image that hides PHP functions in it, conduct extensive backdoor scans, and exfiltrate files and raw data. They can also perform mass overwrite (essentially deleting everything), and generally wreak havoc.
All that said, what web admins should be focusing on is keeping Ensiko out - and a sure method to help minimize the chances of infection is to update web applications. Ensiko actors are typically exploiting known vulnerabilities to deploy the web shell, so for the PHP shell to drop onto a web server, a compromise must already have taken place.
To ensure that nothing nasty is running on your server, you should conduct periodic scans for web shells, as relying solely on setting up security and defensive mechanisms isn’t enough.
Read More:
- Seattle Police Booby-Trapped a File to Catch Ransomware Actor
- “WastedLocker” to Attack Large Corporations in the United States