Emsisoft Releases Decryption Tool for Most Variants of the STOP Ransomware
- Emsisoft provides a way out to 70% of STOP ransomware victims by releasing a universal decryptor.
- STOP has claimed 460k victims who were going after a free game or pro-grade software tool.
- 12 variants remain uncracked, and people who are affected are advised to stay patient.
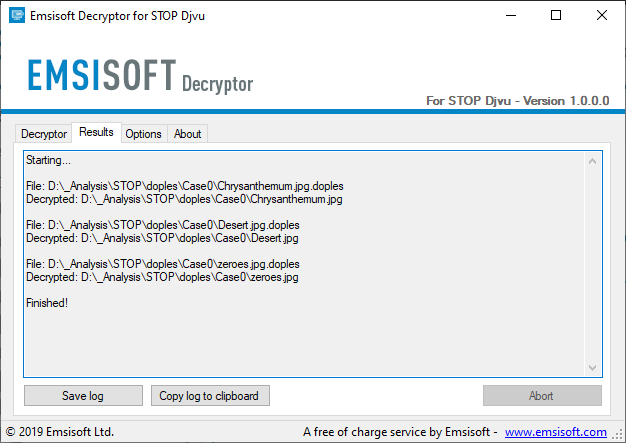
The STOP ransomware has been one of the nastiest problems we’ve had in the field since February 2018 when it first appeared. Counting at least 460000 infections and having numerous encryption filename extensions (DJVU, STOP, RUMBA, PUMA, SUSPENDED), it asked victims $600 in the first 72 hours, otherwise, they would be stuck with an RSA-1024 lockdown forever. As we always like to point out, waiting for the release of a decryption solution is the best strategy if you don’t have a backup to restore your files from. Emsisoft has vindicated this advice once again, as they have released a comprehensive decryption tool for STOP and the majority of its variants, almost putting an end to the obnoxious and widely used ransomware.
Good news! We've just released a free decryption tool for STOP. With more than 116,000 confirmed victims, it's by far the most active and widespread #ransomware. More details in the link #NoMoreRansom Hat-tip to @demonslay335 https://t.co/zq6qmpPHk4
— Emsisoft (@emsisoft) October 18, 2019
The decryption method is done via a side-channel attack on the ransomware’s keystream, which is the first time that is deployed in a tool of this type. Through this method, the free decryption tool can recover the files of approximately 70% of the victims, as it is capable of unlocking files encrypted by 148 out of the total of 160 STOP variants. The 12 variants that remain unbreakable correspond to the 30%, so there’s still a significant number of victims who won’t be freed yet. One of these is the newest Djvu variant that circulated after August 2019. Emsisoft suggests that victims of these 12 variants should stay patient, archive their encrypted files, and wait for a tool to arise in the future.
Source: Emsisoft Blog
STOP ransomware strains are generally getting spread to the public through game and software cracks as well as key generator utilities, so they are usually found in torrent packages. The first thing that people need to understand in order to stay safe is to stop using these tools, as piracy is the least of their concerns when doing so. If you don’t have the money to buy a license to something, consider open-source and free of charge alternatives which can provide you with something to get started. If you absolutely need to use a software tool that you downloaded via P2P networks, check it thoroughly by using an up to date AV tool from a reputable vendor before executing it.
If you are in need of help with the decryption process, the kind people of Bleeping Computer will welcome your questions in their forums. The community there is already helping the victims to use the STOP decryptor, the available offline keys, and the sample files, and we applaud this effort.
Are you one of the 460k victims of one of STOP’s variants? Did you pay the ransom, or did you prefer to wait until now? Let us know in the comments down below, or on our socials, on Facebook and Twitter.