Emotet Sends Mail to Inform Users of a Microsoft Word Update
- Emotet actors are now sending emails that inform users of a supposed Microsoft Word update.
- The messages urge the recipients to “enable content” on their suite, supposedly to enable the update.
- The malware then fetches a range of payloads, including QBot, Trickbot, and Ryuk ransomware.
Emotet’s bag of tricks is literally bottomless, and every week, we report of a new way its actors are attempting to distribute the malware. This time, they are sending emails that carry a malicious attachment, which informs the recipient about a Microsoft Word update.
The attached documents are nothing more than macro-ridden files that fetch the trojan onto the victim’s computer. This then turns the computer into a new email dissemination point, with the ultimate goal being to launch a catastrophic ransomware attack on the entire network.
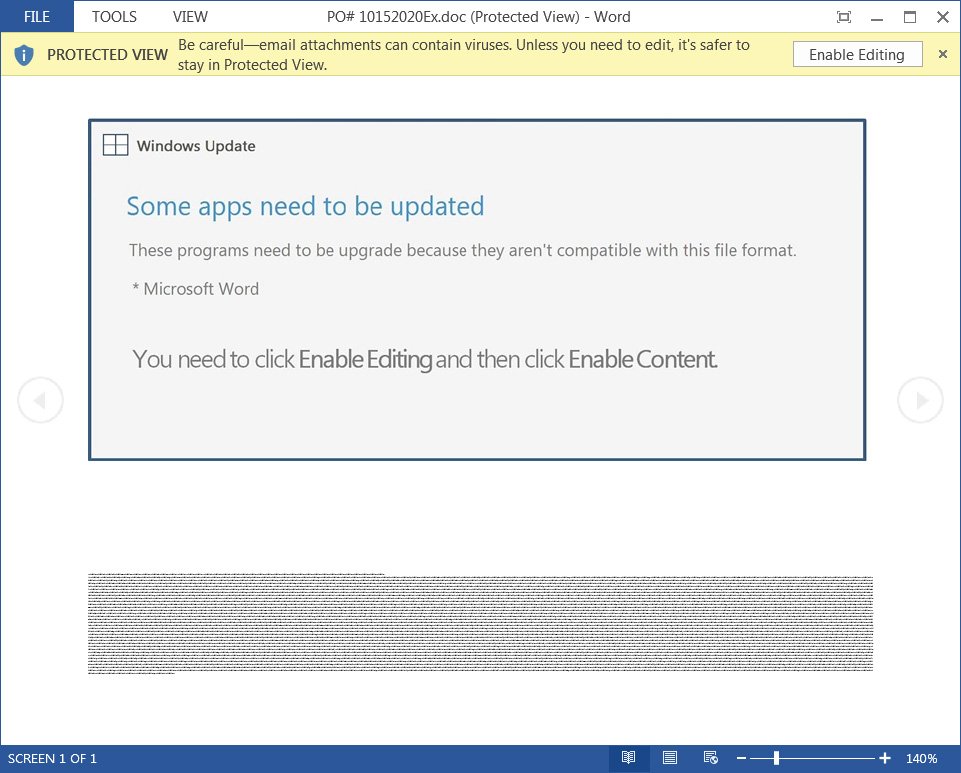
Of course, for all of this to work, the recipient must have the macros enabled on their Microsoft Office suite, so the actors have to convince them to do this on various pretenses. In this case, the lure is a Windows Update that concerns Microsoft Word in particular.
As the message reads, the current version that runs on the victim’s machine is supposedly incompatible with the received file format, but a click on “Enable Editing” and “Enable Content” will fix this by opening the way to the needed update.
Doing that simply lets the malicious macros to run, which results in the fetching of the Emotet malware onto the victim’s computer. In this latest campaign, Emotet may also download and install QBot, Trickbot, and Ryuk payloads, which then steal user information like passwords, and eventually encrypt the locally stored data.
It is important for users to understand the danger and identify the patterns of action used by these crooks, as rendering their methods ineffective is the best way to make these campaigns obsolete.
Keep the macros disabled on your Office suite at all times, don’t download attached files, and don’t try to open documents that came via unsolicited communications like the emails sent by these groups. No matter the claims made in these messages, treat them all as fake and move on with your life.