Emotet Returns for Christmas With a New Bag of Tricks
- Emotet has received a refresh in its infrastructure and some new obfuscation tricks, returning to the wild.
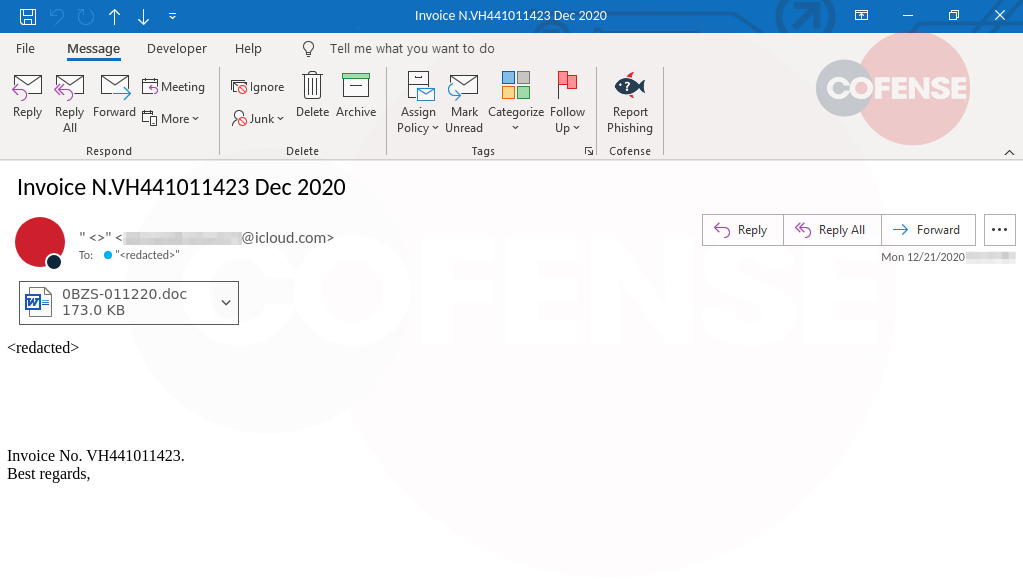
- The distribution involves emails of varying themes, all carrying a password-protected ZIP attachment.
- People are advised not to download attachments and to avoid enabling content on MS Office.
The persistent botnet known as “Emotet” has updated its payloads and distribution channels and is back online for the holidays. Researchers from Cofense warn about the new targeting, tactics, and the signs of the Emotet activity, which had dropped down to zero between October and November.
From the perspective of the malware’s abilities, these revolve around the same info-stealing stuff like credential harvesting from browsers, email content exfiltration, and the abuse of the victim’s contacts list for further distribution.
According to Cofense, the latest email themes used by Emotet actors are relevant to invoices, payments, holiday gift cards, etc. However, due to the wide-scope targeting of the botnet, there are quite a few email themes used in the wild, as well as different languages. What is common in all of these is the presence of a password-protected ZIP file attachment, which contains a macro-ridden Microsoft Office document.
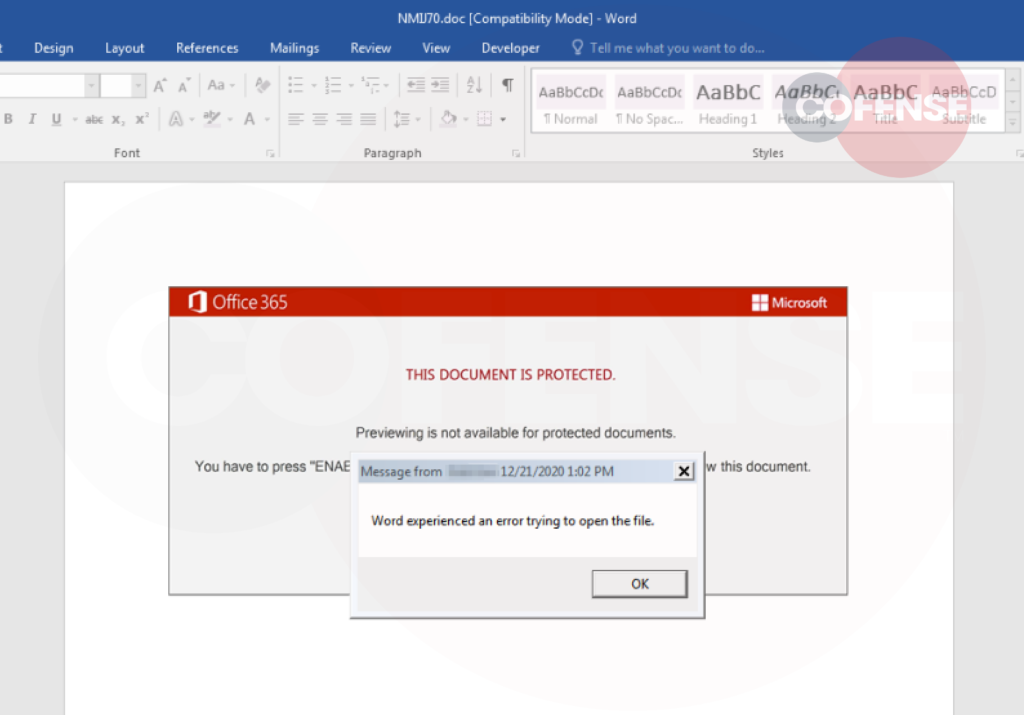
One key difference of the new document compared to earlier versions is that once the victim “enables content” and the macro runs, an error dialog appears saying that “Word experienced an error trying to open the file.” This is meant to help in keeping the infection secret, as the victim may falsely believe that nothing was executed after all. In reality, though, Emotet is already running in the background.
To evade detection from AV tools, the new strain is using the Windows built-in “rundll32.exe” for its initialization, whereas previously, it used a standalone executable. This is not a strong move, but it certainly reduces the chances of detection, even if slightly. Finally, in regards to the C2 communications, the plaintext data approach was abandoned for using binary data, adding some form of basic obfuscation to protect against unsophisticated network security solutions.
The secondary payloads remain TrickBot, Qakbot, and Zloader, with the first one noticed in the majority of the most recent cases. All in all, Emotet’s authors have made some effort to upgrade the arrant botnet and increase its chances of success. Still, if you’re careful and use good enough AV and internet security solutions, you have nothing to fear. Just don’t open attachments that come via unsolicited communications and don’t enable content on your MS Office suite.