Earth Preta Uses Legitimate and Malicious Software, Sideloads Toneshell Backdoor Variant
- The Earth Preta APT group leverages MAVInject and Setup Factory in its malicious activities.
- These tools are used to deploy payloads, bypass ESET antivirus, and maintain control over compromised systems.
- A TONESHELL backdoor variant sideloaded with a legitimate Electronic Arts app communicates with a C2 server for data exfiltration.
Earth Preta, also known as Mustang Panda, was seen employing new methods to infiltrate systems, refining its strategy to bypass antivirus solutions and maintain persistence on targeted systems by blending legitimate software with malicious payloads.
The advanced persistent threat (APT) group's latest campaign demonstrates sophisticated techniques that integrate both legitimate and malicious components, complicating detection efforts, Trend Micro’s Threat Hunting team uncovered.
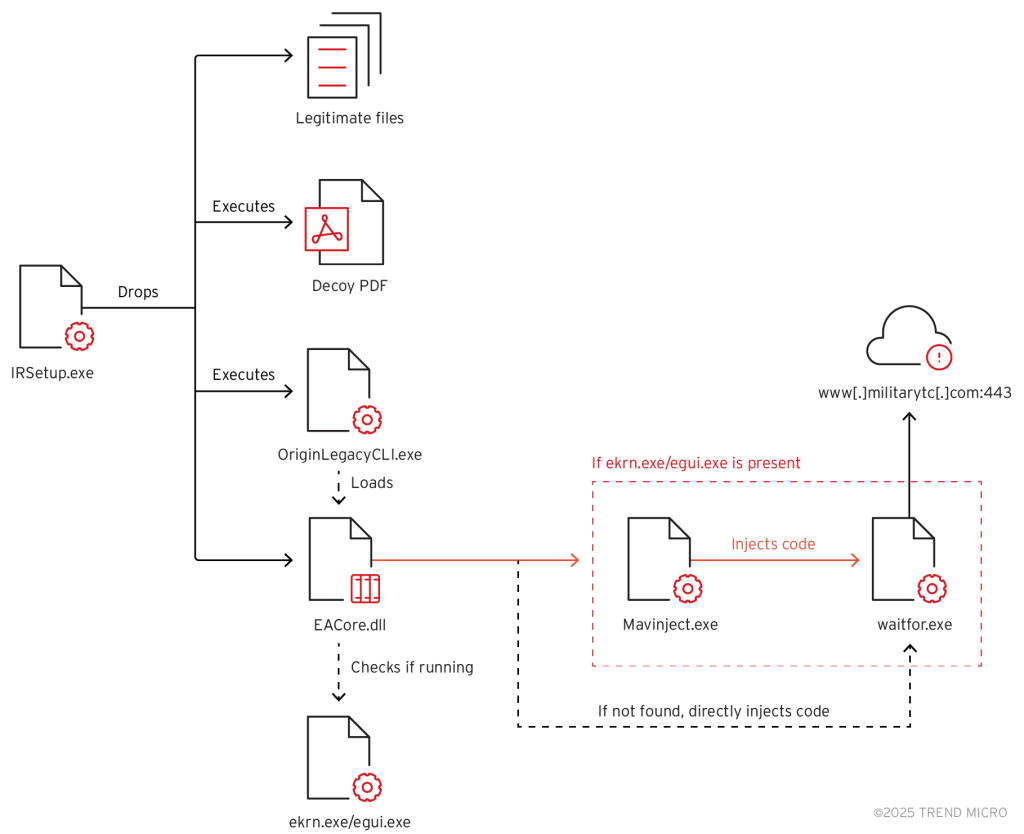
The group employs Microsoft Application Virtualization Injector (MAVInject.exe) to inject malicious code into the legitimate Windows process "waitfor.exe" when it detects ESET antivirus software running.
Setup Factory, a legitimate installer builder for Windows, is utilized to deploy and execute malware, further enabling stealth and persistence.
To distract victims, attackers present a decoy PDF document designed to look legitimate. For instance, one campaign used a document targeting Thailand-based users under the guise of an anti-crime initiative.
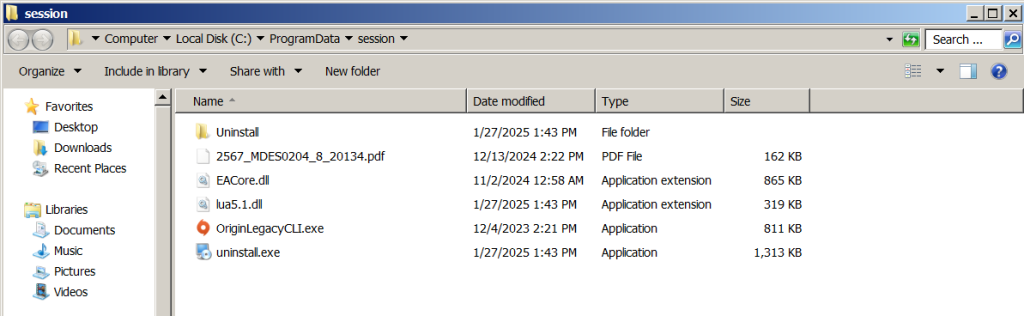
The attack begins with the deployment of a dropper file, IRSetup.exe, which places several files in the system directory. Among these files are legitimate executables and a modified variant of the TONESHELL backdoor.
Key to the operation is OriginLegacyCLI.exe, a legitimate Electronic Arts (EA) application. The attackers sideload this app with their custom malware, disguising malicious activity as routine processes.
Once in place, the malware communicates with command-and-control (C2) servers, enabling attackers to exfiltrate data or execute additional commands. Even when ESET antivirus solutions are absent, Earth Preta adapts its method, using manual injection techniques like "WriteProcessMemory" to deploy malicious payloads.
Since 2022, Earth Preta has targeted organizations across the Asia-Pacific region, particularly government entities. Previous campaigns utilized a different strain of malware, DOPLUGS, to compromise systems in Taiwan, Vietnam, and Malaysia.