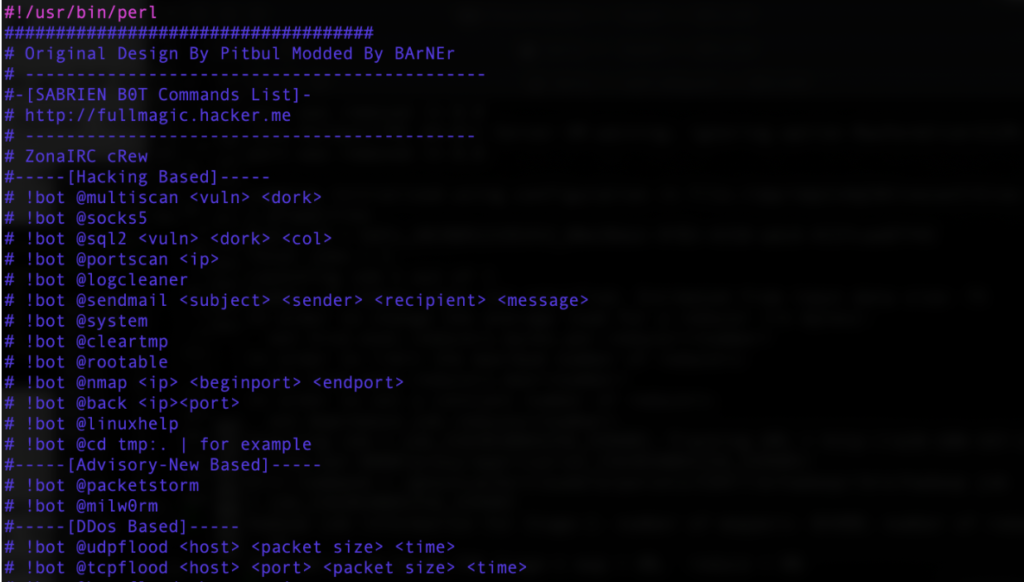
Drupal Installations are Still Under Attack by Drupalgeddon2 Actors
- Unpatched Drupal systems are being targeted by powerful malware based on a year-old flaw.
- The actors have several specialized PoC samples at their disposal, focused on version 7 or 8.
- The code of the malware is heavily obfuscated, and it comes hidden inside a GIF file.
According to a report by Akamai, actors are still leveraging a remote code execution vulnerability in the Drupal CMS that has been patched since March 28, 2018. Carrying the identifier “CVE-2018-7600”, the flaw allows an attacker to send a specially crafted AJAX request that targets a variety of form fields, resulting in the arbitrary execution of code. The first proof-of-concept code for this was released on April 12, 2018, and malicious actors have been using it as a basis to launch their attacks against unpatched Drupal CMS installations. Since then, more PoC samples were discovered in the wild, targeting Drupal 7 or Drupal 8 specifically.
The “Drupalgeddon2”, as this old vulnerability is nicknamed, was mostly used to plant Cryptominers, but in some cases, it was also used for site takeover attacks, web shell uploads, and shell reversing operations. Right now, Akamai researchers report that they observed attacks that execute code which is embedded inside a .gif file carrying the name “index.inc.gif”. Upon analyzing the attack patterns, the researchers found no signs of targeting specific fields or industries, but it is generally directed towards high-profile websites. The malicious GIF file is apparently hosted on a bodysurfing website that is based in Brazil, but this is almost definitely a case of a compromise and not a direct launch point.
Upon further inspection of the commands that the GIF is trying to execute, the researchers have noticed several attempts to remove previous installations and configuration files. The PHP code features gzip compression, rot13, and base64 encoding, so there’s a certain level of obfuscation going on. Once the second layer of commands are decoded, the malware that is stored in the $database variable is taking over, enabling the running of multiple functions. Examples including scanning for credentials, displaying MySQL configuration files, sending an email with sensitive data back to the actor, launching a web shell, renaming files, show system information, send SQL flood commands, and more.
Source: blogs.akamai.com
The only way to stop Drupalgeddon2 is to update your Drupal installation and apply the latest available patches. The fact that attackers are still leveraging this year-old vulnerability highlights that there are still many systems that are left to be running an older and exploitable version of the popular open-source CMS, and oftentimes, these systems are playing crucial operational roles in large corporate networks.
Have something to comment on the above? Let us know in the comments down below, or on our socials, on Facebook and Twitter.