Dreambot Malware Infrastructure Remains Down as Operations Went Silent
- The Dreambot trojan seems to have abruptly stopped operations, as the infrastructure remains down for weeks now.
- There have been no new versions in the wild since March, so this might be the end of Dreambot.
- It is highly unlikely that this will bring any real disruptions for malicious actors, as they will simply use other tools.
The CSIS Security Group is reporting on the complete ceasing of "Dreambot" activities. This botnet has been around over the last six years and has never been so silent before. The Danish cybersecurity firm believes that this is the end of operations for the malware, as the onion C&Cs and the back-end servers have been offline for weeks now. Hence, it is unlikely that the team behind the banking trojan is pausing operations to prepare a new and upgraded version. No new Dreambot samples have appeared in the wild since March, so we can assume that this threat is really over by now.
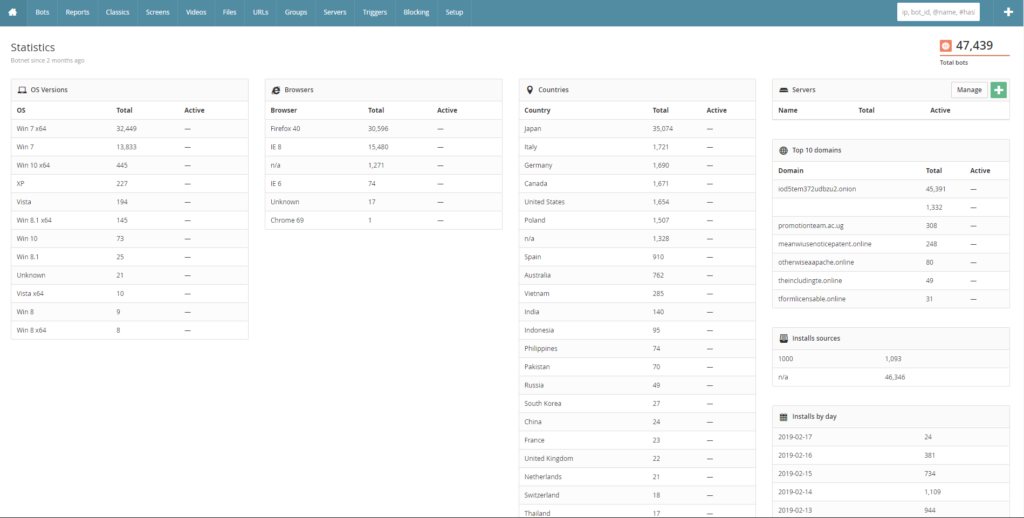
Dreambot was once a thriving operation, and during 2019 alone it accounted for over a million infections worldwide. While it started as a specialized banking trojan, it quickly evolved into a general-purpose trojan that was offered for rent to cyber-criminals. It featured “infection overview” panels with a friendly interface, and supported numerous operations in a wide range of fields. Dreambot was used by a community of hundreds of actors who undertook specific roles in each process, acting as well-organized gangs. From BEC fraud and ransomware infections to POS systems compromise and e-commerce operations, Dreambot supported a wide range of malicious acts.
Source: Medium
The exact reasons behind the termination of Dreambot remain unknown for the time being, and CSIS can only speculate. In general, the development of the botnet wasn’t very "hot" in the last couple of years, and the lack of new features could have pushed malicious actors to look elsewhere. Maybe the rise of Zloader or the appearance of multiple Gozi variants has played a role, or possibly the COVID-19 may have something to do with Dreambot’s sudden demise. We would presume that the “bus factor” of software projects like Dreambot cannot be comfortably big.
So, what happens from now on, then? Does this mean that we will get a break from banking trojan attacks? Unfortunately, not at all. Actors will just turn to other tools, and there is an abundance to choose from (Trickbot, Emotet). Hoping to see any languor in malicious operations due to the termination of Dreambot is like hoping that bank robberies will stop just because a gun maker stopped producing revolvers. Thieves will just buy a different gun brand and carry on raiding financial institutes. The only thing that will stop them is protective measures and defense mechanisms, and this is all what matters in cybersecurity as well.