DoS Vulnerability in Eclipse Jetty Calls for Urgent Updates
- Eclipse Jetty was found to be vulnerable to a denial of service exploit of medium severity.
- A fix is already out, so those deploying Jetty are urged to upgrade immediately.
- Jetty is very widely used, so the flaw potentially affects a large number of endpoints.
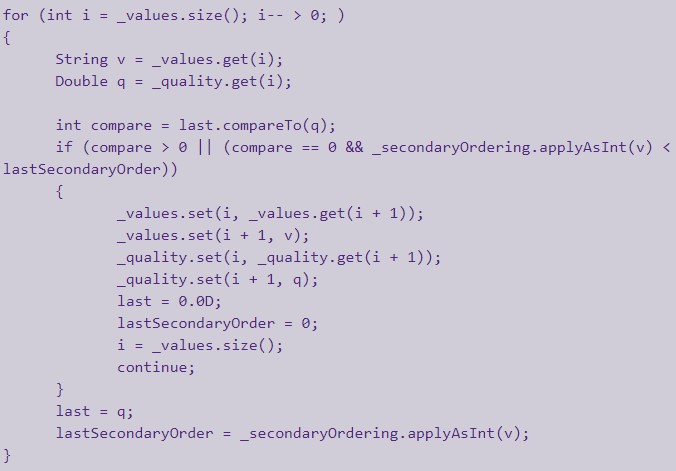
A team of researchers at the Synopsys Cybersecurity Research Center (CyRC) discovered a denial of service (DoS) vulnerability in Eclipse Jetty, a widely-used open-source web server and servlet container. Given the identifier CVE-2020-27223, the flaw lies in how Jetty handles a request containing multiple Accept headers with a large number of parameters.
This scenario would put the CPU into a state of processing numerous quality values, creating a DoS condition that can last for entire minutes each time.
These accept headers can be abused through Jetty’s default error handling, the statistics servlet, the HTTP servlet request fetcher, and the default servlet, so there are four individual features that offer an attack surface. The severity of the flaw is classified as “Medium,” but due to the extensive deployment of the product, it impacts a vast number of systems.
To get an idea, Jetty is used in products such as Apache ActiveMQ, Alfresco, Scalatra, Apache Geronimo, Apache Maven, Apache Spark, Google App Engine, Eclipse, FUSE, iDempiere, Twitter's Streaming API, Zimbra, Lift, Eucalyptus, OpenNMS, Red5, Hadoop, and I2P. It is widely valued as a varied application framework, but this is precisely where the need for advanced web protection services to cover it arises.
As NNT’s security expert Dirk Schrader told us:
The affected software versions are the following:
- Eclipse Jetty version 9.4.6.v20170531 through 9.4.36.v20210114
- Eclipse Jetty version 10.0.0
- Eclipse Jetty version 11.0.0
The CyRC researchers discovered the flaw on January 5, 2021, and the first confirmation of the reception of the report from its maintainer came a month later. Finally, a fix was published on February 22, 2021, which was pushed to versions 9.4.38.v20210224, 10.0.1, and 11.0.1. Thus, if you’re using anything earlier than that, you are advised to upgrade immediately.