The “djvu” (STOP) Ransomware Enters 2020 with Impetus
- Researchers warn that the djvu ransomware is still active and continuously evolving with new strains.
- Most of the strains remain unbreakable, while the ransomware downloads info-stealers too now.
- The actors are asking for the payment of $980, which reflects the strength of djvu after all this time.
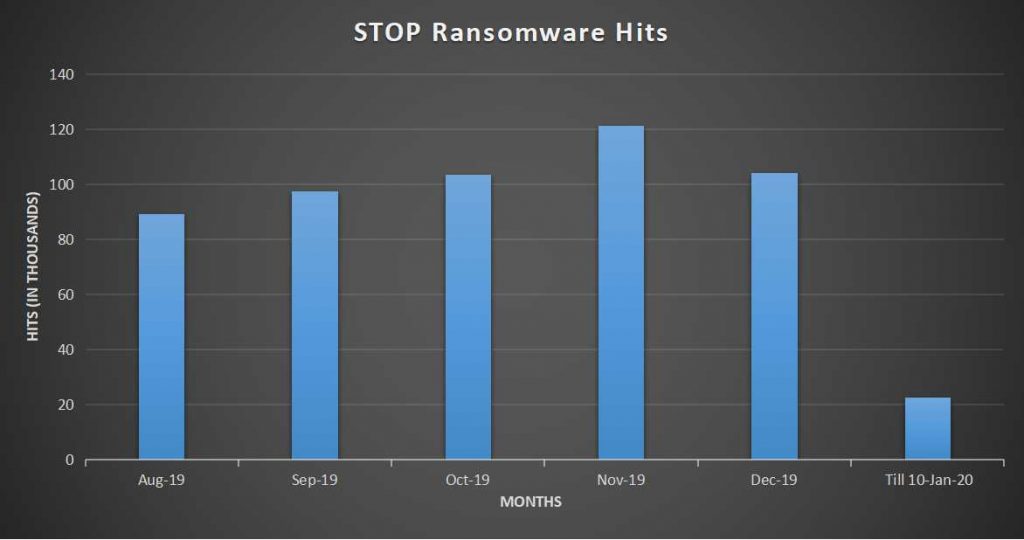
Quick Heal researchers report that the djvu ransomware, aka “STOP”, remains active and aggressive in the new year. The popular ransomware strain counted over 20 thousand hits until January 10, so there are no signs of the menace subsiding. Simply put, malicious actors prefer to use ransomware strains that are hard or impossible to stop, and easy or cheap to source. The djvu fits this shoe, as about 30% of the 200 variants that circulate the net right now remain unbreakable. For the rest, people can always give Emsisoft’s decryptor a go.
Source: Quick Heal Blog
According to the data that was sourced from the most recent campaigns, actors are infecting their victims by using cracked software, keygens, and app activators. That said, most of the infections come from questionable torrent files. The main payload of the djvu ransomware features advanced anti-emulation and anti-debugging features which are achieved by the wrapper. In many cases, identifying the country of the victim and deciding whether or not to decrypt the local files is still an active feature of djvu. In most variants, the countries that are excepted are Russia, Syria, Ukraine, Armenia, Kazakhstan, Belarus, and Uzbekistan.
Source: Quick Heal Blog
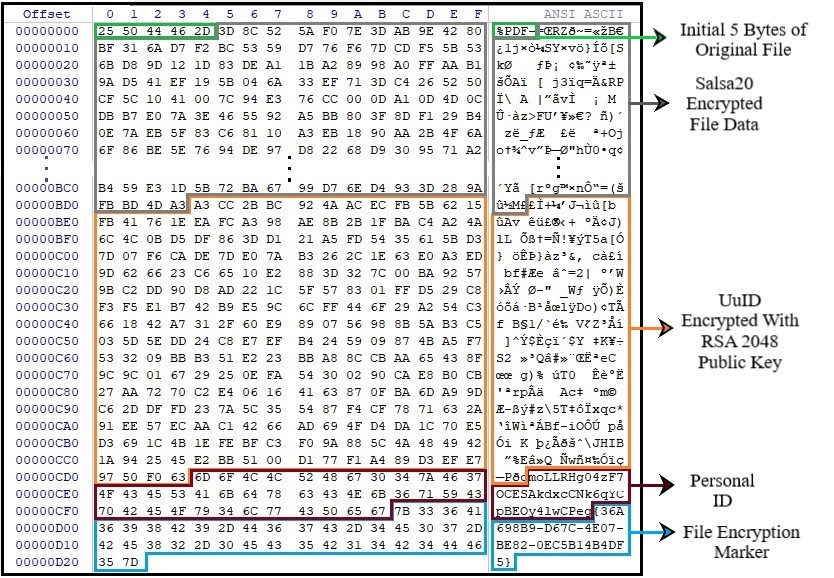
Another element of the recent campaigns is that djvu is trying to fetch additional payloads from its C2 server. The most common is the Vidar info-stealer and the Vilsel Trojan. Vidar is able to steal browser login data, cookies, cache, messaging and email data, and even two-factor authentication data. Before the encryption of the files begins, djvu drops a ransom note to all of the enumerated directors and creates a RUN registry entry for persistence. The encryption is done either by using an online key or an offline one. In both cases, the first 5 bytes of the original file are kept intact, while the rest is encrypted with the Salsa20 algorithm.
Source: Quick Heal Blog
The ransom note is asking the victim to pay $980, or $490 if the payment is done within three days. The only way to communicate with the actors remains the email, while a personal ID that is unique to each victim remains crucial for the decryption process. Remember, this concerns white-hat tools and not the actors, as paying the latter wouldn’t guarantee that you’ll get your files back anyway. To steer clear of the dangers of djvu/STOP, avoid the downloading of cracked or pirated software from torrent sites, and take regular backups of your most important data on offline mediums.