The “DJI GO 4” App Is Engaging in User Privacy-Risking Practices
- DJI’s official app is collecting user data even when running in the background and sends it to Weibo.
- The app tries to convince users to allow privacy-risking permissions, like letting it update from outside the Play Store.
- DJI is doing something ubiquitous, but they’re doing it in an unethical and secretive way.
DJI is a Chinese maker of drones that is considered a leader in the field, marketing powerful camera fliers with gimbals, stabilizers, and advanced flight control systems. DJI’s most popular products are the Phantom, Mavic, and Spark, having sold millions of units around the globe.
The thing is, though, the “DJI GO 4” official accompanying app is following several insecure practices that put the users’ privacy at risk. This conclusion came from cybersecurity firm ‘GRIMM,’ who analyzed the way the app operates under the hood, so here’s what they’ve found.
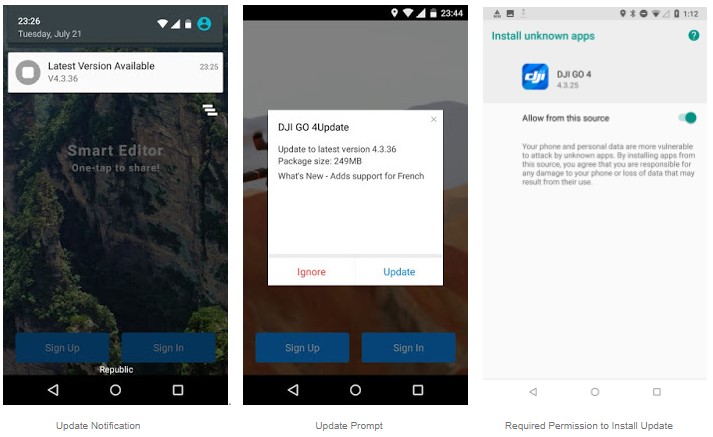
First, the app has a feature that allows it to update its components from outside the Google Play store by fetching APKs. For this to get activated, the user receives a notification informing them of a new version being available. The update change-log provides something irrelevant to the fetching of SDKs, like additional language support. The user is then prompted to permit the app to install stuff from “unknown sources,” which is another way to say outside the Play Store.
Source: GRIMM Blog
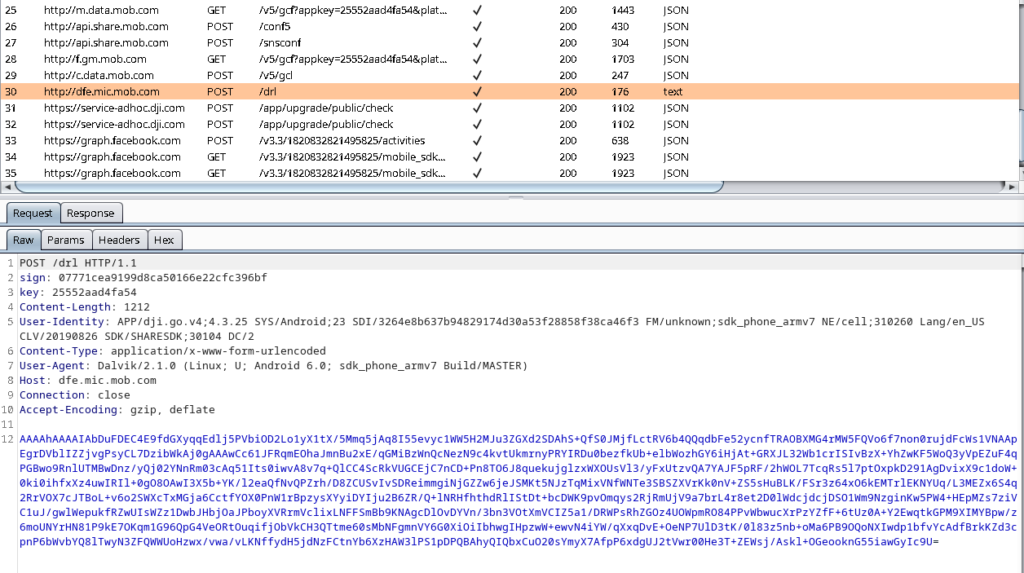
In the current version of the app, this system is abused to download and install the Weibo SDK. In turn, it collects private user data and transmits it to Weibo.
Weibo is a highly popular Chinese social media platform, so there’s a data selling transaction taking place here. Considering that Weibo has failed to adequately protect its users’ data in the recent past, this is not great news for users of the “DJI GO 4” app.
Related: 538 Million Weibo Users’ Data Offered for Purchase on the Dark Web
Source: GRIMM Blog
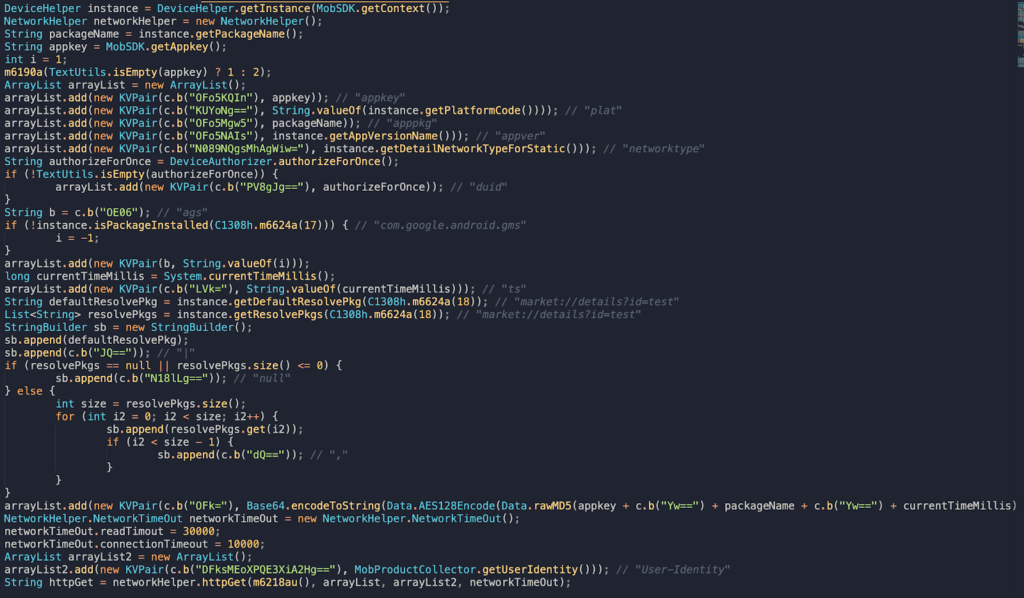
Secondly, DJI’s app was found to contain the Mob SDK until version 4.3.36. This is another component that collected private user information and sent it to a third party. MobTech is a Chinese analytics company, so we have a second data transaction going on here, and one that spreads user data to an even greater number of unknown locations.
Source: GRIMM Blog
Thirdly, the researchers found that it automatically restarts itself as a background process when the application is closed. It then continues to send telemetry data to the entities mentioned above, even when the user (falsely) thinks that the app is no longer active.
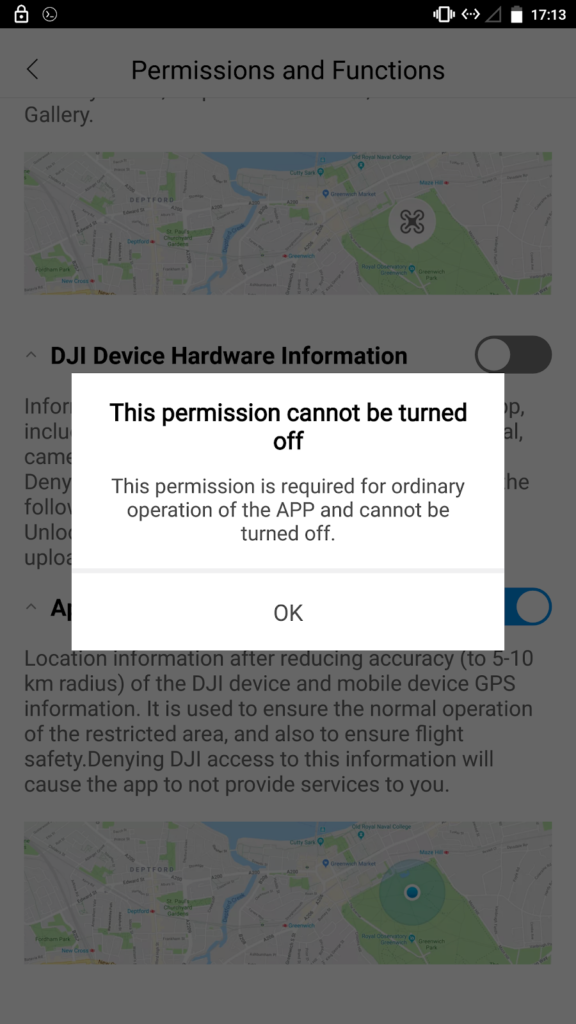
If the user tries to retract the permissions that were provided upon installation, the GO app displays a warning not to do it because the software won’t be able to operate as expected.
Source: GRIMM Blog
DJI products are premium priced, so the company shouldn’t need to sell user data to various third parties. Deciding to do it nonetheless is still their right, but they should have chosen to do it more transparently.
Heavily obfuscating the app’s code to thwart analysis, abusing permission request systems, side-fetching APKs aimed directly to data collection, and running secretly in the background are not acceptable methods for a modern company that pretends to respect its userbase.