Diving Deeper Into the “Hive” Ransomware Modus Operandi
- “Hive” is a new ransomware group that uses a strain written in Go, featuring very fast encryption.
- The payload accepts commands from a remote actor who operates it manually.
- The actors don’t care about who their victims are and simply distribute infection emails everywhere.
“Hive” is one of the most active ransomware groups right now and the actor who is believed to be responsible for the recent attack against dozens of ‘Memorial Health System’ hospitals in the United States. Researchers of the Sentinel Labs have analyzed the group from the aspect of its toolset, ethics, encryption power, and victimization methods, and their report contains juicy details on how the actor moves in the wild. This is valuable because Hive was launched roughly a month ago, so it is a new group that hasn’t seen much light shed onto it yet.
First of all, and as the recent attacks against American hospitals underlined, “Hive” doesn’t have any constraints to prevent it from targeting any facility, even those struggling to keep people in need of emergency treatment alive. Instead, the particular group sends out large volumes of phishing emails without considering which environments are targeted and what the repercussions of down-times could be for society.
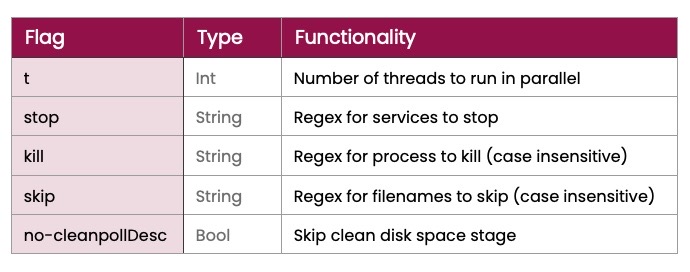
Apart from that, Hive follows a typical approach of operations, including data exfiltration prior to encryption, double extortions, deployment of Cobalt Strike, and the utilization of open source tools for network reconnaissance and credential theft. The ransomware payload itself is a 2MB executable written in Go and packed with UPX. It can take input from the command line, so it runs manually, controlled by a remote actor. The available functions are given in the table below.
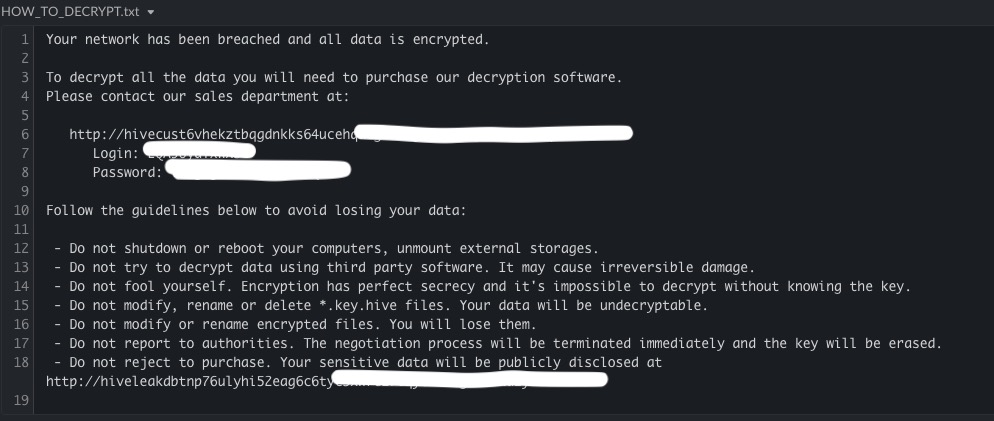
Hive’s ransomware features fast encryption thanks to a scanning and encryption concurrency that derives from the use of Go. The strain first enumerates all drives, including native logical, removable, and remote drives, and then runs “kill” to end linked processes that could jeopardize the encryption process. In the end, it wipes the encryption key from the memory and deletes the shadow copies it created during the encryption process. Finally, a ransom note is planted everywhere except for the “C:\windows” directory.
Dealing with Hive is the same case as dealing with any modern ransomware threat today, so it involves having a solid backup strategy, restricting and monitoring remote access, and using MFA everywhere. Additionally, because the above can’t prevent the double-extortion tactics that typically follow a data breach incident, companies can successfully tackle the ransomware threat only if they stop it at the door - and this can only happen by using state of the art endpoint protection technologies.