Discovery of Zero-Day Bug in “Sign in with Apple” Paid Out $100,000
- A security researcher has figured a way to take over any account based on the “Sign in with Apple” system.
- The hacker realized that he could forge authentication tokens that carry a valid signature and are connected with a specific account.
- According to Apple’s investigation, the discovered zero-day wasn’t being under exploitation in the wild.
Security researcher Bhavuk Jain has published a zero-day vulnerability on “Sign in with Apple,” which he discovered back in April 2020. Apple has paid the man $100,000 for his discovery through its Security Bounty program and has already fixed it on the server-side. The bug could lead to a full email account takeover, so the consequences for the users were dire. This is reflected in the amount of the bounty that was paid to the researcher.
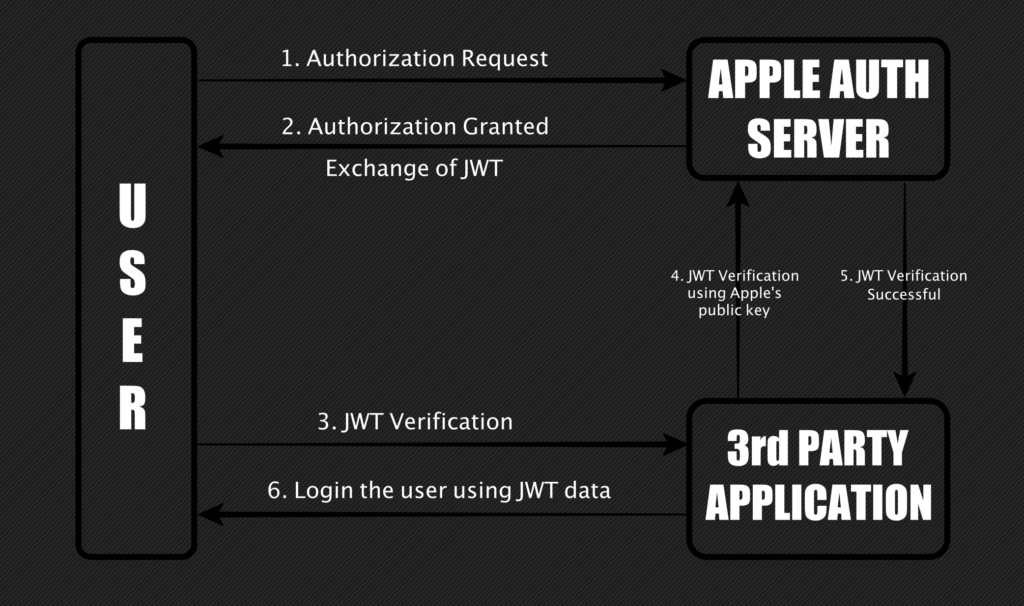
The “Sign in with Apple” user authentication system was introduced by Apple last summer to provide a fully secured and anonymous user ID authentication system based on Open ID Connect and OAuth 2.0. Its purpose is to help users maintain a high level of privacy by using “random” and disposable email addresses that won’t reveal their identities to third-party apps and services, making the persistent tracking of someone practically impossible.
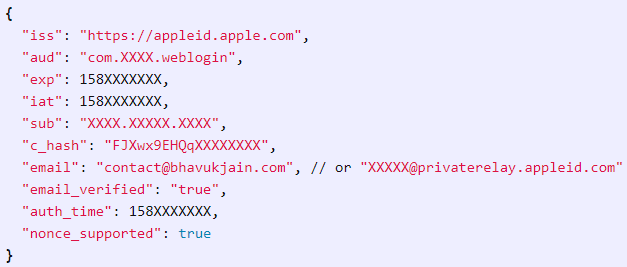
Bhavuk Jain has figured that he could request the JSON Web Token (JWT) that is generated by Apple for any Email ID, allow the signature of the tokens to be verified on the server, and then forge a JWT with the valid signature to access the target’s Email ID account. The JWT is encoded, but apparently, the researcher managed to decode it nonetheless.
Source: Bhavuk Jain Blog
Source: Bhavuk Jain Blog
As the researcher points out, countless third-party apps have already integrated the “Sign in with Apple” system, including Dropbox, Spotify, Airbnb, Giphy, and many more. By exploiting the above vulnerability, an attacker could have potentially taken over the target’s accounts on these services. Apple carried out an internal investigation to figure out if such a thing had already happened, and they confirmed that Bhavuk Jain was the first and only one to discover the bug until the time it got fixed.
Upon the revelation of this seemingly simple exploit, many people rushed to mock Apple’s developers of making a fundamental mistake. Generating JWTs for any account without implementing authentication steps in every step of the process does look like a silly error. Still, almost every vulnerability out there is based on something fairly basic. Nobody has noticed the problem during development and testing of "Sign in with Apple," and it took security researchers almost a full year before they discovered it and claimed the admittedly lucrative bounty. It just proves that "simple" bugs can still hide well and fly under the radar for long.