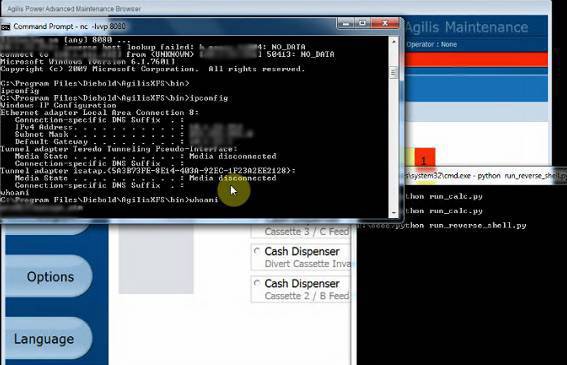
Diebold Nixdorf Warns of Remote Code Execution Vulnerability on Older ATMs
- Older Diebold Nixdorf ATMs running outdated software are vulnerable to RCE attacks.
- The ATMs that carry this flaw are of the Opteva brand and are unlikely to have stayed stagnant for so long.
- The company has released a patch that plugs the flaw by changing the configuration, as well as a securing guide.
Diebold Nixdorf, one of the world’s largest ATM manufacturers with a presence in 130 countries, has announced a vulnerability that plagues their older Opteva-branded ATM machines, allowing remote code execution (RCE) attacks. According to the company’s report, the potential exposure was a part of the Agilis XFS service using .Net remoting over an externally facing HTTP channel, and affects Opterva version 4.x and earlier. The company has released Agilis XFS for Opteva version 4.1.22 that swaps the externally facing HTTP to internal process communication, so the problem can be addressed through an upgrade in the configuration.
To further protect the network communications, Diebold suggests the activation of an adequately configured system/host firewall, the implementation of a TLS connection and a MAC verification layer, and the setting up of a segmented LAN/VLAN with intrusion detection and prevention. Finally, limiting the physical access to the ATM machines is always a crucial part of keeping them secure, so locking the compartment, using two-factor authentication, and conducting frequent visual inspections are also included in the company’s securing guide. Of course, keeping the operating system and all firmware modules up to date and applying any available patches immediately goes without saying.
The particular vulnerability was discovered by a security researcher who contacted Diebold Nixdorf through their standard “Contact Us” form, so it took the company quite a while to get back to him. Once more details were shared with the security experts working for the ATM manufacturer, the company moved on quickly to issue a patch and publish the associated securing guidelines. Moreover, Diebold Nixdorf has clarified that there have been no cases of exploitation and RCE incidents that have been reported to them and that there are practically no banks or institutions that have left their ATM fleet as outdated as required for the vulnerability still to exist out there.
image source: medium.com
The researcher has published a detailed post on how the attack could work against the ATMs, without disclosing the proof of concept code though. If you want to dive deeper into the technical details of the attack, go ahead and check out this Medium post. The publication of this only came after three months have passed since the initial disclosure to Diebold Nixdorf.
Have something to comment on the above? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.