IT Solutions for Dentists Firm Falls Victim to a Ransomware Attack
- A company that was backing up dental documents on its cloud infrastructure has fallen victim of a ransomware attack.
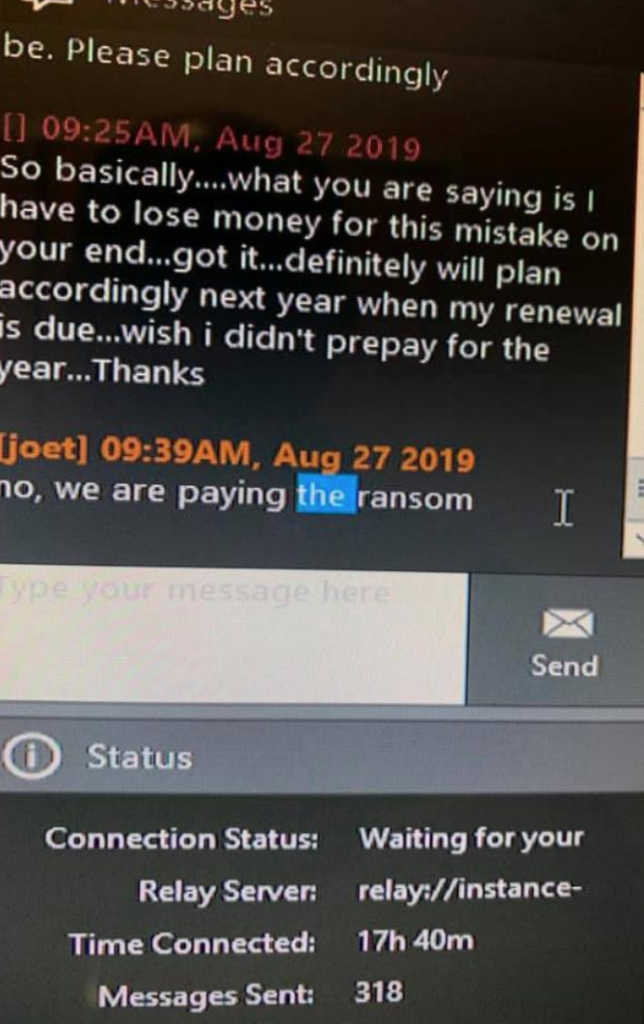
- According to unofficial reports, the firm has already paid the ransom, and they are decrypting the files.
- Dental clinics report that the decryptor is not working reliably and can’t unlock all of the files.
PerCSoft, a Wisconsin-based company that offers IT services and solutions for dental clinics, has fallen victim of a ransomware attack. PerCSoft is the cloud management provider for Digital Dental Record (DDR), a service that helps dental clinics from across the United States to save documents such as medical histories, consent forms, emergency records, customer registrations, screening examinations, and many more. The irony in the story is that these documents are saved on the DDR cloud in order to keep the dental clinics safe in the case of a ransomware attack.
While PerCSoft hasn’t issued an official announcement on the incident yet, some details have been made known through the Wisconsin Dental Association. Brenna Sandler, the director of communications of the association, stated that the ransomware attack actually took place on Monday, August 26, and encrypted thousands of files that correspond to 400 dental practices. The system hasn’t been restored yet, but additional sources close to KrebsOnSecurity have provided more details about what happened. According to the researcher, PerCSoft was struck by an evolved version of Sodinokibi (REvil). Remember, we warned about this new “ransomware as a service” in July, and we will continue to see it being used by malicious actors extensively.
Source: krebsonsecurity.com
According to the same unnamed sources, PerCSoft has paid the ransom and obtained the decryptor, so they are currently helping clients regain access to the locked-down files. As some dental offices report on Facebook, the provided decryptor isn’t working with all of the files, which is something to be expected in cases like this. Others fear that crucial business processes such as the management of the payroll will be impossible to carry out by the end of this month. PerCSoft has informed their clients through Facebook that they are trying to involve more IT firms to help them speed up the process of the systems restoration.
While the amount of the ransom that was paid hasn't been made known, the trend of victims paying them is notable and has also been recorded in several recent studies. As always, paying ransoms is not advised, as this encourages the actors to strike again in the future, and there’s no guarantee that you’ll ever get a decryption key anyway. In this case for example, the provided decryptor isn’t able to unlock all files, so it’s not exactly a reliable tool that PerCSoft paid for.
Would you expect your cloud services provider to pay the ransom, or would you agree to wait for white hat hackers to do it at a later date? Let us know where you stand in the comments down below, or on our socials, on Facebook and Twitter.