Denial Of Service Attack Causes Mozilla Firefox Desktop Versions To Crash
- A security researcher from Wire has developed a JavaScript script that can crash the desktop version of Mozilla Firefox.
- The script can crash the browser when a user visits web pages with JavaScript elements.
- The script can also cause high CPU and memory usage on desktops.
Security researcher Sabri Haddouche, who is a security researcher at Wire has released multiple denial of service scripts that can cause web browsers to freeze or crash. A new exploit created by Haddouche can crash the desktop version of popular browser Mozilla Firefox whenever a user visits a web page with JavaScript enabled.
An IPC channel is flooded between a child process and the main Firefox process on desktops. The script causes the browser to freeze and eventually crash. Haddouche explained the process stating "What happens is that we generate a file (a blob) that contains an extremely long filename and prompt the user to download it every 1ms, therefore it flood the IPC channel between the child and main process, making the browser at the very least freeze."
Image Courtesy of Reaper Bugs
The most telling sign that you may have been affected by the Firefox script is a “Not Responding” screen or a crash. The script can be used to crash multiple variants of Firefox including Quantum, Beta and Nightly builds. However, the script does not work on mobile variants of the browser.
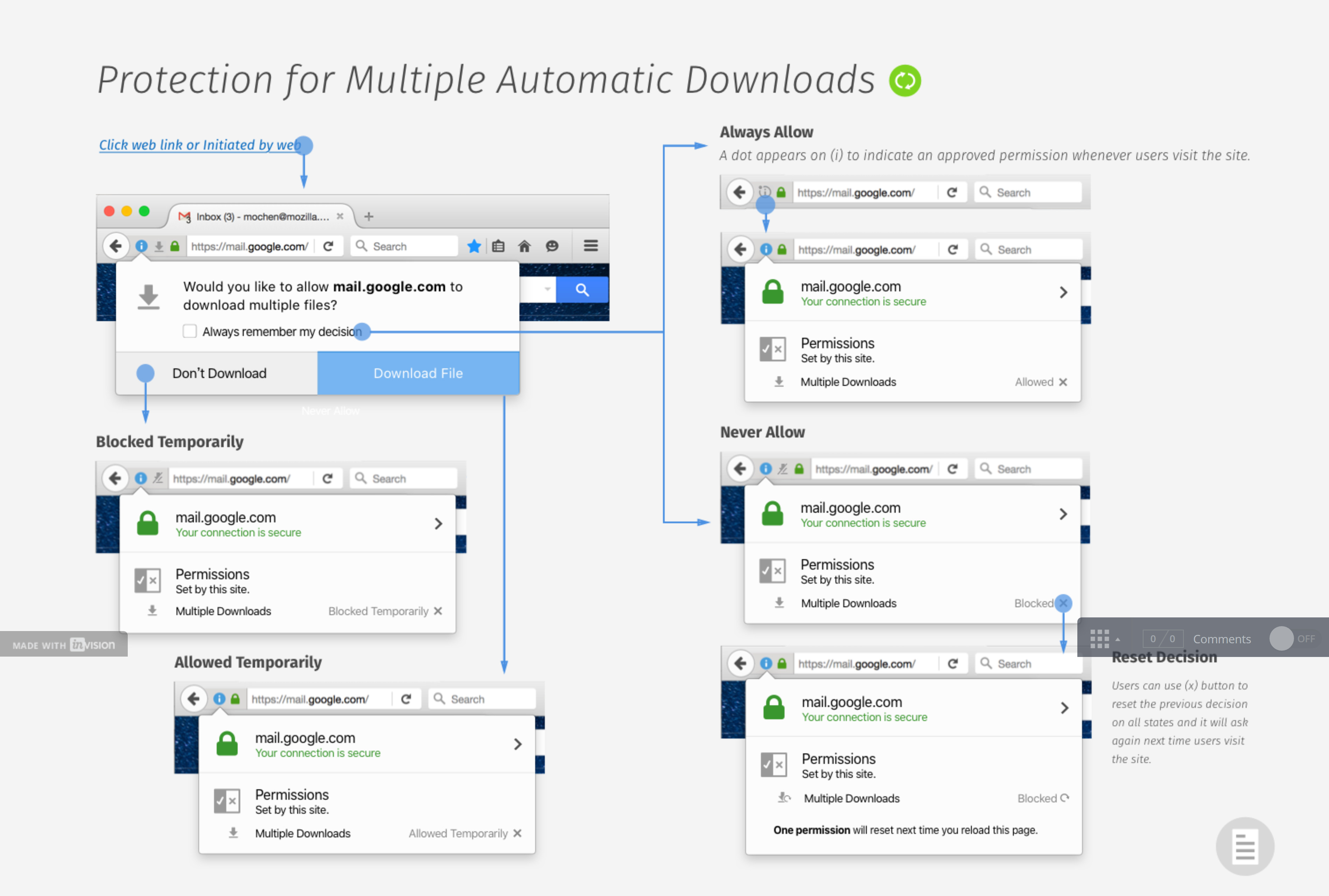
To avoid being affected by the bug users should not allow websites to download multiple files at the same time without the necessary permissions. Going into your browser settings and disabling the option to initiate downloads automatically can solve the issue.
Image Source: Bugzilla
The “Reap Firefox” bug is one of many web browser exploits Haddouche has been working on. His collection of exploits titled “Browser Reaper” can be accessed publicly on his website. Other browsers that he has developed exploits for include Chrome and Safari. Mozilla was at the receiving end of another exploit that allowed add-ons to steal user data last month. It is unknown when Mozilla will be releasing a fix for the bug with the nightly build of their browser still being susceptible to the bug.
What do you think about the browser exploit? Let us know in the comments below. Get instant updates on TechNadu’s Facebook page, or Twitter handle.