Dell Fixes Multiple BIOS Vulnerabilities Affecting Millions of Its Computers
- Tens of millions of Dell computers are vulnerable to arbitrary remote code execution flaws.
- The problem lies in BIOS components that come as part of a software tool that is pre-installed on most Dell machines.
- The flaws will be addressed via a fixing BIOS update that will cover all models until the end of July 2021.
Only about a month after Dell decided to fix a 12-years-old vulnerability in a BIOS driver that was to be found in about 100 million Dell computers, the company is now releasing remediations for multiple security vulnerabilities affecting BIOSConnect and HTTPS Boot. In this case, the scope of affection covers 129 consumer and business laptops, desktops, and tablets, corresponding to roughly 30 million devices. Notably, those protected by superior security systems such as “Secure Book” and “Dell Secured-Core” are also vulnerable.
These are the flaws discovered by Eclypsium researchers and which have compelled Dell to release an urgent mitigation advisory:
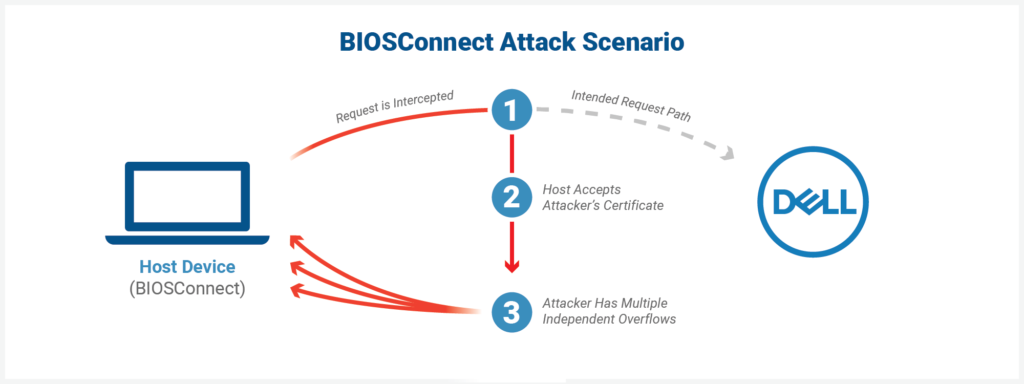
- CVE-2021-21571 – Dell UEFI BIOS HTTPS stack leveraged by the Dell BIOSConnect feature and Dell HTTPS Boot feature contains an improper certificate validation vulnerability. A remote unauthenticated attacker may exploit this vulnerability using a person-in-the-middle attack which may lead to a denial of service and payload tampering. CVSS score: 5.9 and cumulative chain score is 8.3
- CVE-2021-21572, CVE-2021-21573, CVE-2021-21574 – Dell BIOSConnect feature contains a buffer overflow vulnerability. An authenticated malicious admin user with local access to the system may potentially exploit this vulnerability to run arbitrary code and bypass UEFI restrictions. CVSS score: 7.2
The implications of exploiting CVE-2021-21571 include arbitrary remote code execution in the UEFI (pre-boot) environment without any additional prerequisite. This opens up quite a wide spectrum of attack potential, like man-in-the-middle attacks or even full system takeover. The problem lies in the fact that connection requests to the backend Dell HTTP server accept any valid wildcard certificate, so impersonation is made possible after the trivial retrieval of the relevant files.
For a full list of the affected Dell models, check out the company’s advisory as it’s too extensive to share here. BIOSConnect is part of SupportAssist, which comes pre-installed on most Windows-based Dell devices, so the problem is quite extensive.
Dell has promised to roll out fixing patches for all affected models until the end of July 2021, so until then, apply the proposed mitigations. For now, the mitigating recommendation is to update to the latest Dell Client BIOS versions as soon as practically possible. If that’s impossible or if there’s no available update for your model yet, disabling BIOSConnect and HTTPS Boot should do the trick. You may do this through the BIOS Setup Menu, under “Update, Recovery → BIOS Connect”, and “Connection → HTTPS Boot”.