DeepSeek iOS Mobile App Stores and Transmits Unencrypted User Data
- Cybersecurity researchers signaled severe DeepSeek iOS issues that concern user data storage and transmission.
- Among these are unencrypted data transmission, weak and hardcoded encryption keys, and insecure data storage.
- Sending data to China and extensive data collection and fingerprinting are also mentioned.
Severe security and privacy vulnerabilities in the DeepSeek iOS app were highlighted by cybersecurity researchers, each presenting significant threats to organizations and individuals alike. Improper data storage and transmission are among the key findings.
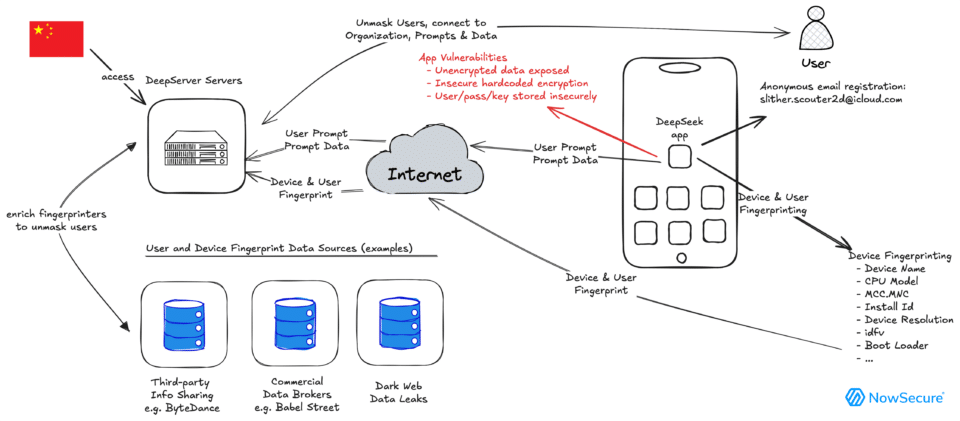
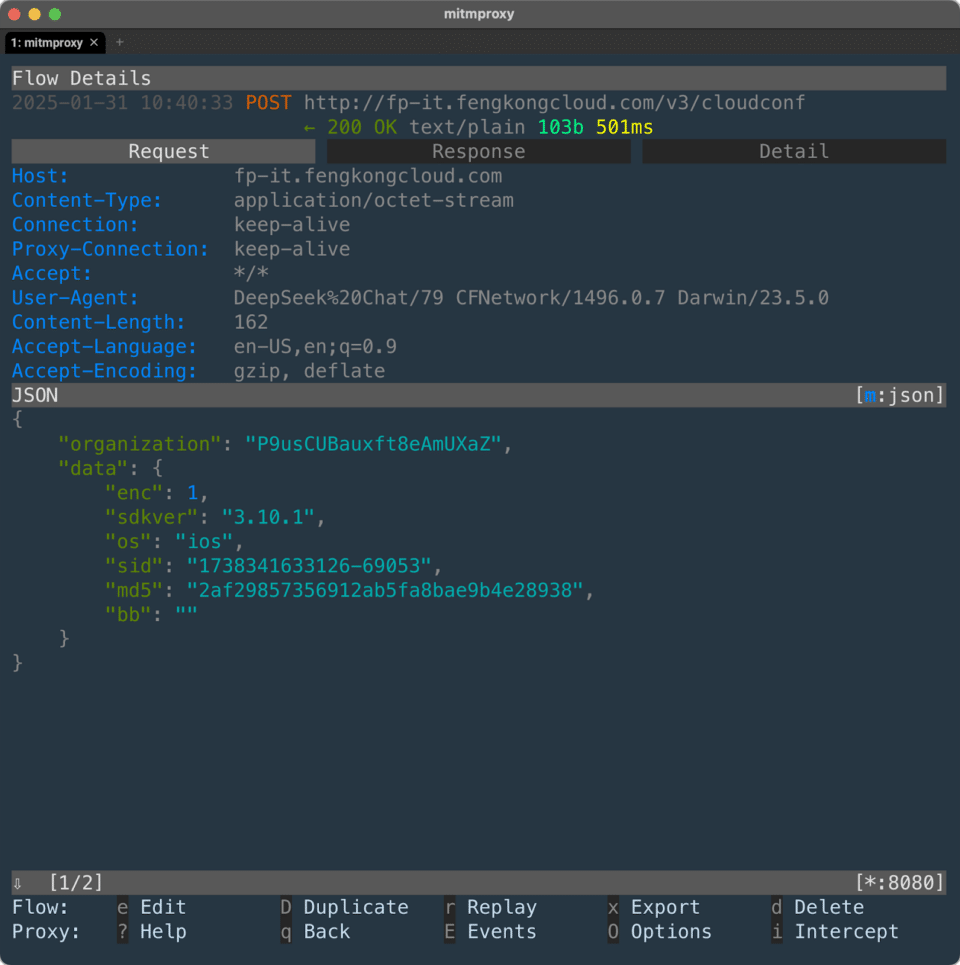
A recent comprehensive assessment by mobile app security firm NowSecure mentions sensitive user data is transmitted over the internet without encryption, leaving it vulnerable to interception and manipulation by attackers, such as in Man-in-the-Middle (MITM) attacks.
The app employs outdated Triple DES encryption, hardcodes encryption keys, and reuses initialization vectors, violating modern security best practices and leaving sensitive data unsecured.
Highly sensitive credentials, such as usernames, passwords, and encryption keys, are stored insecurely, significantly increasing the risk of credential theft.
The app collects considerable user and device data, which could be used for tracking, surveillance, and de-anonymization. User data is transmitted to servers controlled by ByteDance, making it subject to Chinese data privacy regulations, which raises significant compliance and government access issues.
These vulnerabilities create serious risks, including the potential loss of intellectual property, exposure of confidential government and enterprise data, and even regulatory violations due to the storage and processing of data within Chinese jurisdictions.
During initial app launches, the DeepSeek app connects to its backend infrastructure without sufficient protection, further exposing sensitive data to passive surveillance and active tampering.
NowSecure warns that attackers with privileged network access can easily exploit the unencrypted data transmissions of the DeepSeek app, compromising both individuals and organizations.
For instance, recent breaches by Chinese-based threat actor Salt Typhoon have highlighted vulnerabilities in U.S. internet service providers, showcasing the potential for widespread data manipulation and compromise.
The app, which has held the position of the top iOS download since January 25, 2025, has already been installed on millions of devices globally, including those used by enterprise employees and government officials.
These findings have already led to swift bans by multiple countries, federal and state governments, and even the U.S. military to safeguard sensitive data and protect national security.
DeepSeek recently secured a publicly accessible ClickHouse database that granted unauthenticated users access to chat histories, API endpoints and keys, backend details, and other operational information.