‘Decathlon’ Sports Gear Retailer Leaked 123 Million Records Online
- Decathlon Spain and UK exposed employee and customer data, as well as pathways to their network.
- The sportswear retailer was storing data in their cloud systems without using any encryption whatsoever.
- Employees are now running the risk of falling victims to identity theft or phishing actors.
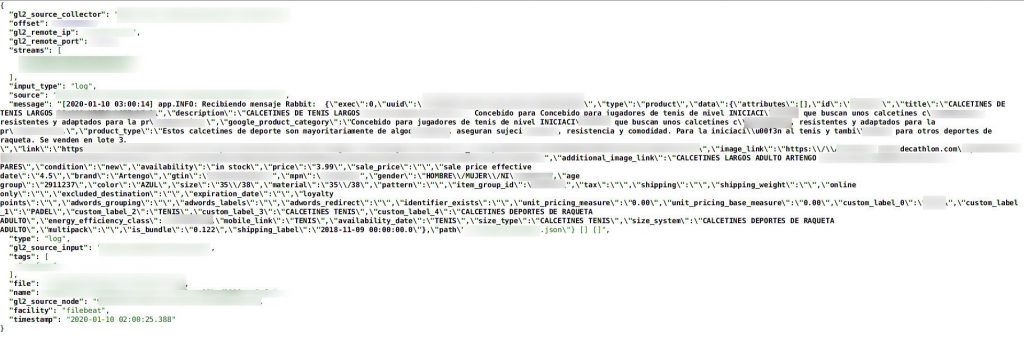
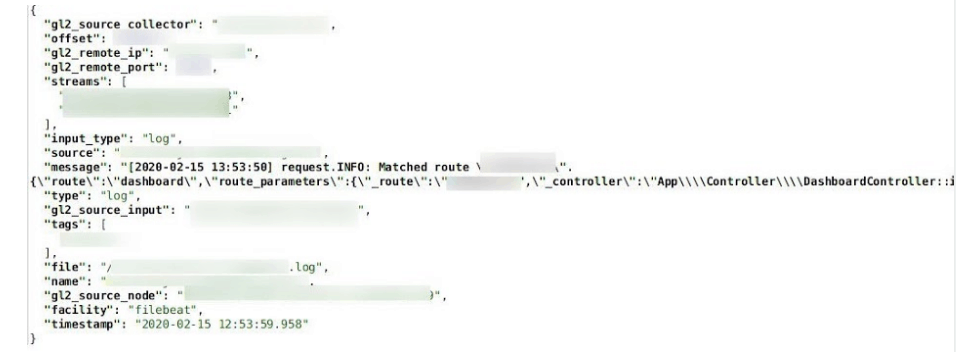
‘Decathlon’, one of the most popular sports gear retailers in Europe, has left an unprotected ElasticSearch server online, leaking 9GB of data comprising of 123 million records. The server reportedly belongs to the Spanish arm of the firm, but it’s possible that data from Decathlon UK are also involved in the security incident. The discovery of the leak was the work of vpnMentor researchers and occurred on February 12, 2020. Decathlon was notified on February 16, 2020, while they secured the database within the following day. Upon analyzing the data, the researchers found out that the following things have been exposed:
- Employee usernames
- Unencrypted passwords
- API logs
- API username and unencrypted password
- PII of employees
- Social security numbers
- Full names
- Nationalities
- Mobile phone numbers
- Full addresses
- Birthdates
- Education
- Work email addresses
- Employment contract information
- Working hours
- Location
- Qualifications
- Contract period
- Roles
- Customer email and login information, unencrypted
- Private IP addresses
Source: vpnMentor
Besides the personal data of employees that have been leaked, Decathlon has the problem of the API details that shouldn’t have been publicly exposed. Especially when these details contain usernames and unencrypted passwords, it is like giving the keys to your network to anyone out there. Using this data, actors could very easily roam inside Decathlon’s systems, access confidential information, check local inventories, dive deeper into the PII (personally identifiable information) of particular employees such as store managers, track down employees or even customers, and eventually threaten their physical safety.
Source: vpnMentor
Those who have been affected by this incident are advised to contact Decathlon and ask about the level of their compromise. If you are a Decathlon employee, the only thing that you can do now is to be aware of the possible consequences of this data exposure. Receiving phishing emails containing valid information is one possibility. Falling victim to identity theft actors is another. Thus, you may want to keep an eye on your bank account activity, as well as to inform friends and family about the chances of them being contacted by someone who makes bold or weird claims about you or while posing as yourself.
Decathlon hasn’t issued an official announcement about the incident yet, although they should inform the customers at least. They blundered by leaving the database unprotected, they demonstrated a lack of basic security practices by storing data in an entirely unencrypted form, and now they are acting unethically by not informing the compromised individuals.