DDoS Attacks Overwhelming Mitigations Through Short and Sharp Doses
- DDoS actors now prefer short, high-volume bursts that can easily overwhelm legacy mitigation systems.
- The attacks last for a few minutes, and then cease for a while before they return, going through this circle for hours.
- Paying the demanded ransom will only secure that the crooks will come back and hit you with the same demands again.
DDoS (distributed denial of service) attacks are a beset for all internet platforms and services, and no matter what mitigation systems are developed to handle them, actors always find something that works against at least some defenses. The most recent trend seems to involve shorter, sharper DDoS attacks that overwhelm protection systems suddenly, instead of building up gradually to mountainous proportions only to see their garbage traffic getting discarded outside the target channels.
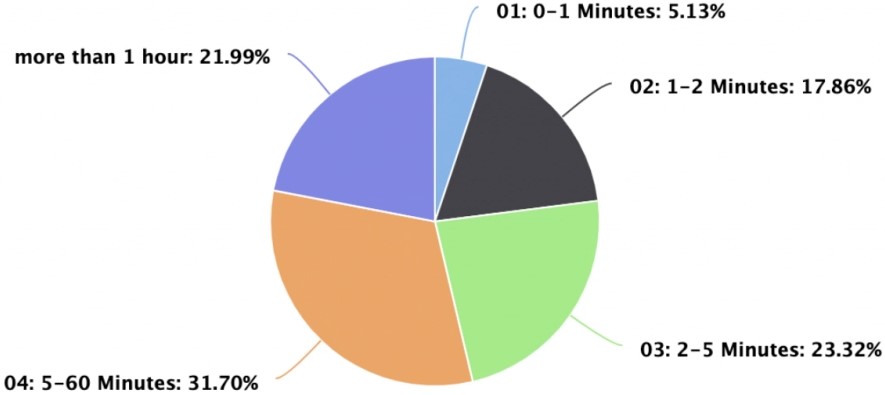
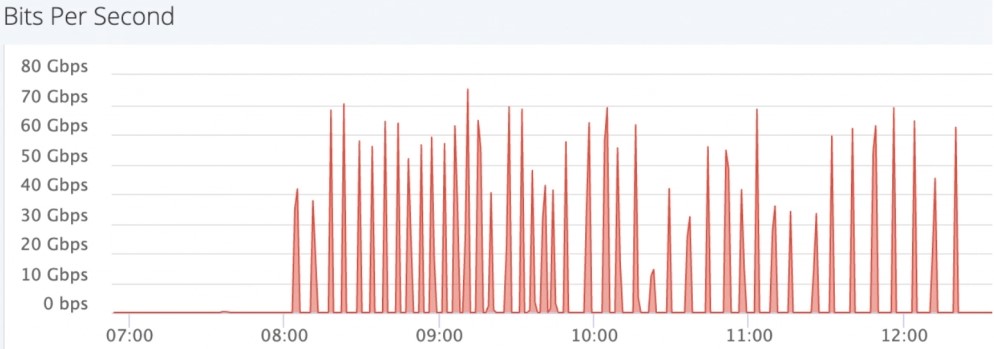
According to an analysis by Imperva, today's DDoS landscape is characterized by short high-volume attacks that last an average of six minutes, with 20% lasting for only 120 seconds. These “pulse” attacks were considered unusual a few years ago, but DDoS actors have found that against modern mitigation systems, they work much better.
Of course, that doesn’t mean that defenders only sustain the attacks for two minutes and then return to normal operational status. The short spikes return every couple of minutes, with the volume spiking suddenly, forcing the mitigation switches to “on” and “off” all the time, causing periodic disruptions that make it impossible for the victim to estimate when the attack will end.
These burst attacks work well against legacy DDoS protection solutions typically configured to ignore short spikes. Unfortunately, and as it is reflected by the trends, there are many entities out there using older and less sophisticated mitigation tools. Also, older systems need some more time to respond to large volume garbage traffic, and this doesn’t really work against these pulses.
The goal is to drive the victim mad with the situation and just have them pay a ransom. Those who pay the ransom, though, will soon discover that they have made the wrong choice, as DDoS actors simply come back for more after some time. The key is to deploy adequate mitigations and shut the door to these crooks, and soon, they will just pick lower-hanging fruit. After all, DDoSing needs resources, time, and effort, so wasting it on a well-shielded entity isn’t usual.