Darknet Marketplace “Joker’s Stash” Evolves Infrastructure and Upgrades Offerings
- The Joker’s Stash now offers PII and SSN entries, as well as a powerful search tool to narrow down results.
- The marketplace calls less sophisticated actors to access its clearnet domains while keeping a smaller set locked for the nastier stuff.
- The operators of the renown marketplace want to cement their position in the darknet market.
According to a report by researchers of the “Insikt Group”, the notorious darknet marketplace known as the “Joker’s Stash” is undergoing an upgrade and evolution phase. First of all, the marketplace is no longer limited to selling stolen credit card data, as the researchers noticed entries that concern personally identifiable information (PII) and Social Security numbers (SSNs). In addition, the operators are expanding the infrastructure of the platform, moving away from Tor and relying on dedicated domains and servers instead.
The Joker’s Stash is already the “go-to place” for malicious actors who have something to sell. That said, it looks like its operators want it to stay on the top, not being afraid of the FBI or other prosecution entities. This moves to the opposite direction of the general trend in the field, as we’ve seen various highly popular darknet marketplaces meeting their end recently, either voluntarily or after coordinated global police operations. The Joker’s Stash seems to be standing in an entirely different place, preparing its infrastructure for a long and prosperous future for itself and its community.
Source: Recorded Future
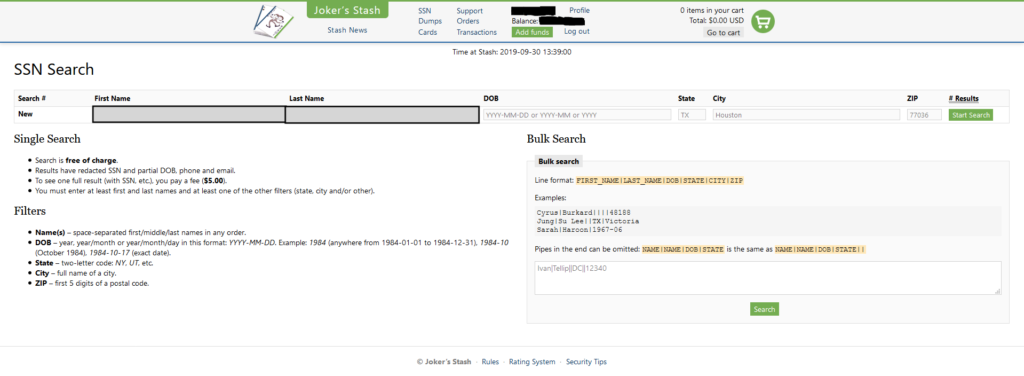
As the researchers point out, the newly added PII and SSNs weren’t randomly sourced. The data concerns members of the White House Cabinet as well as Fortune 500 executives, so we’re talking about high-profile individuals here. Obviously, buying such dumps costs quite a lot, but there’s the capacity to search for a particular entry if you’re interested in a specific individual. The Joker’s Stash can filter SSN entries by location, as they are accompanied by ZIP codes and recent addresses. The search filtering can also help you find specific areas such as “banks”, “retail chains”, “credit unions”, etc. As the reporters point out, this is the first time we see such powerful search tools being incorporated into a darknet shop.
Source: Recorded Future
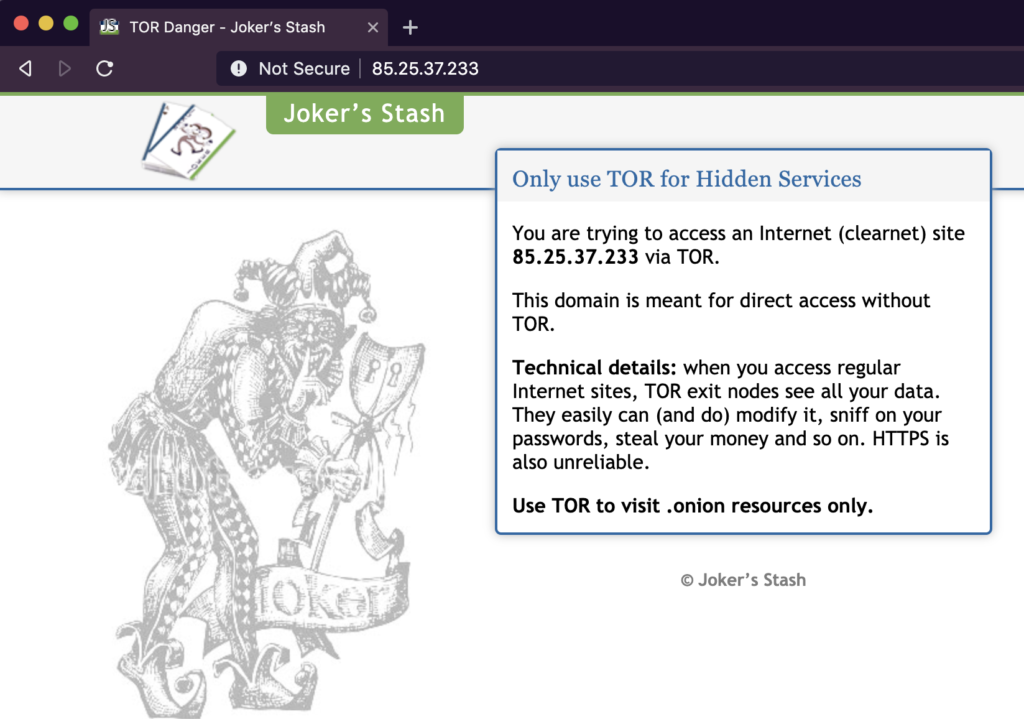
As for the infrastructure, the Insikt Group identified 49 servers and 543 domains that are linked to the Joker’s Stash, but it is very likely that the actual numbers are bigger. As they point out, these domains aren’t malicious, so there’s no risk of getting phished or getting infected with malware. Some domains are only accessible via Blockchain DNS browser extension while others are accessed on the “clearnet”, providing a better service for the lower-grade customers who are the majority anyway. The “locked” domains are probably held for a select clientele who sell much more precious data, but this is just a guess at this point.
Have something to comment on the above? Feel free to share your thoughts with us in the section down below, or join the discussion on our socials, on Facebook and Twitter.