DarkGate Malware Seen in 14,000+ Campaigns After FBI Thwarts Rival QBot
- A surge in the use of the DarkGate malware was observed by security researchers lately.
- The capable malicious tool for ransomware is multifunctional and uses sturdy evasion techniques.
- This observation came after the FBI disrupted the rival QBot malware in August 2023.
A threat actor tracked as 'TA571' is using DarkGate to gain access to 1,000+ organizations worldwide in an attack spanning 14,000 campaigns and containing 1,300+ different malware variants, as a recent Proofpoint report says. This surge in DarkGate use was also observed by Palo Alto Networks Unit 42 security analysts.
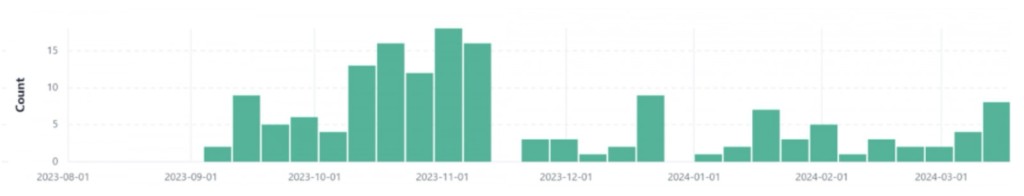
DarkGate was relatively under the radar until 2021, but Unit 42 security researchers say they saw a surge in DarkGate starting in September 2023, right after the FBI took down its botnet and malware loader rival’s infrastructure, QBot (aka Qakbot), one month before.
The recent DarkGate campaigns use AutoIt or AutoHotkey scripts for infection, targeting victims across the U.S., Europe, and significant portions of Asia, and a sixth major version was released in January 2024, identified as version 6.1.6 by Spamhaus.
From March to April 2024, Palo Alto Networks saw a campaign that employed servers running open Samba file shares hosting files for DarkGate infections, with a peak of almost 2,000 samples in one of the days.
The sophisticated DarkGate malware campaign targets Windows machines supported by a reactive Command and Control system and has evolved into a malware-as-a-service (MaaS). It spreads through malicious torrent files, social engineering, phishing emails, compromised websites, and DLL sideloading.
DarkGate malware uses advanced evasion techniques, like code obfuscation, encryption, and anti-debugging measures, and executes multiple payloads, including data exfiltration, cryptocurrency mining, crypto stealing, ransomware, keylogging, credential theft, and remote access.