Anonymous Operating Systems are Perfect for the Dark Web
Every computer, smart TV, laptop, tablet or other modern consumer computing device has an operating system. You're probably aware of the big names such as Windows, Linux, Android, and MacOS.
What does the operating system do? Well, the main clue is in the name. This is the software that operates the device's hardware. It controls what the computer physically does and lets you run software packages on that machine. The operating system also usually includes the interface that you use to send commands and receive feedback. That's how Windows started actually. As a graphical fronted for MS-DOS. The Microsoft Disk Operating System.
Modern operating systems like Windows 10 are incredibly sophisticated and complex. They do far more than just allow basic computer functions to operate. The scope of these systems is growing in such a way, that there are even privacy concerns about them.
OS or Spyware?
How would you feel if a piece of software on your computer was watching you constantly? Keeping logs and then sending them back to the person who wrote it.
Typically we'd call that malware or spyware, but many modern operating systems are now doing it too. This isn't a problem in itself. If the data collection is transparent and it's easy to opt-out that would be OK.
However, in practice, things are more complicated than this. In the case of Windows 10, it's not possible to turn off the built-in "spyware". I don't want to single Windows 10 out, but it's one of the more prominent examples.
The fact of the matter is that any closed-source operating system can have, well, anything programmed into it.
So if you want peace of mind that no deliberate privacy-harming code is in your operating system a good start is to opt for an Open Source OS such as Linux.
Good, But Not Good Enough
While your Open Source OS is unlikely to be spying on you, there's more to it than that. First of all, the typical operating syste m isn't built around the primary goal of protecting your privacy. Sure, Linux is incredibly secure, but it's not designed to keep your identity a secret or clamp down on all possible identifying data.
This is a problem for a couple of reasons. Most importantly, if your computer is seized or hacked into, things like regular operating system logs and other digital breadcrumbs could link you to specific online activities. Ones that you may have wanted to keep private.
If you have accessed potentially frowned upon resources such as Dark Web sites, the last thing you want is for your operating system to gather evidence of this and potentially betray your private activities.
This is where the idea of an anonymous OS comes into play. First, let us see what this term actually means.
What Makes an OS "Anonymous?"
There are two main factors that make an operating system anonymous. The first is that its feature set is geared towards privacy and anonymity. This means that privacy-compromising elements have been stripped out or disabled. Tools for strong privacy have been included and privacy holes have been plugged.
The second thing that makes an OS anonymous is what it does with the information that's private in nature. In general, a private OS will not store any personal information as a rule. It will only do what's needed in order for you to perform tasks such as running a browser or other software tools.
As you might expect, this limits the general usefulness of these OSes. Most private operating systems would be pretty annoying to use as a daily driver. Especially since many of them are designed to leave no traces on the computers they run on.
That's actually a point in their favor though. These operating systems are not designed to leave traces on the host computer. The idea is to boot up the anonymous OS when you need that extra layer of protection and then go back to your vanilla OS when done. That's the idea, but now's a good time to actually look at specific examples.
Popular Anonymous OSes
While there are many takes on the anonymous OS idea, a few names repeatedly come up in the cybersecurity community. These are some of the best-regarded examples.
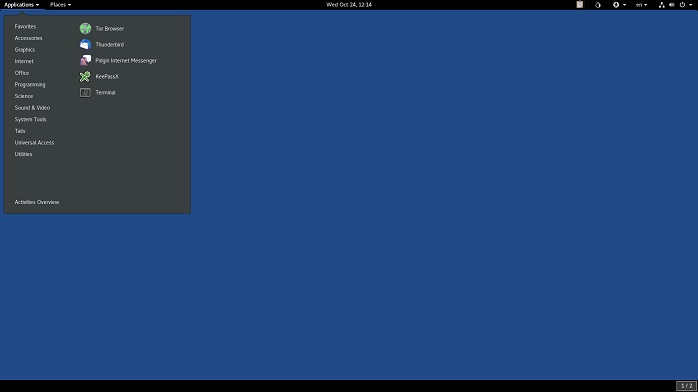
Tails
Image Courtesy of Distrowatch
We singled out Tails as being an especially good choice for Dark Web visitation. The main reason for this is that Tails is a part of the Tor Project. Most of the Dark Web runs on Tor hidden services, so who better to provide an airtight OS for accessing Tor than, well, Tor?
Tails take information security very seriously. If you can't create a copy from an already verified Tails installation, then you have to use a tricky, two-USB drive method of creating a verified copy from scratch. Of course, you can also just boot a disc burned from the ISO, but who has an optical drive anymore?
In the end, however, it's entirely worth it. When you truly want to go incognito you can plug your Tails drive into any computer, boot from it and then do what you need to. After rebooting and taking your drive with you there won't be a single trace left of your activity either on the USB drive or the host computer.
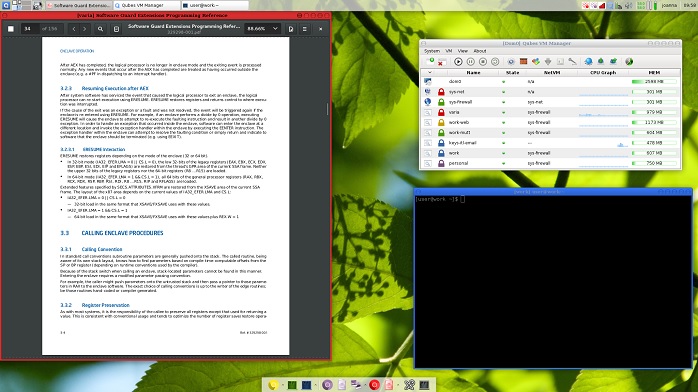
Qubes
Image Courtesy of Qubes
Qubes has the endorsement of none other than Edward Snowden himself. Or, at least, that's what the Qubes home page claims.
The reason Qubes is named Qubes relates to the way in which the OS approaches security. Even with a live OS such as Tails, you still have all the software running in the same environment. So, for argument's sake, if your browser is hacked that may lead to local file access or being able to take remote control of the computer.
With Qubes every activity and process is compartmentalized into a "Qube" of its own. That means if one part of your computer is compromised everything else remains safe. It's a revolutionary approach to computer security and you can use it as your main OS rather than a temporary one.
It Takes a Team to Win
Just remember that, regardless of how cool they are, anonymous OSes aren't good enough by themselves. You need to combine them with common sense, VPN technology, anti-virus software, and other crucial privacy and security tools. There's no magic bullet to protect your identity or data, so strive to strike the right balance.
Have you tried an anonymous OS? Which would you recommend? Let us know in the comments below. Feel safe follow TechNadu on Facebook and Twitter, and join our online community discussions.